Cyber Intelligence Weekly (March 27, 2022): Our Take on Three Things You Need to Know
Welcome to our weekly post where I will be sharing some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
You can also Subscribe to receive Cyber Intelligence Weekly in your inbox each week.
Before we get started on this week’s CIW, I’d like to highlight a recent video interview our very own Lily Clark did with John Hammond, “Career Conversations with seclilc - Offensive Cybersecurity!” If you are interested in a career in penetration testing or consulting in general, this is a great listen!

Away we go!
1. Okta Compromise by LAPSUS$ Causes Massive Concern
The cybersecurity and IT community were largely abuzz last week due to a quick escalation of a reported compromise at Okta. Okta is used by thousands of organizations globally for numerous important cybersecurity functions, including the control of single sign-on and multi-factor authentication (MFA). An application that controls such important authentication mechanism would be a juicy target for attackers as a compromise of their systems could lead to compromises of thousands.
Screenshots of internal customer support applications for the company were being shared on Twitter and it quickly became a heated issue, prompting further response from Okta. According to a timeline and additional details posted on their blog, Okta reported that the compromise stemmed from the unauthorized access of a contractor account through Sitel, an Okta vendor that assists with customer support.
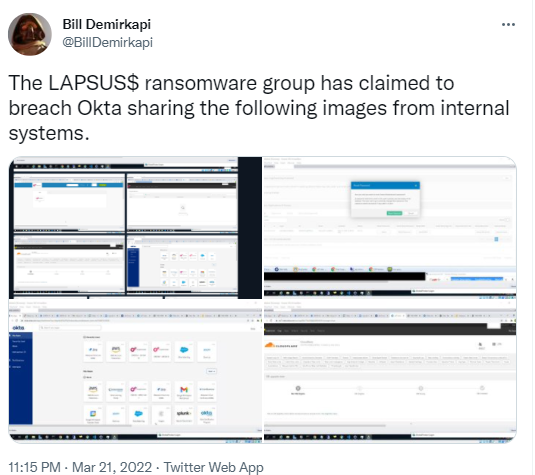
Okta notes that the scope of the proposed compromise was very limited in scale and scope. Here is a statement from David Bradbury, their Chief Security Officer “After a thorough analysis of these claims, we have concluded that a small percentage of customers – approximately 2.5% – have potentially been impacted and whose data may have been viewed or acted upon. We have identified those customers and already reached out directly by email. We are sharing this interim update, consistent with our values of customer success, integrity, and transparency.”
The statements from Okta continue to call the actions a “compromise” rather than a “breach” and the overwhelming narrative from the company is that the threat actors had access to certain customer support functions but did not have any deeper access than that. Per an FAQ from Okta, “Sitel’s support engineers have limited access. They are unable to create or delete users, or download customer databases. Support engineers are able to facilitate the resetting of passwords and multi-factor authentication factors for users, but are unable to choose those passwords.”
The official company reports of the compromise were challenged by the purported hacking group “LAPSUS$” on their Telegram channel, which has over 52,000 subscribers at the time of this writing. More on them in the stories below…
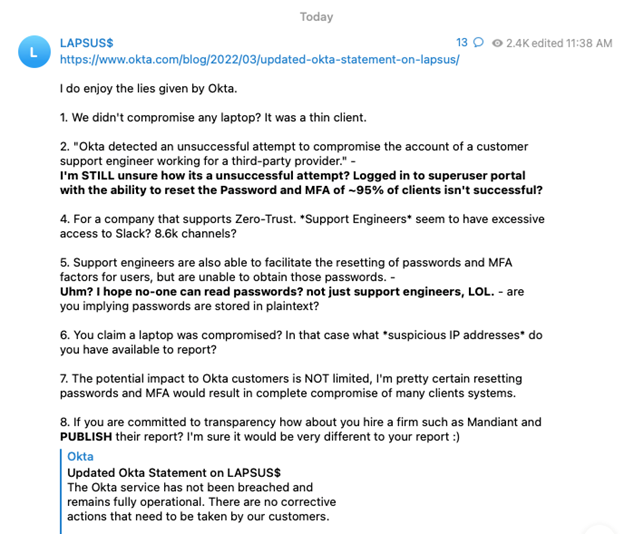
Okta has noted in their blogs and official statements that they have communicated to all customers that they believe may have been affected in this incident. They also state in their materials that they do not believe corrective actions need to be taken by their customers. Although the company states that, that certainly wouldn’t be a bad exercise to perform out of an abundance of caution. The co-founder and CEO of Cloudflare, Matthew Prince, would agree.

