Cyber Intelligence Weekly (April 17, 2022): Our Take on Three Things You Need to Know
Welcome to our weekly post where I will be sharing some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
You can also Subscribe to receive Cyber Intelligence Weekly in your inbox each week.
Before we get started on this week’s CIW, I’d like to highlight a wonderful article by our very own Chereese Langley, where she highlights the risks of insider threats and why these risks should quickly become the most relevant for many organizations across the globe. As the threat landscape quickly evolves, we will always bring our unique insights like this to our loyal readers. Enjoy!
Away we go!
1. Feds Uncover a ‘Swiss Army Knife’ for Hacking Industrial Control Systems
The big story of this past week, was undoubtedly the report about the new toolsets and capabilities for industrial systems hacking discovered by federal law enforcement. The Department of Energy (DOE), the Cybersecurity and Infrastructure Security Agency (CISA), the National Security Agency (NSA), and the Federal Bureau of Investigation (FBI) jointly released a cybersecurity advisory to warn about that certain advanced persistent threats have exhibited new capabilities that enable them to gain full system access to several popular industrial control system (ICS), supervisory control and data acquisition (SCADA) devices.
The specific manufacturer devices called out by the CISA warning include:
- Schneider Electric programmable logic controllers (PLCs)
- OMRON Sysmac NEX PLCs
- Open Platform Communications Unified Architecture (OPC UA) servers

These ICS and SCADA systems are designed to act as intermediaries between modern computing systems and machinery and sensors within industrial environments. A detailed report by Dragos on the malware and how it operates, can be found here. Dragos dubs the tool, “PIPEDREAM” and they mention in their report that while specific PLC manufacturers were initially called out in the CISA advisory, the PIPEDREAM malware actually attacks vulnerabilities in the underlying code of such systems, CODESYS.
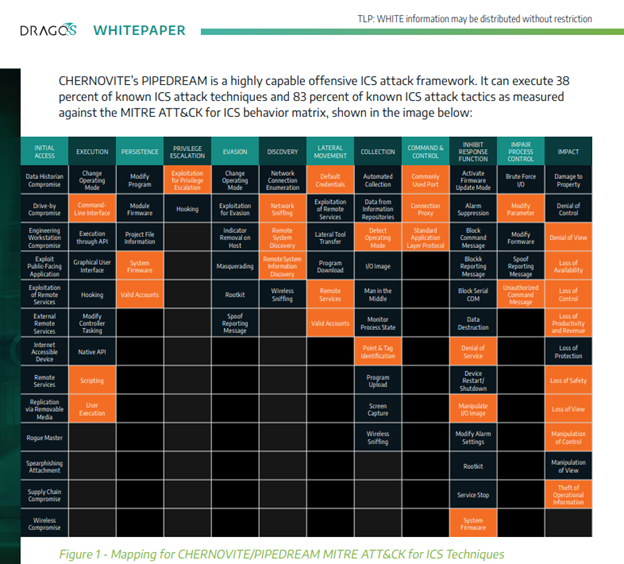
The Dragos whitepaper on PIPEDREAM outlines the full capability set of the malware across the MITRE ATT&CK framework specific to ICS technologies. The MITRE ATT&CK framework is a good benchmark and classification system for threat actors tactics, techniques and procedures (TTPs). As you can see above, the PIPEDREAM toolset has a number of capabilities that makes it one of the most diverse and capability rich ICS specific toolsets ever discovered. That fact, in and of iteself, is a disturbing one. This means that there are significant means and motivations behind the creation of such a malware framework.
The CISA and Dragos reports both outline a number of great risk mitigation techniques to combat this new malware framework. Some of the recommendations include good cyber hygience items like:
- Monitoring east-west ICS/SCADA network traffic
- Changing default credentials on PLCs and other devices on the network
- Hardening systems by restricting access to targeted ports for malware operation
- Maintain good offline backups for faster recovery upon attack
- Enforce the principle of least privilege across ICS/SCADA networks, firmware and devices
- Isolate ICS/SCADA networks from corporate networks wherever possible
2. Widely Used Autonomous Hospital Robots at Risk of Remote Hijacking
Sticking to the device theme for today, we have a scary story about major flaws that could allow a hospital robot to be remote commandeered. Cynerio, a healthcare IoT company, found a series of serious vulnerabilities in Aethon Tug hospital robots that allowed them to take over the robot which could allow attackers to remotely surveil or interact with patients, tamper with medical distribution, and disrupt day-to-day operations. The ICS-CERT Advisory can be found here.

Cynerio has dubbed the five zero-day vulnerabilities as JekyllBot:5. The Aethon Tug is commonly used in hundreds of hospitals to deliver medication, perform cleaning and transport supplies. The issues found had to do with the TUG Homebase Server’s JavaScript and API implementation, and a WebSocket.
Asher Brass, lead researcher on the JekyllBot:5 vulnerabilities and Head of Cyber Network Analysis at Cynerio has this to say on their blog, “These zero-day vulnerabilities required a very low skill set for exploitation, no special privileges, and no user interaction to be successfully leveraged in an attack. If attackers were able to exploit JekyllBot:5, they could have completely taken over system control, gained access to real-time camera feeds and device data, and wreaked havoc and destruction at hospitals using the robots.”
The intersection of the cyber and physical world’s keep getting closer and closer, which means the stakes keep getting raised higher and higher to ensure these devices and the patients who interact with them are safe. Kudos to the researchers who uncovered these issues along with the Coordinated Vulnerability Disclosure (CVD) process put in place by CISA to help coordinate and manage the disclosure and remediation of serious vulnerabilities such as these.
3. Mirai Malware Leveraging Spring4Shell Exploits for Botnet Delivery
Just when we thought we’d heard the last of the Mirai botnet, it seems to have new life. Threat researchers from Trend Micro have reported that they have observed active exploitation of the relatively new Spring4Shell vulnerability, allowing malicious actors to weaponize and execute the Mirai botnet malware.

The initial exploitation attempts that have been observed were focused on vulnerable web servers in the Singapore region. Some have postulated that these initial exploits are a localized testing ground before launching a much broader campaign worldwide.
Botnet operators are always looking for low hanging fruit to grow their botnet operations, and scale them up. System admins need to focus on upgrading the Spring Framework to help keep these and other threat actors at bay.
Thanks for reading! Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more point solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
