Hacker’s Perspective: Web App Vulnerabilities - Algolia API Keys
Algolia API Keys – Are you exposing your company’s internal data?
Algolia APIs are extremely useful for fast and efficient access to stored data. At Echelon, we see them used in around 20% of our web app tests. Unfortunately, the keys used to access these APIs are easily misconfigured and can allow an attacker to read internal company data, or even launch a site-wide attack to takeover customer accounts!
Why Does It Matter?
Algolia APIs use both an ApplicationID and key to identify a host and allow for access. These keys can be found in every call to the API and are meant to be public. However, many developers are unaware that the permissions of these keys are also public!
They can be read by anyone accessing the URL below and filling in your AppID and API keys:
https://APPID-dsn.algolia.net/1/keys/APIKEY?x-algolia-application-id=APPID&x-algolia-api-key=APIKEY
This will return data like the following:
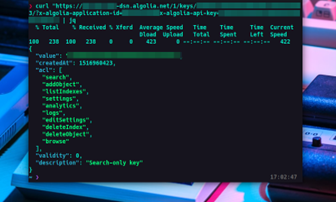
The main thing to note from the above photo is the key permissions listed under the ‘acl’ JSON object. These permissions show what an attacker can do with the key. If there are ANY permissions assigned to the key beyond ‘search,’ then this key is considered misconfigured.
Assuming the below permissions are assigned, an attacker would be able to:
- listIndexes -> Get list of all existing indexes along with full access to the data within them
- editSettings -> Update index settings, which allows an attacker to specify JavaScript to be executed upon EVERY API call
- addObject -> Add or update records
- logs -> Query the logs
- deleteIndex or deleteObject -> Delete records
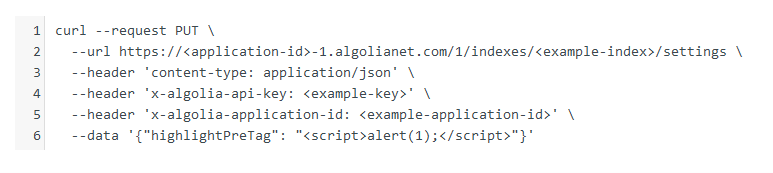
As you can see, a misconfigured Algolia API key can lead to some serious issues ranging from low to critical severity.
How Can You Fix It?
To fix this vulnerability, we recommend analyzing your key permissions and ensuring only the ‘search’ permission is attached. If other permissions are assigned, remove them immediately.
Another option is to use Algolia’s Secure Keys feature, which are like standard API keys but include a set of restrictions embedded within them and are base64 encoded. They can only be used within pre-defined constraints, preventing unauthorized access to data within your API.
