Cyber Intelligence Weekly (April 10, 2022): Our Take on Three Things You Need to Know
Welcome to our weekly post where I will be sharing some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
You can also Subscribe to receive Cyber Intelligence Weekly in your inbox each week.
Before we get started on this week’s CIW, I’d like to highlight a great resource that we just launched on our website. Our very own Jake Murphy has been putting out great tips on web application security through this tips and tricks. We’ve compiled some of his top recommendations and tips into this document for you to download for free! Enjoy!

Away we go!
1. US Government Disrupts Russian Government Controlled Botnet
On Wednesday of last week, the Department of Justice announced that it had taken down a significant botnet operation controlled by the Russian Federation’s main intelligence directorate, the GRU.
In their official statement, the Department of Justice announced that they had copied and removed malware from thousands of infected devices, mainly Watchguard firewall devices and some ASUS, that were under the control of the GRU and its hacker squad, known as Sandworm.
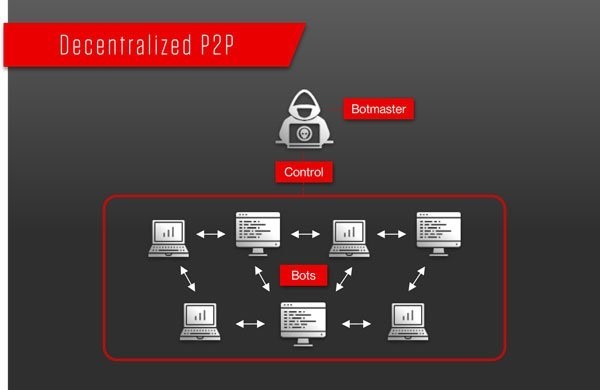
A botnet is a network of computers or devices that is taken over by some vulnerability with malware and that can be controlled centrally by a botmaster. Botnets are then weaponized and used to carry out mass scale attacks. Luckily in this case, it appears the botnet was taken down before they could stage any serious attacks. For more about what a botnet is, see this great article by our partner, CrowdStrike.
In this case, the Russian GRU was controlling the WatchGuard devices with malware known as Cyclops Blink. A thorough breakdown of the Cyclops Blink malware, how it operates, and how to mitigate it, can be found in this great whitepaper released by jointly by the United Kingdom’s National Cyber Security Centre, the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency, the FBI, and the National Security Agency.
This is yet another reminder of why security in the supply chain is such an important matter.
2. German Federal Police Shut Down Russia’s Dark Web Market, Hydra
On Tuesday of last week, federal law enforcement in Germany scored a major win by seizing the server infrastructure in Germany of the world’s largest online illegal darknet marketplace dubbed “Hydra Market.” Bitcoin totaling around $23 million Euro were also seized as part of the arrest.
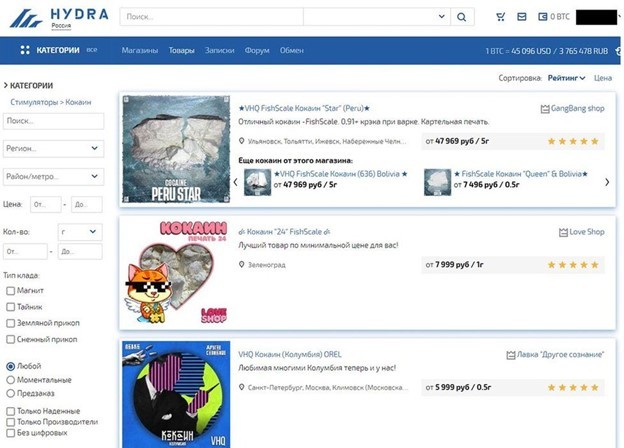
The operation was a join one between the German Federal Police (BKA), FBI, DEA, IRS Criminal Investigations, and Homeland Security Investigations in the US. It has been reported that the Hydra market facilitated more than $5 billion dollars in illicit cryptocurrency transactions since the site started in 2015.
Hydra had another very big role that it has been playing in addition to a market for illicit goods, and that is the role of facilitating money laundering. According to crypto analysis firm, Chainalysis, Hydra received $645 million worth of cryptocurrency from illicit sources (darknet markets, wallets with stolen funds, ransomware operators, etc.) since 2020.
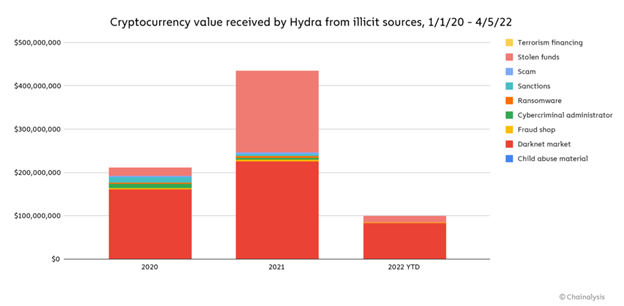
This disruption in the money laundering ecosystem for criminals is one that is worth watching. Will it dissuade more criminals from launching attacks in the first place, or will it be business as usual? Only time will tell.
3. Block Says Former Worker Accessed U.S. Customer Data Without Approval
In what has been a wild few weeks for insider threat discussions, more bad news came out last week, this time it was Block, Inc. that was the victim. In an SEC filing, Block explains that a former employee downloaded reports of its subsidiary, Cash App, that contained U.S. customer information.

The SEC filing notes that the reports included full name, brokerage account numbers, portfolio values, brokerage portfolio holdings and potentially stock trading activity for one trading day. The reports supposedly did not contain usernames, passwords, SSNs, date of birth, or any other highly sensitive personal information. The filing also noted that they would be notifying nearly 8.2 million current and former customers about the incident.
Identity and access management is such a critical function for any business, and this is a reminder of how lingering user access to internal company data can be so harmful.
Thanks for reading! Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more point solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
