Cyber Intelligence Weekly (April 3, 2022): Our Take on Three Things You Need to Know
Welcome to our weekly post where I will be sharing some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
You can also Subscribe to receive Cyber Intelligence Weekly in your inbox each week.
Before we get started on this week’s CIW, I’d like to highlight a great article by our very own Stephen Scandrett, where he breaks down the key takeaways from the CrowdStrike 2022 Global Threat Report. This is a great read that highlights some of the key takeaways in the threat landscape overview, as well as seven ways to stay ahead in 2022, enjoy!

Away we go!
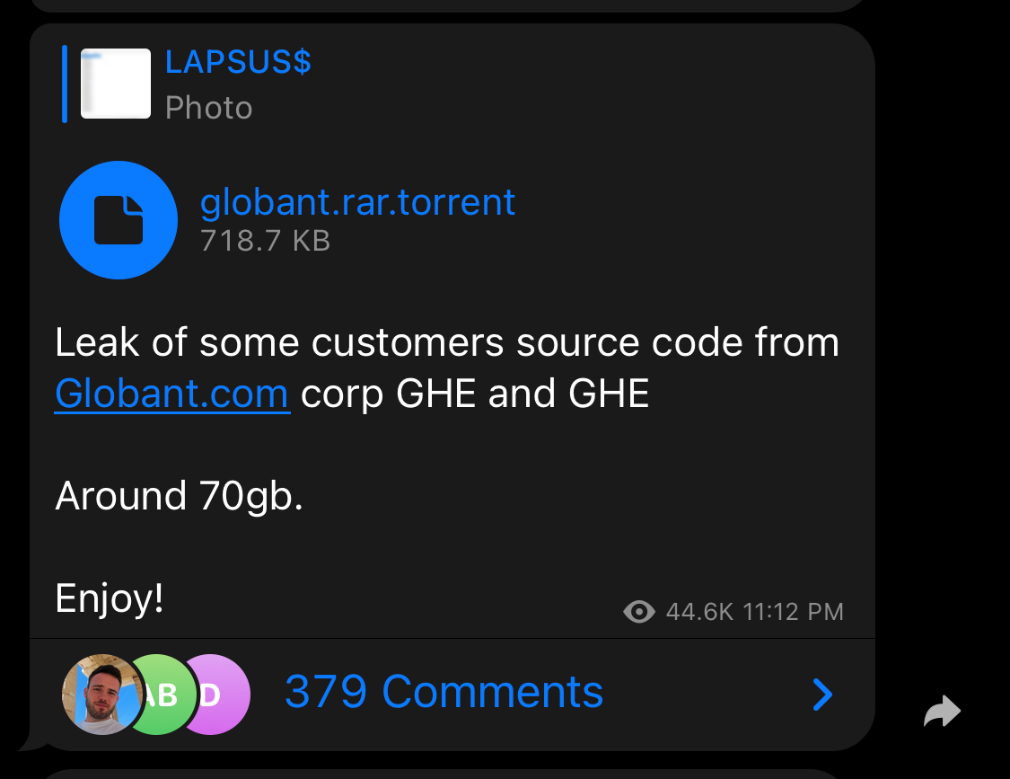
1. Software Giant Globant Confirms Breach after LAPSUS$ Shares 70GB of Stolen Data
In an official statement last week, software giant Globant confirmed that “a limited section of our company's code repository has been subject to unauthorized access.” This was after the LAPSUS$ group supposedly published a portion of Globant’s source code repository on their Telegram site earlier in the week.
LAPSUS$' recent string of victims include several high-profile names such Okta, Microsoft, Nvidia and Samsung. In last week’s Cyber Intelligence Weekly (CIW) we reported on several of their recent attacks as well recent arrests made on several supposed group members in the UK.
In addition to the source code dump, the LAPSUS$ group also threatened to expose other “poor security practices” at Globant as well as administrative credentials for all of their devops platforms.
