Cyber Intelligence Weekly (August 21, 2022): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Also, we are always looking for great people to join our team. If you know anyone who fits the profiles for any of our open positions, drop me a line and let me know!
Before we get started on this week’s CIW, I’d like to highlight our team’s recent success at DEF CON 30! Our team won the prestigious DEF CON Black Badge. The DEF CON Black Badge is one of the pinnacles of achievement in the profession of cybersecurity. Per the DEF CON site “A Black Badge is one of the highest honors that DEF CON can bestow on a person or team in recognition of their overall elite skills or outstanding contribution to the security community.” These four gents now get to attend DEF CON for free for the remainder of their natural lives! Way to go TEAM ECHELON!!!


Away we go!
1. TikTok’s Built-In Browser Can Log Keystrokes, Researcher Says
When using your favorite mobile application, you may have noticed that many popular mobile apps have their own in-app browsers. Rather than re-directing the user outside of the mobile app to the native browser on the device, the app uses its own custom built browser within the app itself so that the user does not leave the app.
New research from developer Felix Krause recently showed the security and privacy risks of these in-app browsers, as it gives the app developers more control over your browsing experience. Most notably, he calls out potential big risks with TikTok and their in-app browser. When opening any website in the TikTok mobile app, Krause notes that it injects tracking code that can monitor all keystrokes, including passwords, and all taps.
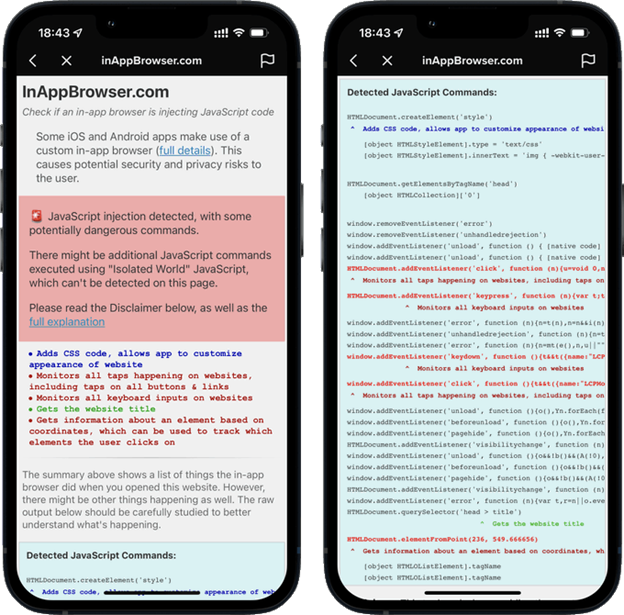
Per a Forbes article on this matter, TikTok pushed back on the notion that they track user’s activities and private data. They noted that the JavaScript in question is used only for debugging, troubleshooting and performance monitoring. Regardless of what the company says, exercising caution when using an in-app browser, for any app, seems like a strong security move.
2. Lloyd’s of London to Exclude State-Backed Cyber Attacks from all Coverage
Lloyd’s of London Ltd. is an insurance marketplace where nearly 75 syndicates of underwriters go to provide insurance coverage for businesses. In a recent market bulletin from Lloyd’s of London, they stated to their syndicates that they must include language in all new policies that exclude state based attacks. The bulletin notes that state-based attacks, their ability to spread, and the damage they can cause may create systemic risk to insurers.
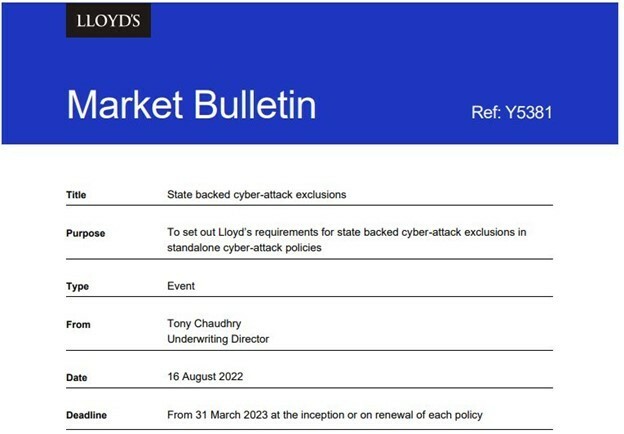
It is clear that the cybersecurity insurance market is going through a period of readjustment as insurers want to limit their losses from large cyber catastrophes. But in this case, how are we supposed to clear the attack attribution hurdles? Figuring out who is behind a certain cyber attack is a very difficult task in nearly every case. Then you have the problem of a criminal group who is maybe acting in support of their country rather than on behalf of their country, which is a real distinction. These types of exclusions really limit the overall usefulness and protection of the coverages as a whole. It will be interesting to see how the market reacts to these changes.
3. 1,900 Signal User’s Numbers Exposed Due to Twilio Breach
Twilio announced a breach last week, that affected approximately 125 customers. Twilio, a public company based in San Francisco, provides programmable communication tools for making and receiving phone calls, sending and receiving text messages, and performing other communication functions using its web service APIs. Per their blog post, some Twilio employees were tricked into giving up their credentials through advanced phishing techniques and then the threat actors were able to gain access to certain internal Twilio systems and the ability to read Twilio SMS messages as well.
Of note, Twilio provides phone number verification services through SMS text for the popular encrypted messaging app, Signal. Basically, whenever a user registers their phone number with Signal, they will receive an SMS through Twilio with a verification code that they enter into the Signal app. When the hackers gained access to Twilio’s systems, they gained access to the phone numbers and/or the SMS verification codes for approximately 1,900 Signal users.
During their window of access to Twilio’s systems, the threat actors had the ability to register these phone numbers to another device. Essentially, this would allow the threat actors to impersonate that individual Signal user, although they would not have access to their contacts, message history or profile information. Luckily, through Signal’s privacy policies, all of that information remains locally on the user side app only.
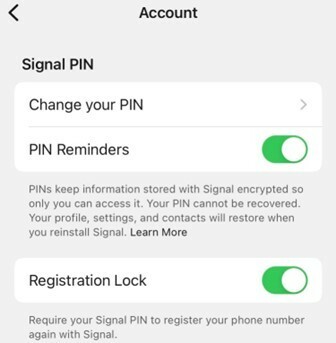
A blog post from Signal noted that of the 1,900 phone numbers accessed, the attackers explicitly searched for three numbers, one of them was linked to cyber journalist at Vice News, Lorenzo Franceschi-Bicchierai. He chronicled the takeover of his Signal account in his most recent story. One of the major takeaways for Signal users here is to enable their “Registration Lock” feature. By enabling registration lock, it adds another layer of security to the registration process for Signal, requiring your secret PIN to be entered.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
