Cyber Intelligence Weekly (March 10, 2024): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Before we get started on this week’s CIW, I’d like to highlight our vCISO led Security Team as a Service (StaaS)!
🌍 Introducing #STaaS by Echelon Risk + Cyber! 🛡️ 🔐 Elevate your #cybersecurity with our complete team of pros, led by a seasoned #vCISO. #STaaS is your strategic shield, offering 24/7 protection and navigating compliance complexities with ease. Echelon's #STaaS isn't just a service; it's your digital fortress in a world where #CyberSecurity is paramount. From complex compliance landscapes to defending against sophisticated threats, our team is your frontline defense. 🚫 Don't leave your cybersecurity to chance. Dive into how we can transform your cyber strategy and safeguard your future by reading our Cybersecurity Dive Press Release here: https://lnkd.in/eRc93wi2
Before we get started on this week’s CIW, I’d also like to highlight a solution from one of our strategic technology partners. This week, we highlight…
Dragos
Echelon Risk + Cyber proudly cultivates a diverse network of strategic relationships with leading vendors in the Cybersecurity Industry. These collaborations empower Echelon to deliver premium services to our clients through cutting-edge technology and valuable insights. In our ongoing effort to bring top-shelf knowledge, each week, we want to spotlight a distinguished partner solution offered at Echelon. This week’s focus is on the Dragos Platform.
The Dragos Platform stands as an advanced OT Cybersecurity technology solution, delivering comprehensive visibility of ICS/OT assets and threats. It encompasses four key tools: Asset Visibility & Inventory, Vulnerability Management, Threat Detection, and Investigation & Response. Let’s dive into each of the platform’s tools below.
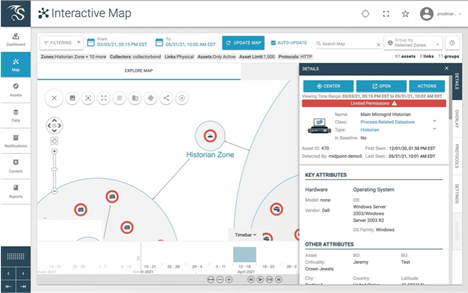
The Asset Inventory tool within the Dragos Platform offers profound contextual insights into ICS/OT network traffic and asset communication. This tool provides a complete lifecycle management capability, allowing for zoning by location, role, type, or subnets. Furthermore, it facilitates device filtering based on details such as vendor, firmware, and more.
Specifically tailored for ICS/OT devices, the Vulnerability Management tool provides full-cycle vulnerability management capabilities. This allows organizations to prioritize and address the most critical issues, thereby mitigating risks, minimizing downtime, and optimizing the allocation of cybersecurity resources. The Dragos Threat Intelligence team enhances this tool by providing risk levels for each vulnerability, along with real-time updates. Vulnerabilities can be managed in bulk or individually, with options for acceptance, mitigation, or remediation.
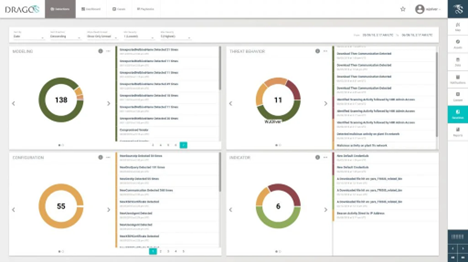
The Threat Detection Tool, an advanced threat analytics tool, employs state-of-the-art behavior-based analytics and aligns with MITRE ATT&CK for ICS. With continuous monitoring, this tool provides organizations with insights into configurations, modeling, indicators, and threat detections through a centralized dashboard.
Lastly, the Incident & Response tool serves as a Cyber Analyst-Focused Workbench, complete with step-by-step investigation playbooks. This tool enhances investigation efficiency by offering in-depth asset information, facilitating cross-team collaboration, and streamlining case management processes.
With the conclusion of the insight into The Dragos Platform, we look ahead with anticipation. Echelon Risk + Cyber remains dedicated to pushing the boundaries of cybersecurity innovation, forging partnerships that empower us to stay at the forefront of industry trends. If your organization is grappling with specific security challenges, allow Echelon to help alleviate the burden. Reach out to discuss how we might help your organization and stay tuned for more solution highlights in the weeks to come!
Away we go!
