Cyber Intelligence Weekly (July 31, 2022): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Also, we are always looking for great people to join our team. If you know anyone who fits the profiles for any of our open positions, drop me a line and let me know!
Before we get started on this week’s CIW, I’d like to highlight and remind our subscribers about this two-day training class that Dahvid Schloss, Managing Lead of Offensive Security, will be giving at DEFCON in a few weeks. If you are headed to DEFCON, sign up here before it is too late!

Away we go!
1. UEFI Rootkits, Hidden Lurking Malware
Security researchers put out a report last week unveiling a malicious UEFI rootkit used in the wild sine 2016. Unified Extensible Firmware Interface (UEFI) is a publicly available specification that defines a software interface between an operating system and platform firmware. UEFI replaces the legacy Basic Input/Output System (BIOS) boot firmware. Basically, this stuff gets in there so deep, it is nearly impossible to detect an infection.
Kaspersky is the organization that uncovered the UEFI rootkit, dubbed ‘CosmicStrand’ that they are also attributing to a an unknown Chinese speaking threat actor group. The research notes that the rootkit is most likely located in the firmware images of Gigabyte or ASUS motherboards, and they also noticed that all the images are related to designs using the H81 chipset.
The concept of UEFI malware is difficult to engineer given that UEFI components will have terminated before the Windows operating system is loaded. However, in this recent finding, Kaspersky noted that this malware passes down malicious code through the various startup phases, but it starts at the UEFI level. The below graph from Kaspersky summarizes the flow.
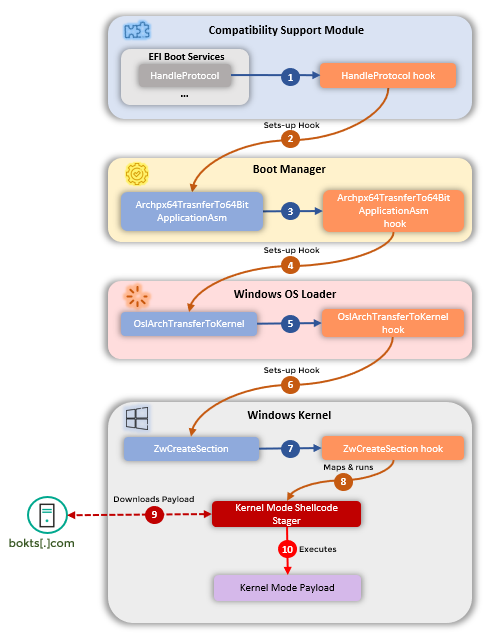
Image: Kaspersky
When attackers are able to modify the startup process at that deep of a level within the machine, it is obviously very concerning. It has been thought that there are not many threat actor groups with this level of technical sophistication, however, these new findings may just challenge those assumptions.
The author of the research made a final point in his article that sums it up the issue well, “The most striking aspect of this report is that this UEFI implant seems to have been used in the wild since the end of 2016 – long before UEFI attacks started being publicly described. This discovery begs a final question: if this is what the attackers were using back then, what are they using today?”
2. Untangling KNOTWEED, Microsoft Highlights Austrian Cyber Actor in Latest Blog
Last week, Microsoft released a new blog post that called out KNOTWEED, a threat actor group that they define as a private-sector offensive actor (PSOA), who they allege is using multiple Windows and Adobe 0-day exploits in the wild, unknowingly to the victims. Per the research, KNOTWEED is an Austria-based PSOA named DSIRF. The research noted that the observed victims to date may include law firms, banks, and consultancies in Austria, the United Kingdom, and Panama.
This group has been targeting these organizations with malware that they dub as Subzero. The research and previous news stories link DSIRF to the development and sale of the Subzero malware. Microsoft also noted that they communicated with the supposed victims of this group and they noted that they had not sanctioned or approved any penetration testing or red-teaming against them from DSIRF.

As far as mitigations go, Microsoft recommends patching their operating systems for a vulnerability that their malware takes advantage of, CVE-2022-22047. In addition to that, Microsoft notes that they have been adding indicators to their security tools, such as Defender, to look for any other indicators. Other suggestions from Microsoft include enabling MFA and locking down Microsoft Excel macro settings.
3. Hacker Teaches How to Shoplift at Recent Conference
At the New HOPE Hacker conference in New York City last week, a security researcher called MakeItHackin dove deep into the security of loss prevention devices and security tags used in retail settings.

MakeItHackin is famous for his TikTok, which he started during the pandemic, where he shows his discoveries to the mass public. Pictured above is where he illustrates how to bypass RFID tags from store security systems. This video has over three million views alone.
MakeItHackin does not condone or encourage shoplifting, he is merely doing this because he is truly interested in how things work and sharing it with others. The sharing of these methods on social media platforms however create an interesting dilemma as it allows millions to see exactly how they can pull of these scams in real life if they so choose.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
