Cyber Intelligence Weekly (February 12, 2023): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Also, we are always looking for great people to join our team. If you know anyone who fits the profiles for any of our open positions, drop me a line and let me know!
Before we get started on this week’s CIW, I’d like to highlight some reviews of our amazing people and the services they offer from our partner directory page at Drata. I think we have a pretty great team here, but it feels that much better when our clients do the talking!
Away we go!
1. United States and United Kingdom Sanction Members of Russia-Based Trickbot Cybercrime Gang
The U.S. Department of the Treasury announced last week that they, in coordination with UK authorities, are sanctioning seven individuals who are part of the Russia-based Trickbot cybercrime gang. Per the Cybersecurity and Infrastructure Security Agency (CISA), “TrickBot—first identified in 2016—is a Trojan developed and operated by a sophisticated group of cybercrime actors. Originally designed as a banking Trojan to steal financial data, TrickBot has evolved into highly modular, multi-stage malware that provides its operators a full suite of tools to conduct a myriad of illegal cyber activities.”
I have personally seen TrickBot leveraged against several organizations as an early stage malware and as a precursor before delivery of Ryuk ransomware. The Trickbot malware has been instrumental in carrying out wide swaths of very disruptive attacks over the years. The press release from the U.S. Department of the Treasury noted, “During the height of the COVID-19 pandemic in 2020, Trickbot targeted hospitals and healthcare centers, launching a wave of ransomware attacks against hospitals across the United States. In one of these attacks, the Trickbot Group deployed ransomware against three Minnesota medical facilities, disrupting their computer networks and telephones, and causing a diversion of ambulances. Members of the Trickbot Group publicly gloated over the ease of targeting the medical facilities and the speed with which the ransoms were paid to the group.” For more information on the TrickBot malware, please refer to this CIS article.
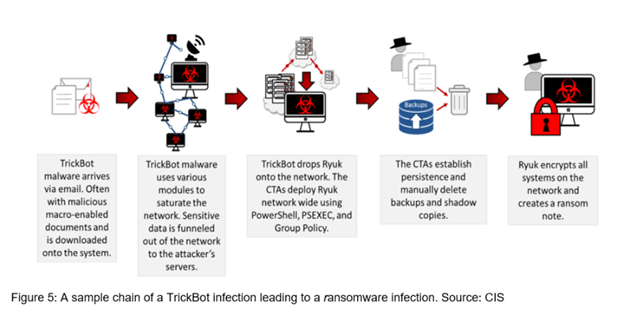
The indictment specifically calls out seven men, and also alleges their ties to Russian States Intelligence agencies. This move by the U.S. Department of the Treasury to sanction these individuals puts them on notice by making it illegal for anyone or any company (including banks, crypto exchanges, etc.) to engage in transactions with these individuals.
2. TruthFinder and Instant Checkmate Background Check Services Suffer Massive Breach
According to a recent report from BleepingComputer, a data breach reportedly affected the systems of American subscription-based background check firms TruthFinder and Instant Checkmate, exposing the personal information of 20.22 million users who utilized the services up to April 16, 2019, in a hacker forum. These are subscription based background check services. The hackers reportedly stole a 2019 backup database file filled with the data.

Both Instant Checkmate and Truthfinder confirmed the breaches after being questioned by BleepingComputer. Per the notices, the lists looked to include all customer accounts created between 2011 and 2019 in the leaked data.
3. Toyota’s Global Supplier Management Network System Pwn’ed by Security Researcher
Security researcher Eaton Zveare, said in a recent blog post that he acquired access to Toyota's Global Supplier Preparation Information Management System through a series of vulnerabilities and then reported it to Toyota.
Toyota's Global Supplier Preparation Information Management System is a web-based application used by Toyota personnel and their suppliers to organize projects, components, surveys, purchases, and other duties pertaining to the global Toyota supply chain.
The security researcher was able to access the site through a few modifications to the website code and then learned that he could grab Java Web Token’s (JWTs) for just about any user just by knowing their email address, no password required, which granted him read write access to the entire global user directory.
This looks to be another win for researchers and responsible disclosure, however, the headlines aren’t that great for Toyota. At least it was a white-hat hacker who found the flaw and not the bad guys.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
