Arm your Offensive Security team with tools developed and used by Echelon


Adversarial tactics, techniques and procedures (TTPs) evolve rapidly. At Echelon, our team often creates applications to emulate the same techniques used by today's modern threats. We've made our selection of the best offensive security tools available to the cyber community to help you stay vigilant and secure.
Pigeonhive is a tool for offensive security teams to simulate MFA-defeating social engineering attacks at scale.
It defeats MFA by tricking end users into authenticating on an attacker-controlled server. It creates an unlimited number of hive nodes using containerized browsers sharing their content through VNC. This allows security teams to simulate attacks for large groups of end users, using real login portals for phishing campaigns.

Peekaboo is a Python script that screenshots every service running on port 80 and 443, taking Nmap XML as input. It's a simple and quick alternative to other similar tools. In the HTML results file, the images can be clicked to open the service in a new tab.
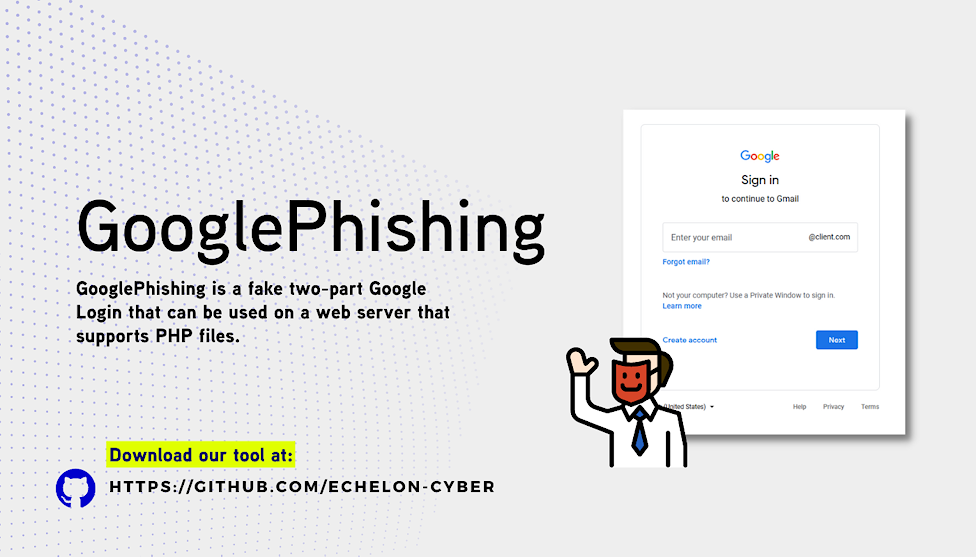
GooglePhishing contains a fake two-part Google Login. It can be used on a web server that supports PHP files. Any entered credentials are saved in /opt/GooglePhishing/creds.txt. The Domain Suffix can be changed from @client.com to any site of your choosing (to do this, just edit line 21 of index.html).

GoogleBITB contains a fake two-part Google Login implemented within a Browser-In-The-Browser attack window. It can be used on a web server that supports PHP files. Any entered credentials are saved in /opt/GoogleBITB/creds.txt. The Domain Suffix can be changed from @client.com to any site of your choosing (to do this, just edit line 21 of login_page.html).
Log4jake is a python script that works by spidering a web application for GET/POST requests. It will then automatically execute the GET/POST requests, filling any discovered parameters with the ${jndi:ldap://:389} Log4j payload. Note that this tool is designed to work simultaneously with a NetCat listener.