Cyber Intelligence Weekly (October 23, 2022): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Also, we are always looking for great people to join our team. If you know anyone who fits the profiles for any of our open positions, drop me a line and let us know!
Before we get started on this week’s CIW, I’d like to thank our 15,000+ subscribers! Every time we hit a milestone number, it is pretty humbling, but to cross the 15k mark, I never imagined that! Thank you all so much for subscribing to my newsletter, I hope to find more ways to improve it each and every week.

Away we go!
1. Australia’s Largest Healthcare Insurer Confirms Data Breach
Just weeks after we wrote about the Optus data breach in our CIW newsletter, the Aussies are under fire again. This time reports are swirling that Australia’s largest healthcare provider, Medibank, has been hit by a massive attack.

The threat actors involved in this breach say that they have stolen over 200 GB of data. This attack is most concerning given that healthcare records are some of the most private details of someone’s life, and healthcare records typically have all the data need to steal someone’s identity fully.
Per an official press release from Medibank, they noted that the threat actors have provided a sample of records for 100 policies that they believe came from their ‘ahm’ and international student systems. They noted that the data includes first names and surnames, addresses, dates of birth, medicare numbers, policy numbers, phone numbers and some claims data. It has certainly been a bad month for the data privacy of the Aussies.
2. CISA Begins Request for Comments on Microsoft 365 Security Configuration Baselines
The Cybersecurity and Infrastructure Security Agency (CISA) has recently released a request for comments (RFC) for their new Microsoft 365 security configuration baselines. This is part of their new Secure Cloud Business Application project (SCuBA). What a name, right?

Major business applications like the Microsoft 365 suite are convenient for many businesses due to the sheer number of applications that come along with the package as well as the low overhead and maintenance. While these applications are great, they are never fully secure “out-of-the-box.” This is why our MS 365 security hardening assessment is one of the more popular things that we do for our clients. I applaud CISA for its efforts on putting this together, this should be a popular tool that many organizations can utilize to harden their cloud environment.
The RFC period is open until Nov. 24, 2022. CISA is specifically requesting insight on the feasibility, clarity, and usefulness of the baselines. Comments should be submitted to: [email protected].
3. Feds Warn About Ransomware Threats to Healthcare Organizations
A new joint Cybersecurity Advisory (CSA) has been released by CISA as part of its ongoing campaign raising awareness in an effort to curb ransomware efforts. These advisories are aimed at network defenders and they detail various ransomware variants and ransomware threat actors. The CISA advisories include recently and historically observed tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs) to help organizations protect against ransomware.
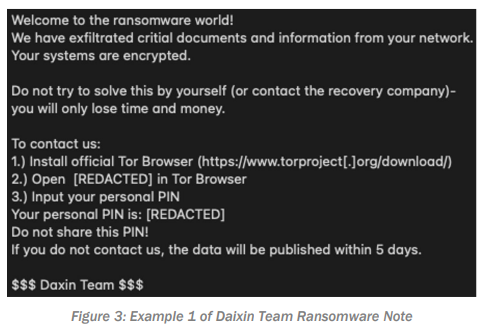
In the most recent advisory, CISA highlights the “Daixin Team”, a threat actor group that is targeting U.S. based businesses, with many of them being in the Healthcare and Public Health sector. The report paints a picture of a group of threat actors that both deploy ransomware to encrypt resources, but they also steal electronic personal health information (ePHI).
The report highlights the tactics, techniques, and procedures that the threat actors use in great detail. The report also outlines several recommendations for mitigations, including:
- Regular patching and updating operating systems and software
- Requiring phishing-resistant MFA
- Turning off and restricting network device management interfaces when not needed
- Implementing multi-layer network segmentation
- Segregating standard account use from administrator account use
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