1. Healthcare in Crisis: Navigating the Aftermath of Change Healthcare Cyberattack
The healthcare industry is still grappling with the fallout of a major cyberattack on Change Healthcare, a medical payment processing subsidiary of UnitedHealth Group's Optum division. This attack, which has been described as the most significant against the U.S. healthcare system, has left doctors and hospitals in a dire situation, unable to process payments electronically. A recent news story highlights a dermatologist practice with the inability to bill electronically threatening the financial stability of healthcare providers.
Despite the attack, efforts to shift to paper claims processing are hindered by delays and reluctance from Medicare payment processors like Noridian Healthcare Solutions to accept them, exacerbating the crisis.
The cyberattack, suspected to be a ransomware incident, has underscored the healthcare system's vulnerability and the inadequacy of current protective measures. The American Hospital Association and other industry bodies are calling for more robust action from the federal government, critiquing the reliance on voluntary standards for network protection. The attack's impact is far-reaching, with independent practices and large health systems alike struggling to maintain operations amid the financial strain. The Federal government and UnitedHealth have announced relief measures, but healthcare providers argue these are insufficient to address the immediate financial challenges.
This incident has sparked a broader discussion about cybersecurity in healthcare, emphasizing the need for more funding and focus on safeguarding critical infrastructure. As the industry awaits more concrete solutions, the episode serves as a stark reminder of the ongoing threats posed by cybercriminals and the urgent need for a coordinated response to bolster the cybersecurity posture of the healthcare sector.
2. Midnight Blizzard Continues Cyber Siege on Microsoft
Microsoft has reported that it is still dealing with the effects of an ongoing cyber intrusion by Russian government hackers, specifically targeting the company's source code and internal systems. The group, known as Midnight Blizzard, APT29, or Cozy Bear, has been utilizing information gleaned from a previous hack last year to gain unauthorized access. In recent weeks, Microsoft has detected attempts by these hackers to exploit corporate email systems and other internal resources, including source code repositories. This revelation, shared in a blog post and a filing with the U.S. Securities and Exchange Commission, underscores the persistent threat posed by Midnight Blizzard, which has a history of significant cyber operations against high-profile targets.
The intrusion is part of a broader strategy by the hackers to understand and possibly undermine Microsoft's defenses, as evidenced by their initial breach of email accounts belonging to senior leadership and employees in key departments. Microsoft's analysis suggests that Midnight Blizzard is leveraging secret information acquired through their cyberespionage efforts to refine their attack strategies, including a tenfold increase in brute force account attacks. This sustained effort reflects a deep commitment of resources and coordination on the part of the hackers, who are affiliated with Russia’s Foreign Intelligence Service (SVR).
Midnight Blizzard's activities represent a continuation of Russia's sophisticated cyber warfare tactics, highlighting the ongoing challenges faced by global technology companies in protecting their intellectual property and internal communications. Microsoft's disclosure of these attacks serves as a reminder of the advanced capabilities of state-sponsored hackers and the importance of vigilance and cybersecurity resilience in countering these threats.
3. CISA Cybersecurity Breach, A Wake-Up Call for National Security
In a significant cybersecurity incident last month, the Cybersecurity and Infrastructure Security Agency (CISA) experienced a breach through vulnerabilities in Ivanti products, leading to the compromise of two of its systems. This breach prompted an immediate response from CISA, with the agency taking the affected systems offline to mitigate any potential damage. While the specific systems compromised were not officially disclosed, sources suggest they included critical infrastructure and chemical security assessment tools, highlighting the breach's potential impact on national security. The incident underscores the pervasive risk of cyber vulnerabilities across organizations, emphasizing the necessity for robust incident response plans.
This breach comes amidst broader concerns regarding vulnerabilities in Ivanti products, which have been exploited in the past by state-backed and other cyber threat actors. Ivanti, known for its IT management software widely used by governments worldwide, has faced scrutiny over security flaws that could allow remote access to sensitive information and system configurations. In response to the exploitation of these vulnerabilities, CISA has repeatedly urged organizations to assess the risks associated with continuing the operation of Ivanti Connect Secure and Ivanti Policy Secure gateways in their environments. The recent breach at CISA, despite the agency's role in promoting cybersecurity resilience, illustrates the complex and ongoing challenge of safeguarding digital infrastructure against sophisticated cyber threats.
The incident also prompted CISA to issue advisories warning of the exploitation of identified vulnerabilities and to advocate for increased vigilance and security measures. As cybercriminals continue to evolve their tactics, the breach at CISA serves as a critical reminder of the need for continuous improvement in cybersecurity defenses and the collective effort required to protect sensitive information and critical infrastructure from emerging cyber threats.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about


