Cyber Intelligence Weekly (Nov 7, 2021): Our Take on Three Things You Need to Know
Welcome to our weekly post where I will be sharing some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
You can also Subscribe to receive Cyber Intelligence Weekly in your inbox each week.
Away we go!
1. Department of Defense Cybersecurity Framework, CMMC, Gets Major Overhaul
The United States Department of Defense announced long awaited changes to their Cybersecurity Maturity Model Certification (CMMC), dubbing it CMMC 2.0. There has been much talk about the impact that the first version of the CMMC system would have on small and medium-sized businesses that support the Defense Industrial Base (DIB). The DOD had received numerous public comments in response to the interim rule establishing CMMC 1.0 regarding how onerous the model was to SMBs.
One of our talented cyber consultants who has the pulse on the CMMC, wrote about some key takeaways to the program here. In addition, the below infographic outlines some of the model specific changes and new characteristics.
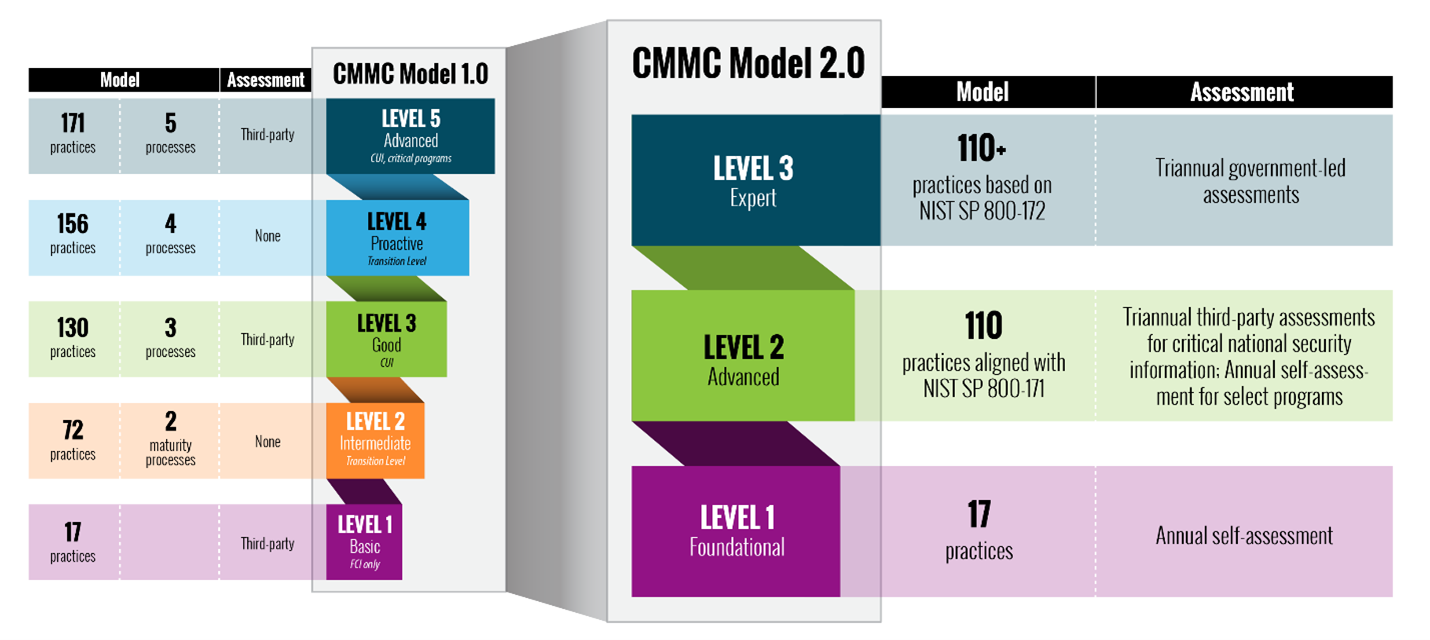
Image Source: https://www.acq.osd.mil/cmmc/a...
My initial reaction to all these changes is one of disappointment. Here are some quick initial reactions from my point of view:
- I personally understand that the requirements may be onerous to SMBs, but at the end of the day, if SMBs want to support the military in the 21st century, there should be a high bar to protect our intellectual property and men and women in the service.
- CMMC 2.0 no longer has maturity and processes or CMMC-unique practices, as NIST 800-171 will be the basis for CMMC 2.0. Well then, why is it still named CMMC? Shouldn’t we drop an “M”?
- The former CMMC-unique practices were value added and made sense to be in the framework, removing these controls doesn’t increase the level of cybersecurity, it only lowers the bar.
- Only a subset of Level 2 will require third-party audits. This in my opinion is one of the biggest potential errors of the entire reconfiguration of this rule. I have personally seen companies self-certify that they meet the NIST 800-171 controls before, and they weren’t even close. These companies didn’t even understand half the requirements they were self-attesting to. Not having qualified third-party auditors VERIFYING compliance, is a big issue.
- CMMC 2.0 is still just a twinkle in the eye of the DOD. CMMC 2.0 will not be a contractual requirement until rulemaking is complete. The Office of the Undersecretary of Defense notes that the rulemaking process and timelines can take 9-24 months.
2. Company Directors and Boards in the Crosshairs Over Cyber Incidents
As breaches have heated over the past couple of years, so have lawsuits in the court room. Earlier this month, the infamous Marriott/Starwood breach was in view again because of a lawsuit that came to a head recently in Delaware. Ultimately, Marriott and its Directors prevailed as the lawsuit was dismissed by Delaware Chancery Court Vice Chancellor, Lori Will. The ultimate hang up in this case (and in future cases) is asserting the “Caremark” rule was violated.
Due to prior caselaw (e.g.; Caremark), the plaintiff must prove that directors either (1) utterly failed to implement any sort of internal controls or other oversight or (2) consciously failed to monitor or oversee the controls that were in place, turning a blind eye to the risks or problems at hand. This sets an extremely high, almost impossible bar, for plaintiffs to prove. Despite the case against Marriott producing several Internal Audit reports, Audit Committee Updates, Post Starwood Merger Memos, etc. that showed that cybersecurity was, and continued to be a major issue and a key risk, it was not enough to say that the Directors of Marriott were culpable.
The next big lawsuit on the docket that I am following is one recently filed by a Missouri Pension Fund against SolarWinds. In the lawsuit they allege that SolarWinds did not monitor cybersecurity risks appropriately and that they should be held liable and accountable for the recent breach that left SolarWinds and their customers, and SolarWinds stock, in a downward spiral.
These cases obviously signal the fact that investors and regulators alike are paying much more attention to the carnage and damage that these cybersecurity incidents can have on our lives and investment accounts, among many other perceived harms. However, if the laws don’t change anytime soon, the bar to hold anyone liable in these cases seems like a distant reality.
3. Israeli Spyware Producer NSO Group Blacklisted by US Government
The United States Department of Commerce recently posted an addition of companies to its federal blacklist, which essentially does not allow American businesses to do business with or engage with organizations on this list. The bulletin notes that the entities have been “determined by the U.S. Government to be acting contrary to the foreign policy and national security interests of the United States.”
The NSO group has long been the subject of much controversy over the past several years, as their software has been allegedly tied to the targeting of activists, political dissidents and journalists. NSO has frequently denied these claims and repeatedly states that it only licenses its tools to governments for the surveillance of criminals and terrorists.
This is clearly a shot across the bow from the United States. One would think that the NSO group would be significantly impacted by this decision as they will no longer be able to procure technology and other services from the United States, including services like AWS, Azure, or others.
