Cyber Intelligence Weekly (April 30, 2023): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Before we get started on this week’s CIW, I’d like to highlight a new article of mine where I explore the benefits of adversarial-based red teaming with the TIBER-EU Framework, a comprehensive methodology developed by the European Central Bank. In this article, I describe the key differences between traditional penetration testing and adversarial-based red teaming, the components of the TIBER-EU Framework, and recommendations for implementing this approach.
Read the full article here: https://lnkd.in/giC3_pwi

Away we go!
1. NIST Releases New Discussion Draft of the Cybersecurity Framework 2.0 Core
The changes proposed in the new NIST discussion draft for the cyber framework update are significant. First off, it’s important to note that this discussion document is not a final draft of the CSF 2.0. It is a discussion document highlighting several structural changes ahead, as well as providing several examples of the changes. A final draft of CSF 2.0 will be released later in the summer of 2023.
Most notably, the proposed CSF 2.0 Core Functions, Categories, and Subcategories are included in a detailed matrix comparing the CSF 1.1 and CSF 2.0 tables. A quick scan of this will show you where the net new items are.
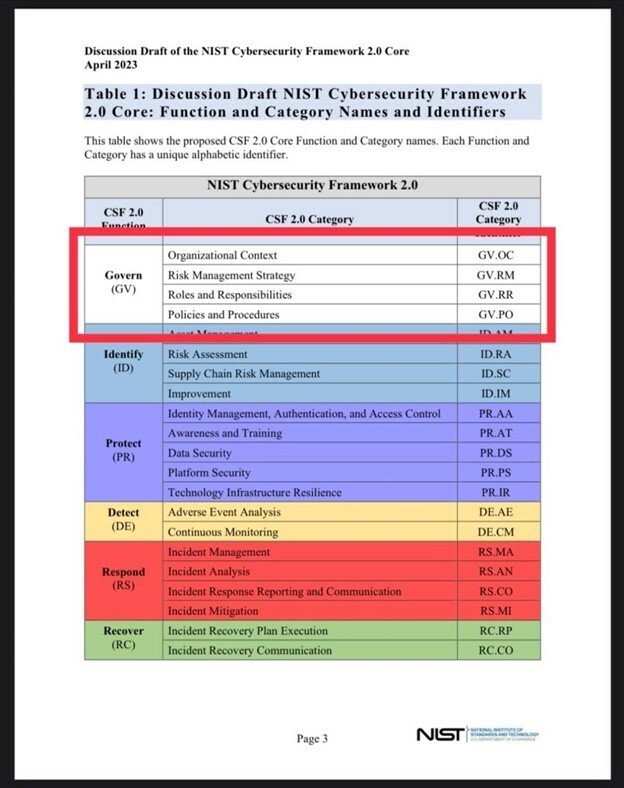
There are several other notable takeaways. There is:
- A new Function, “Govern (GV)”, which steals some categories and subcategories from other Functions as well as adding some net new.
- A renewed vigor within “Identity” surrounding cybersecurity supply chain risk management outcomes.
- A new “Improvement” Category in the Identify Function which includes a new subcategory surrounding continuous evaluation, including through reviews, audits, and assessments (including self-assessments).
- A new Category, “Technology Infrastructure Resilience” with a deeper focus on, well, resilience!
- A new column(!) with proposed new CSF 2.0 Core Implementation Examples which are intended to provide notional implementation examples of concise, action-oriented steps to help achieve the outcomes of the framework.
The implementation examples are the biggest game changer of the proposed CSF 2.0 changes in my opinion. These implementation examples will provide the initiated with concrete ideas of how they might achieve the outcomes they desire through detailed examples.
Implementation Example Sample:
CSF 2.0 Subcategory, ID.RA-01: Vulnerabilities in first-party and third-party assets are identified, validated, and recorded.
CSF 2.0 Implementation Examples, ID.RA-01:
- Example 1: Vulnerability scans are performed to identify unpatched and misconfigured software
- Example 2: Network and system architectures are assessed for design and implementation weaknesses affecting confidentiality, integrity, availability, and resilience
- Example 3: The authenticity and cybersecurity of critical technology products and services is assessed prior to acquisition and use
- Example 4: Software developed by the organization is reviewed, analyzed, or tested to identify vulnerabilities
- Example 5: Facilities housing critical computing assets are assessed for physical vulnerabilities
2. SolarWinds Hack Discovered 6 Months Earlier Than First Disclosed
According to a recent report by Kim Zetter at Wired, the US Department of Justice (DOJ), Mandiant, and Microsoft discovered the SolarWinds breach six months earlier than previously reported, in May 2020. However, at that time they were seemingly unaware of the significance of what they had found. As a refresher, the breach involved Russian hackers compromising the software maker SolarWinds and inserting a backdoor into software that it had served to about 18,000 of its customers, including several US federal agencies.
The DOJ detected unusual traffic emanating from one of its servers that was running a trial version of the Orion software suite made by SolarWinds. Suspecting a breach, it engaged Mandiant and Microsoft for an investigation. Investigators suspected the hackers had breached the DOJ server directly, possibly by exploiting a vulnerability in the Orion software, but they reached out to SolarWinds to assist with the inquiry, and communication between investigators and SolarWinds stopped in July 2020 after SolarWinds engineers couldn’t find any vulnerabilities in their code.

In November 2020, months after the DOJ completed the mitigation of its breach, Mandiant discovered that it had been hacked and traced its own breach to the Orion software on one of its servers the following month. It was finally revealed by Mandiant in December 2020 that the hackers had embedded a backdoor in the Orion software while it was being compiled by SolarWinds in February 2020. The tainted software went out to about 18,000 SolarWinds customers, who downloaded it between March and June.
This news further illustrates the need for robust information sharing, especially for an incident that is as serious as a supply chain breach of government entities. Furthermore, the fact that these details were kept hidden for years after the breach makes it seem as if the agencies had something to hide.
3. Salesforce Community Misconfigurations Lead to Widespread Data Leaks
According to a new report from Brian Krebs, numerous organizations, including banks and healthcare providers, have been exposing private and sensitive information via their public Salesforce Community websites due to misconfigurations in the platform. Salesforce Community is a popular SaaS product that makes it easy for organizations to quickly create websites.
The confirmed issue within Salesforce Community allows unauthenticated users to access records that should only be available after logging in. While there is a guest access feature allowing unauthenticated users to view specific content and resources without logging in, administrators often grant guest access to internal resources, which can lead to potential data leaks. Several organizations have had confirmed instances of data exposure, causing them to investigate and fix their Salesforce Community sites.

A security researcher found the vulnerability in the Salesforce Community sites and developed a program to identify hundreds of other organizations that are also running misconfigured Salesforce pages. The researcher has since notified several organizations, including government organizations and companies, about the problem, with little response.
According to Salesforce, the data exposures can happen when customers' access control permissions are incorrectly established but are not due to a flaw in the Salesforce platform itself. Salesforce advises customers to use its Guest User Access Report Package to review access control permissions for unauthenticated users and to review best practices and considerations when configuring the Guest User Profile.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