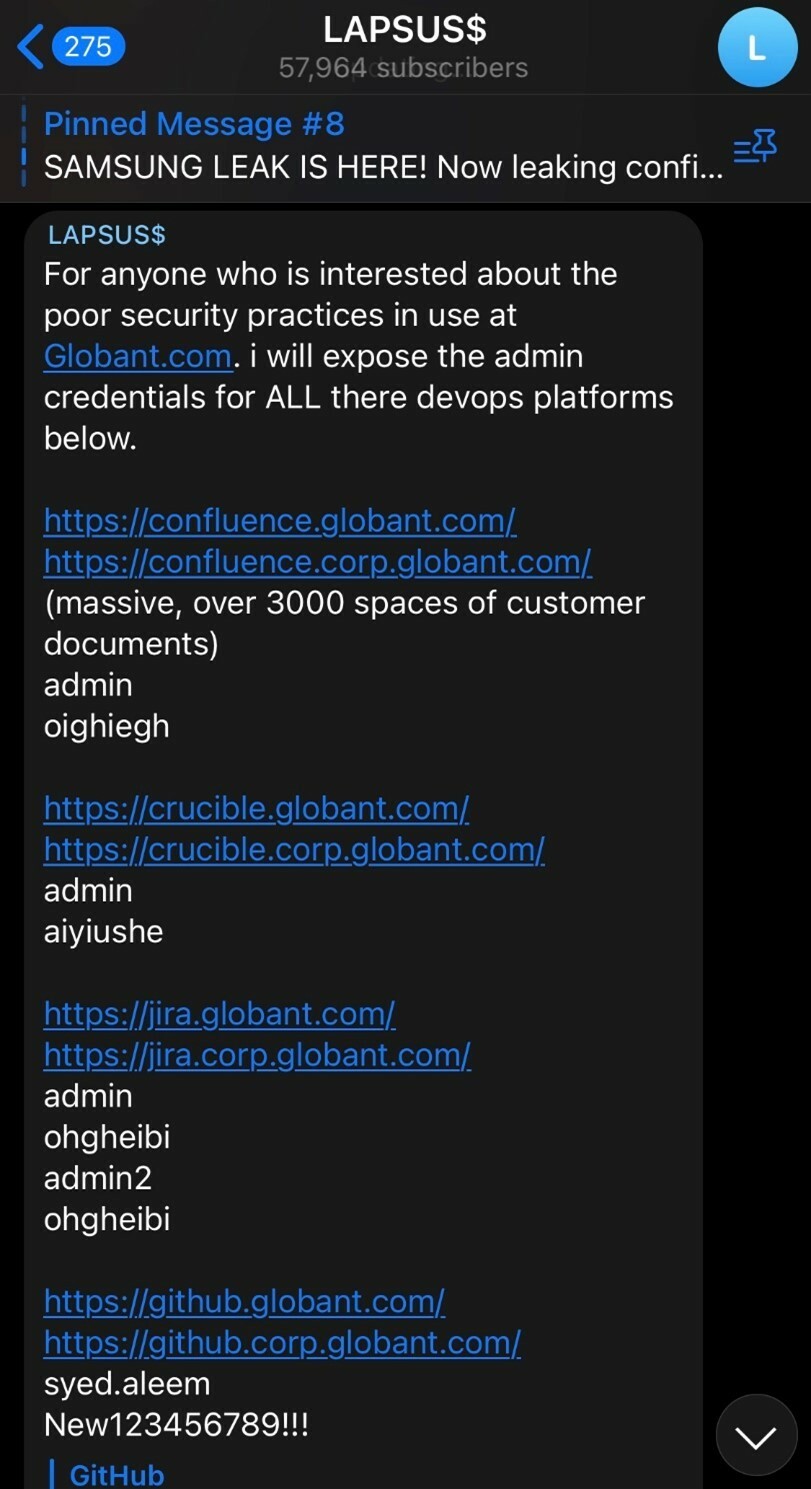
It appears that those arrests have not deterred, nor slowed down, this highly effective threat group as Globant joins a long list of major organizations befuddled by these attackers.
