Cyber Intelligence Weekly (Dec 5, 2021): Our Take on Three Things You Need to Know
Welcome to our weekly post where I will be sharing some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
You can also Subscribe to receive Cyber Intelligence Weekly in your inbox each week.
Lastly, we are always looking for great people to join our team. If you know anyone who fits the profiles for any of our open positions, drop me a line and let me know!
Before we get started on this week’s CIW, I’d like to highlight this great YouTube channel from my friend Christophe Foulon. Chris is passionate about helping others get into the field of cybersecurity and has made a YouTube channel filled with great content to help others break into the industry. Please consider subscribing and giving Chris a follow! Thanks for all you do for this industry Chris!

Away we go!
1. Former Ubiquiti Developer Charged by FBI for Extorting His Employer
Last week, a Department of Justice indictment was unsealed that revealed Nickolas Sharp at the center of a wild story surrounding a massive data breach at technology vendor Ubiquiti. If you recall from earlier this year, Ubiquiti was the center of attention regarding a major breach that was brought to light from through an anonymous whistleblower.
This ‘whistleblower’ reached out to tell his story, which was reported on by Brian Krebs in March of this year. Damian Williams, the United States Attorney for the Southern District of New York, and Michael J. Driscoll, Assistant Director-in-Charge of the New York Office of the Federal Bureau of Investigation believe that Nickolas Sharp was the one posing as the whistleblower.
The press release from the indictment notes, “Sharp subsequently re-victimized his employer by causing the publication of misleading news articles about the company’s handling of the breach that he perpetrated, which were followed by a significant drop in the company’s share price associated with the loss of billions of dollars in its market capitalization.”

The indictment alleges that Sharp had access to the organization’s AWS and GitHub accounts, from which he stole vast amounts of proprietary information from Ubiquiti. The indictment also states that throughout this mischievous process, Sharp tried hiding his home IP address using Surfshark's VPN services. However, his actual location was exposed after a temporary Internet outage. Also, in an effort to further obfuscate his malicious activity, Sharp altered log retention policies and other files that would have exposed his identity during the subsequent incident investigation.
In January of this year, while working on a team remediating the effects of the incident, the indictment alleges that Sharp sent a ransom note, effectively posing as an anonymous attacker who claimed to have obtained unauthorized access to the organization’s computer networks. He then demanded 50 Bitcoin (25 to delete the stolen data and 25 to remove any backdoors) settle the matter.
Sharp is charged with four counts and is facing a maximum sentence of 37 years in prison if found guilty. This is a case study for examining and taking insider threat seriously if I ever heard one!
2. NSO Group Tools Used to Target U.S. and Other Officials in Uganda
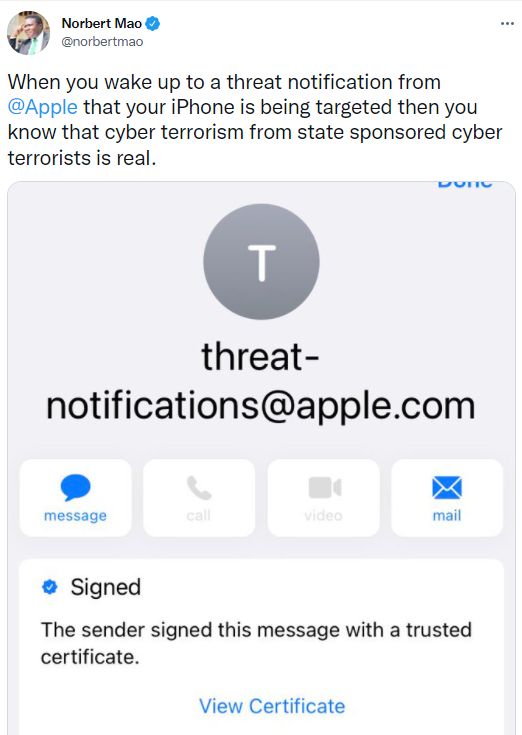
The NSO Group is in the news again, a week after we mentioned Apple was suing the NSO Group for allegedly hacking its customers on a regular basis. In a report from the Washington Post, they note that Apple has alerted 11 U.S. Embassy employees that their iPhones have been hacked in recent months with the Pegasus spyware from the NSO group.
These hacks reportedly were of embassy employees at the U.S. Embassy in Uganda and at least some of the hacked employees were U.S. citizens working as Foreign Services officers. These hacks appear to have used the “FORCEDENTRY” exploit against phones that have not been patched.
Who was behind the attacks that used the NSO Group’s software remains unknown at this time. Here is a tweet from Norbert Mao, President of the Democratic Party of Uganda. At this rate, we should have a special section in this newsletter for the NSO Group and stories related to use/misuse of its spyware.
3. Hackers Are Spamming Businesses’ Receipt Printers With ‘Antiwork’ Manifestos
Insecure business receipt printers are supposedly being targeted by someone who is blasting ‘Antiwork’ manifestos to them. Reports have been flooding Reddit and Twitter about these types of messages that are popping up all over the place on retail receipt printers.
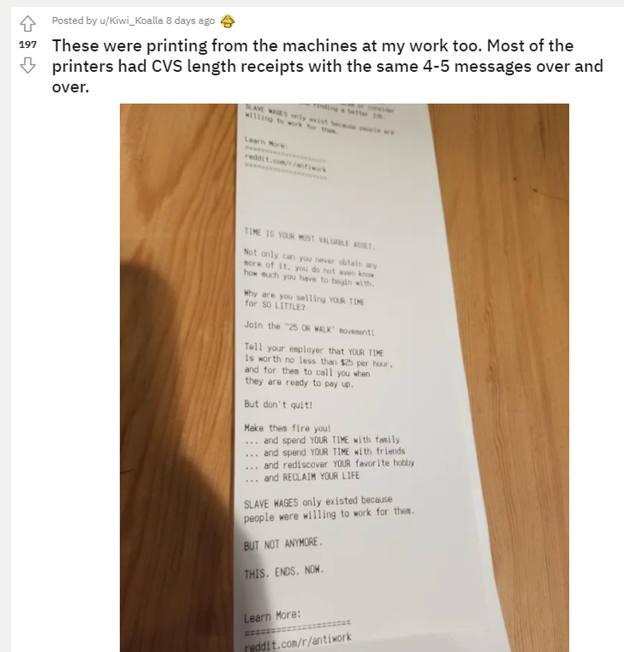
A Motherboard story on the topic cites Andrew Morris, the founder of GreyNoise in the matter. They have looked into the events and they do see network traffic going to insecure receipt printers all over the internet. Whomever is behind this is blasting workers rights messages to thousands of printers that are exposed around the world.
I have seen large corporations struggle with locking down ancillary devices, changing default credentials, etc. I can imagine just how difficult this would be for mom and pop retailers, restauranteurs, etc. Either way, it is a stark reminder just how easily someone can reach out and affect someone using the internet and some misconfigured devices.
