Cyber Intelligence Weekly (July 17, 2022): Our Take on Three Things You Need to Know
Welcome to our weekly post where I will be sharing some of the major
developments on the future of cybersecurity that you need to know about.
Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
You can also Subscribe to receive Cyber Intelligence Weekly in your inbox each week.
Before we get started on this week’s CIW, I’d like to highlight an upcoming webinar we have with our friends at PlexTrac! We are going to speaking about different maturity levels within the realm of offensive security and how to achieve higher heights, please sign up here and join us!

Away we go!
1. Amazon Handed Ring Videos to Police Without Warrants
The Amazon-owned security device company, Ring, is in the news this past week after a new report from Politico reveals that Ring has given law enforcement officials Ring footage on at least 11 occasions in the past year. This data was revealed to Senator Ed Markey, after he sent Amazon a series of concerns and questions back in June. The full response from Amazon can be found here. The Amazon-Ring response notes, “So far this year, Ring has provided videos to law enforcement in response to an emergency request only 11 times. far this year, Ring has provided videos to law enforcement in response to an emergency request only 11 times. In each instance, Ring made a good-faith determination that there was an imminent danger of death or serious physical injury to a person requiring disclosure of information without delay.”

One of the major concerns over Ring video doorbells is that they are always on and can record people up to 30 feet away. In addition, there are over 2,100 police departments that use the Amazon-Ring created “Neighbors” app that allows police to access videos uploaded by users. Couple that with the mass popularity of the devices and you have all the makings of a mass surveillance system. According to the latest transparency report from Amazon-Ring, they saw an increase in legal demands to view footage, 3,147 time, up 65% year over year. As the adoption of internet connected devices everywhere increases, these types of fundamental issues are only going to keep increasing in volume and complexity.
2. Honda Key Fob Hack Allows Anyone to Remotely Unlock Honda Cars
A new bug found in Honda key fobs, dubbed “Rolling-PWN” allows anyone to wirelessly grab the authentication codes from a car owners key fob. It allows anyone to permanently open the car doors as well as start the car engine from a long distance. The research noted that all Honda vehicles on the market from year 2012 to year 2022 are affected by this vulnerability.
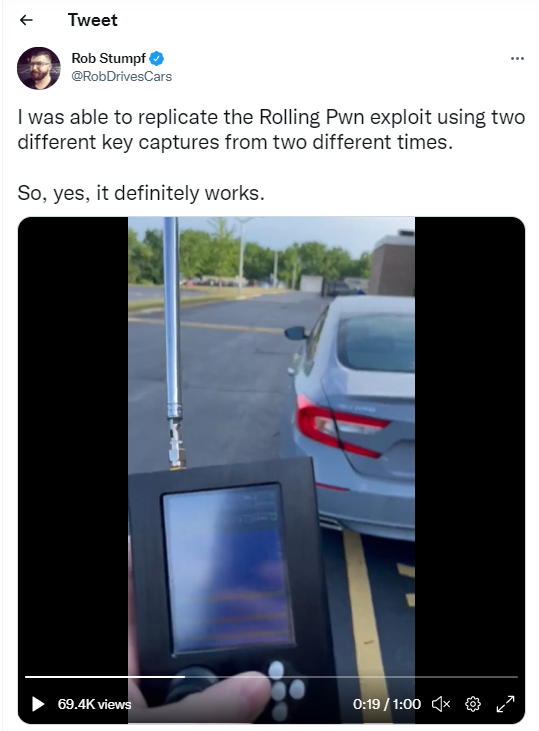
Car manufacturers have been ensuring the safety of locked cars via remote by ensuring that the codes that the car and key fob communicate are not static, they are in fact “rolling.” These rolling codes work by using a Pseudorandom Number Generator (PRNG). The code is sent from the fob to the car, the car checks the code based on the PRNG, and if valid, unlocks the vehicle. Apparently, there is a “window” of allowed codes in case the fob is not close enough to the car when the button is pushed. This vulnerability eavesdrops on the fob communication and captures the codes. This vulnerability allows an attacker to play back older codes in a special sequence to the Honda vehicles and it apparently resynchronizes the counter, so that commands from an older PRNG sequence can be played again and accepted as valid.
Honda supposedly did not take the security researchers work seriously at first and told them to call customer service, rather than take an official bug report. The bug was independently tested and validated by Rob Stumpf, a report from The Drive. Here is a video of Mr. Stumpf remotely starting and unlocking his car, supposedly taking advantage of this vulnerability. Honda has since publicly confirmed the vulnerability.
3. North Korean Operatives are Trying to Infiltrate US Crypto Firms
We’ve written extensively of the insider threat in past iterations of this newsletter. This past week Sean Lyngass, a cybersecurity reporter for CNN, wrote an excellent piece on how North Korean operatives are posing as legitimate knowledge workers in order to infiltrate technology and Web3 types of firms in order to find ways to steal funds and assets that they can filter back illicitly to North Korea. The CNN report recounts stories of tech CEO’s and hiring managers hiring and dealing with supposed agents of North Korea for their IT jobs.
As we all know, the technology hiring market is difficult for companies right now, especially in growing and emerging sections, such as cryptocurrency and Web3. These market conditions help create opportunities for these agents of North Korea, especially in a new commercial world where remote work is normalized. These workers are often in countries that are friendly to North Korea, or they obtain remote freelance IT work through middle agencies in other countries such as China, Russia, Ukraine, Canada, etc.
This reporting comes on the heels of a joint advisory issued in May from the U.S. Department of State, U.S. Department of Treasury, and the FBI where they sound the alarm on Democratic People’s Republic of Korea (DPRK) IT workers attempting to obtain employment. The advisory speaks to how the DPRK dispatches thousands of highly skilled IT workers around the world to generate revenue to help the DPRK operate its military regimes and weapons of mass destruction, in violation of U.S. and UN sanctions.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
