Cyber Intelligence Weekly (Nov 21, 2021): Our Take on Three Things You Need to Know
Welcome to our weekly post where I will be sharing some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
You can also Subscribe to receive Cyber Intelligence Weekly in your inbox each week.
Before we get started, check out this great piece by Senior Manager, Luke Wawrzeniak, where he dives into top tech trends from Gartner and the corresponding cyber risk management issues.

Away we go!
1. United States Charges Two Iranians with Attempting to Interfere with 2020 Presidential Election
Last week, an indictment was unsealed in New York that charged two Iranian nationals for their alleged involvement in a cyber campaign to influence American voters in the 2020 presidential election. Further details are available in a Justice Department press release. The indictment fingers Seyyed Mohammad Hosein Musa Kazemi, aka Mohammad Hosein Musa Kazem, aka Hosein Zamani, 24, and Sajjad Kashian, aka Kiarash Nabavi, 27, both of Iran. The DOJ press release notes that Zazemi and Kashian are Iran-based computer hackers who worked as contractors for an Iran-based company formerly known as Eeleyanet Gostar, and now known as Emennet Pasargad. Eeleyanet Gostar purported to provide cybersecurity services within Iran.
The DOJ press release describes the following, “As alleged, Kazemi and Kashian were part of a coordinated conspiracy in which Iranian hackers sought to undermine faith and confidence in the U.S. presidential election,” said U.S. Attorney Damian Williams for the Southern District of New York. “Working with others, Kazemi and Kashian accessed voter information from at least one state’s voter database, threatened U.S. voters via email, and even disseminated a fictitious video that purported to depict actors fabricating overseas ballots.”
In summary, the indictment alleges that the accused:
- Conducted reconnaissance on and attempted to compromise approximately 11 state voter websites.
- Sent false, misleading, and intimidating messages to Republican Senators, Republican Members of Congress, Trump campaign associates, White House advisors and members of media noting that the Democratic party was planning to exploit weaknesses in state voter website to carry out voter fraud.
- Sought to utilize illegal access to an American Media Company (unnamed in the indictment) to further disseminate false claims concerning the election.
- Engaged in an online voter intimidation campaign involving the dissemination of a threatening message purporting to be from the Proud Boys, to tens of thousands of registered voters.
The voter threat emails, which included the name and street address of the recipient, read:
We are in possession of all your information (email , address, telephone ... everything). You are currently registered as a Democrat and we know this because we have gained access into the entire voting infrastructure. You will vote for Trump on Election Day or we will come after you. Change your party affiliation to Republican to let us know you received our message and will comply. We will know which candidate you voted for. I would take this seriously if I were you.
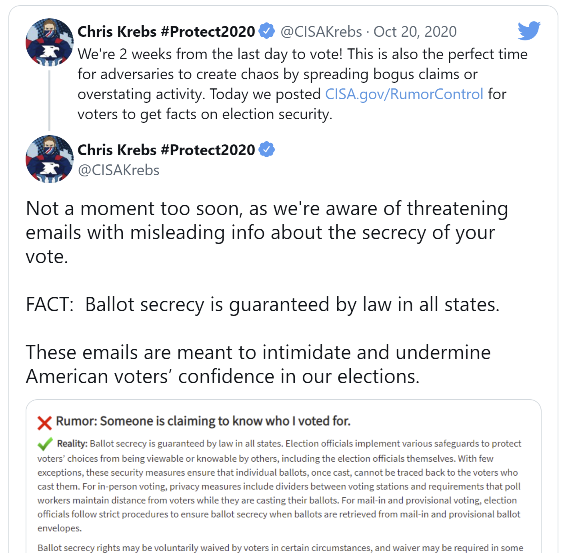
Allegations like this definitely highlight just how nation states can attempt to influence an election process and undermine our Democracy. I specifically recall these messages circulating during the election, as they were addressed directly by Chris Krebs, the former Director of CISA during that time. It caused a lot of confusion and intimidation amongst voters during that period of time.
2. $500 Million in Cyber Spending Inches Closer to Reality as Part of 'Build Back Better' Bill
On Friday morning, the House of Representatives passed President Joe Biden's “Build Back Better” bill, which is a wide-ranging package of Democratic social spending priorities. The bill will now make it’s way to the Senate, where its future is still unknown. Included as part of those spending priorities is over $500 million in cybersecurity related spending. These specific cybersecurity spending measures are historic in terms of size and scale of cybersecurity specific spending.
The bill itself, mentions cybersecurity over 33 times throughout the text. There are secondary spending measures in the bill that include cybersecurity measures within other sections of the bill, such as cybersecurity protection for the Deployment of Next Generation 9-1-1 for example.
However, the majority of the cybersecurity related spending is attributed to the US Cybersecurity and Infrastructure Security Agency (CISA) and CISA related programs. As a reminder, CISA’s charge is to “…lead the national effort to understand, manage, and reduce risk to our cyber and physical infrastructure. “
Most notably and specifically as it pertains to CISA, the bill includes the following:
- $400 million for the implementation of Executive Order 14028, improving the nation’s cybersecurity, which includes including the implementation of multi-factor authentication, endpoint detection and response, improved logging, and securing cloud systems;
- $100 million for cybersecurity workforce development and education, including providing education, training, and capacity development;
- $75 million for expansion and operation of the CyberSentry program; and
- $50 million to support the Multi-State Information Sharing and Analysis Center (MS-ISAC).
You didn't think they actually spent ten thousand dollars for a hammer and thirty thousand for a toilet seat, did you? (Special bonus points to whomever messages me with the movie this is from, no cheating!)
3. CISA Releases Playbook for Incident Response
Speaking of CISA, last week, they issued playbooks for incident response, providing agencies with a standard set of procedures to both respond to incidents and address vulnerabilities on government networks. These are operation procedures that can be leveraged for planning and conducting cybersecurity incident and vulnerability response activities.
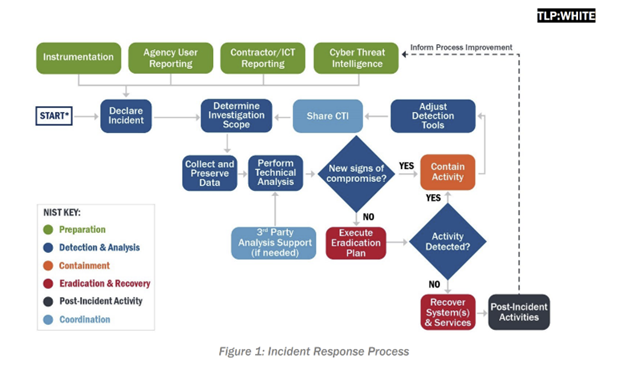
With cybersecurity incidents happening at a breakneck rate, the CISA playbooks could not have been more timely. While the playbooks were created for federal civilian agencies, CISA urges the private sector, critical infrastructure entities, and other state, local, tribal and territorial governments to review and leverage them for their own response processes and procedures. We always like to say, don’t let your first computer security incident be a real one and prepare as if it will happen one day. As the late/great John Wooden used to say, “Failing to prepare is preparing to fail.”