What is most alarming about this story, and has raised the most public uproar, is the length of time that it took Okta to come clean about this incident and notify their customers. It wasn’t until after the LAPSUS$ group went public until Okta was forthcoming, and many are angry about that. Okta tosses the blame back to their third-party support organization and the length of time that it took to complete an investigation. To Okta’s credit, per their blog, they did identify a strange new factor added to the Sitel employee’s Okta account and flagged it immediately as suspicious and escalated the incident to Sitel.
This is a story that we will certainly continue to monitor as new developments are released.
2. LAPSUS$ Hackers Leak 37GB of Microsoft's Alleged Source Code
It was a busy week for the LAPSUS$ group last week. According to a Bleeping Computer story, LAPSUS$ posted a torrent file that contained partial source code for a variety of Microsoft products, including Bing, Bing Maps and Cortana.
Microsoft responded with a blog post of their own which details actions and specific tactics, techniques and procedures (TTPs) of LAPSUS$, as well as an admission that Microsoft had been compromised. Microsoft notes in their blog that, “a single account has been compromised, granting limited access.” They also downplay the incident by stating that Microsoft does not rely on the secrecy of their source code as a security measure and that they don’t believe that viewing the source code alone leads to an elevation of risk.
The Microsoft blog post is a must read for any network defender out there as it describes the specific TTPs used by LAPSUS$, everything from initial access to recon and privilege escalation, followed by their specific methods for exfiltration, destruction, and extortion.
What is most interesting about this group is their public display of openly buying access to organizations through their employees. Below is a screenshot from their public Telegram channel that calls for employees/insiders to give up their credential and MFA response for cash.