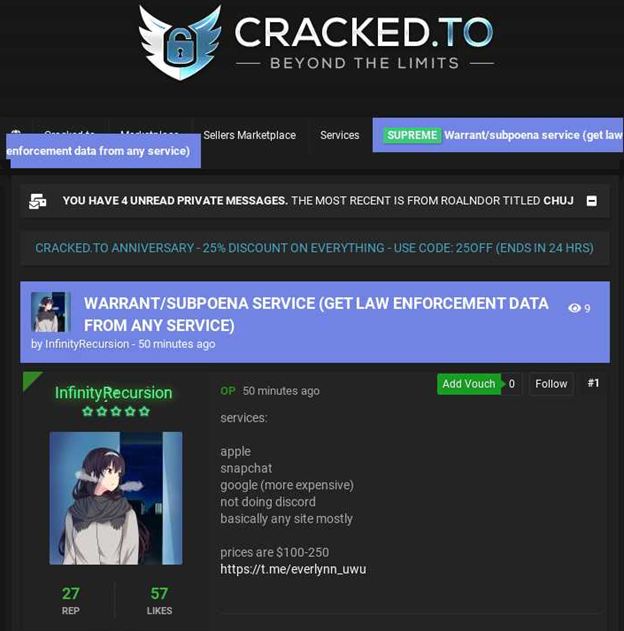
2. Hackers Gaining Power of Subpoena Via Fake “Emergency Data Requests”
It has come to light that major social media and tech companies such as Apple, Meta, and possibly many others have provided subscriber detail to hackers, such as customer address, phone number, IP address and possibly more in response to forged “emergency data requests.”
In a story that first broke from Brian Krebs, he explains how hackers are circumventing a known process that allows for legitimate law enforcement requests for data on the customers of these large tech firms. Normally, law enforcement will need a warrant or subpoena to obtain information about who owns a certain account, however, there are certain circumstances where one of these requests may be urgent in nature, which bypasses the need for official documents. These scenarios are called “Emergency Data Requests.”
Groups of hackers have determined that they can bypass the official documents needed to request personal information from a social media company or tech firm by pretending to submit an Emergency Data Request from a legitimate law enforcement email address. All they need to do is takeover an email account. In his article, Krebs connects these types of hacks to the LAPSUS$ group through their connection to a dark web marketplace that sells this level of email access to perform these fraudulent requests.
3. Critical GitLab Vulnerability Allows Attackers to Take Over Accounts
Popular DevOps platform, GitLab had what appeared to be a not-so-funny April Fools’ Day joke a couple of days ago, as several users were complaining about their accounts having devices added to them for additional 2FA access.
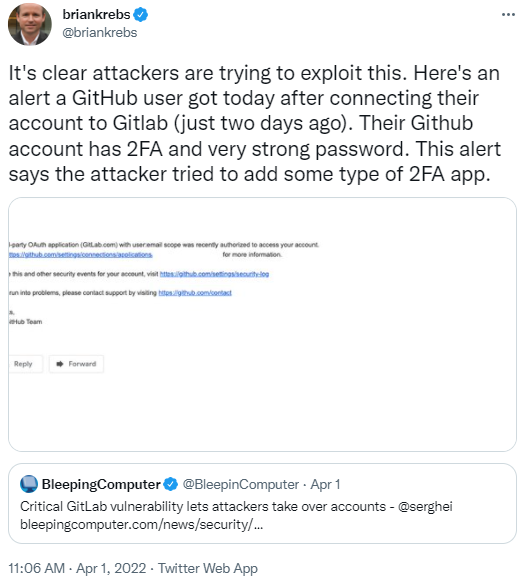
As it turns out, on March 31, GitLab released a new critical patch due to static passwords being inadvertently set during OmniAuth-based registration. Per the GitLab blog, “A hardcoded password was set for accounts registered using an OmniAuth provider (e.g. OAuth, LDAP, SAML) in GitLab CE/EE versions 14.7 prior to 14.7.7, 14.8 prior to 14.8.5, and 14.9 prior to 14.9.2 allowing attackers to potentially take over accounts. This is a critical severity issue (CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:N, 9.1). It is now mitigated in the latest release and is assigned CVE-2022-1162.”
The affected editions were both the GitLab Community Edition (CE) and Enterprise Edition (EE). A BleepingComputer report on the matter showed that GitLab deleted the 'lib/gitlab/password.rb' file, which was used to assign a weak hardcoded password to the 'TEST_DEFAULT' constant. Below is a screenshot from the BleepingComputer report.
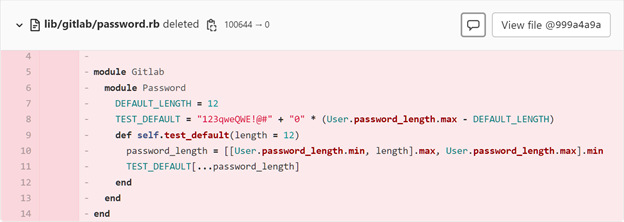
We are reminded yet again about security best practices within the software supply chain and how important they can be.
Thanks for reading! Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more point solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