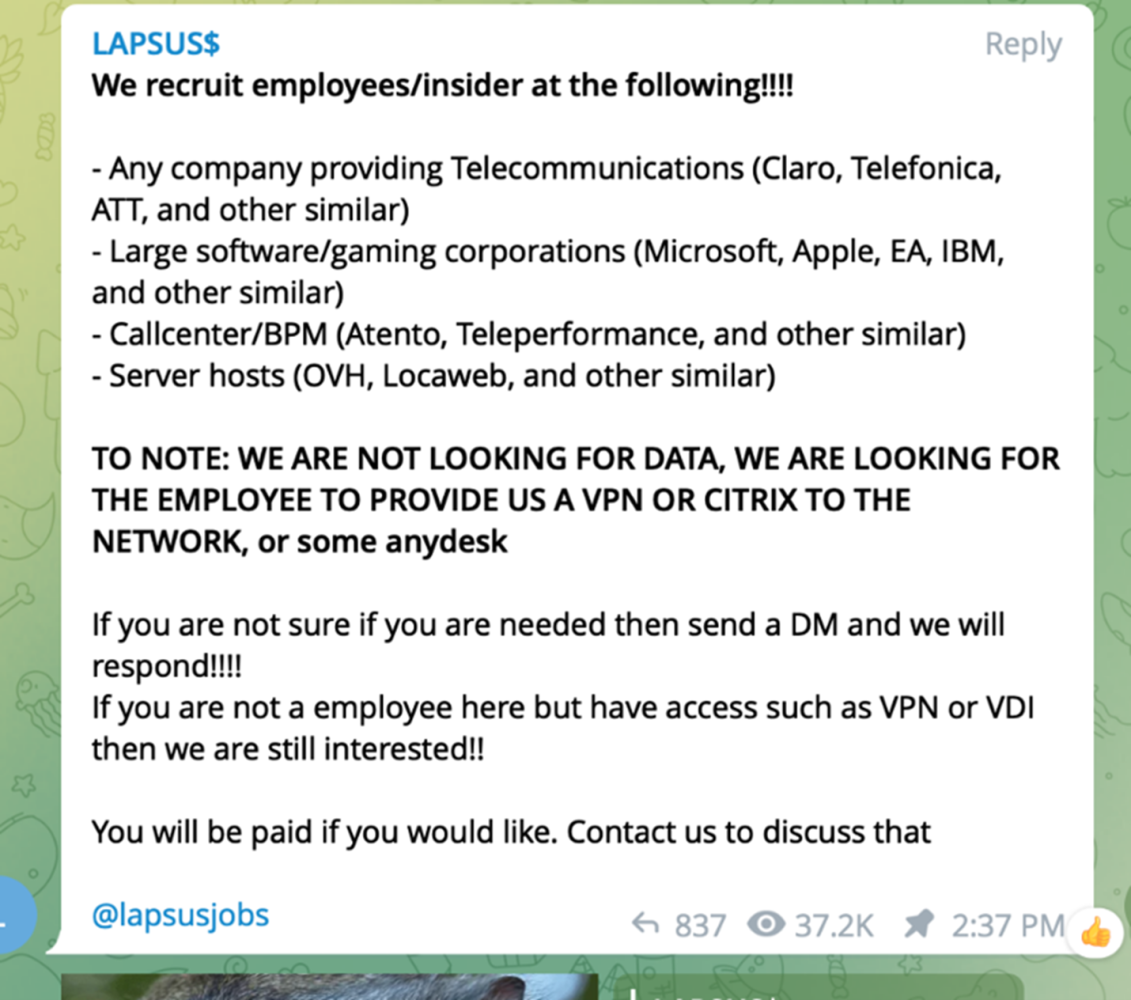
These types of attacks are unique and interesting because they require quick detection and response to what could look like normal internal access at first. To detect and respond to these types of incidents you must combine the elements of insider risk programs with short timeframe incident response, similar to a smash and grab type of incident.
3. U.K. Police Arrest 7 Related to LAPSUS$ Hacks on Tech Firms
Bloomberg has reported that the City of London Police have arrested several people in their supposed connection with LAPSUS$. The suspects are all between the ages of 16 and 21 and have been released as the investigation continues.
According to a similar BBC story, one of the leaders of the group was “doxxed” online after apparent disagreement with business partners. The hackers then revealed his name, address, and other identifying information online, which ultimately led to his arrest. The ring leader of the group, supposedly a 16-year old from Oxford has supposedly made over $14 million dollars from his hacking expeditions.
Due to the age of the individuals, and for privacy purposes, they cannot be named by the investigators. Many more details, including the background of the doxxing can be found in this excellent writeup by Brian Krebs.
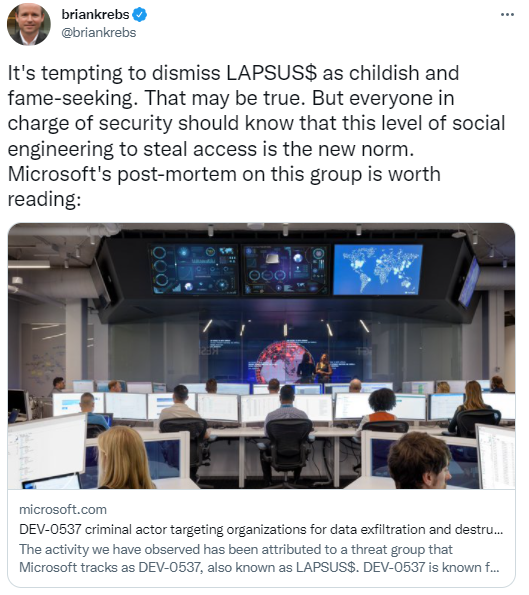
The tweet above from Brian Krebs is one of the most interesting takeaways from all of this. While threat groups have been buying access from legitimate users in the past, none have been so public and brazen about it as LAPSUS$. The worry is that they will spawn other copycat groups that groups and the publicity this has caused will give insiders the opportunity to cash in their credentials.
Do you hear that sound? That is the sound of risk assessments being updated worldwide to heighten the importance of insider threat.
Thanks for reading! Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more point solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
