Cyber Intelligence Weekly (Jan 2, 2022): Our Take on Three Things You Need to Know
Welcome to our weekly post where I will be sharing some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
You can also Subscribe to receive Cyber Intelligence Weekly in your inbox each week.
Before we get started on this week’s CIW, I’d like to highlight the great year we’ve had at Echelon. It is remarkable what a motivated team of people can do when centered around the same beliefs. I am so grateful and inspired by my talented teammates at Echelon. They strive to be the best at what they do with the goal of helping our clients succeed each and every day.
To our tremendous clients, valuable business partners, supporters, and fans of the firm…we THANK YOU for a wildly successful year. We are incredibly humbled and thankful, and we look forward to working with you in 2022!

Away we go!
1. Cheers to Y2K22! Should old acquaintance Microsoft Exchange be forgot, and never brought to mind?
Technology shops around the world got a New Year’s Day present when Microsoft Exchange ceased to perform the primary function it is there to perform, send and receive e-mail. The problem is reportedly to be only with on-site implementations of Exchange Server 2016 and Exchange Server 2019. Microsoft notes that, “The problem relates to a date check failure with the change of the new year and it not a failure of the AV engine itself. This is not an issue with malware scanning or the malware engine, and it is not a security-related issue. The version checking performed against the signature file is causing the malware engine to crash, resulting in messages being stuck in transport queues.”
Microsoft customers were left in the dark for nearly the balance of New Year’s Day while Microsoft scrambled to come up with a solution to the issue. Many Microsoft customers turned to Reddit and other online forums to share workarounds to get mail flowing while they waited for a more permanent solution from Microsoft. Early workarounds suggested by the community were to disable malware filtering (GASP).
Later on, that New Year’s Day, Microsoft published both an automated and manual solution to the problem that replaced the bad files causing the error within the system’s program utilities. More information on the fix can be found on the Microsoft Exchange Team Blog. The fix itself reportedly takes 30 minutes or so to run.

We all know that someone out there, some astute engineer at Microsoft saw this coming and was trying to warn everyone. To you sir/madam, we thank you and may your voice be heard next time!
2. Users of Popular Password Manager Targeted in Credential Stuffing Attacks
Several users of the popular password manager, LastPass, were targeted in a credential stuffing attack, the company said last week. The issue began when users started to receive blocked access emails, signaling someone was trying to attempt to login to their account.
Several members of the cybersecurity community postulated that there may have been a leak of LastPass user authentication credentials somewhere in the ecosystem. However, LastPass is saying that they believe the attack is nothing more than a credential stuffing attack. Credential stuffing occurs when the threat actor takes a collection of previously exposed authentication pairs (e.g.: email address and password) from previous breaches (e.g.: LinkedIn, Myspace, Adobe, etc.) and then uses bots to attempt to login to popular services and sites around the internet.
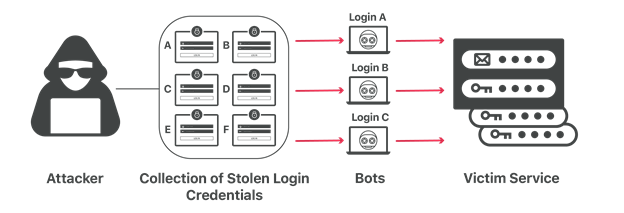
Photo Credit: Cloudflare.com
LastPass notes that, “These alerts were triggered due to LastPass’s ongoing efforts to defend its customers from bad actors and credential stuffing attempts. It is also important to remember that LastPass’ zero-knowledge security model means that at no time does LastPass store, have knowledge of, or have access to a user’s Master Password(s).” This is an important feature of any password manager; you get to set the security level by maintaining a very strong passphrase that salts the encryption function that encrypts all of your secrets.
As a user of LastPass myself, I highly suggest you consider the following configurations to further secure your account. For some of these, you will have to go to Account Settings -> General -> Click “Show Advanced Settings”:
- Enable multifactor authentication within the “Multifactor Options”
- Only allow logins from selected countries, check off only where you reside or travel to very frequently
- Check “Prohibit logins from Tor networks”
- Ensure “Disable Email Verification” is unchecked
3. Shutterfly Hit with Massive Ransomware Attack
If you are late to sending your Christmas cards and you like to send the fabled “New Year's Card”, you might be out of luck. Last week, news broke that photo services giant Shutterfly was recently hit with a massive ransomware attack that affected thousands of their devices and hundreds of their servers. Several of Shutterfly’s brands and many corporate services experienced interruptions.
The threat actors also reportedly stole corporate data during the incident as well. These double extortion attempts are unfortunately becoming more and more common as threat actors attempt to increase the likelihood that their misdeeds will pay off.
These double extortion types of attacks are popular with certain threat actor groups in particular. Computer news outlet BleepingComputer had much of the scoop, and they have reported that the Conti Group is behind this particular attack. In their report they show a screenshot of a ticking information bomb that is set to go live and release company confidential data if their ransom demands are not met.
It is very common for threat actors to be persistent in an environment for weeks or months prior to finally executing their ransomware attacks. During this time, they will steal as much data and other valuable information that they can in hopes of making their attacks successful. To avoid this, organizations should place more emphasis on detection of bad actors and their methods within their environments and catch them before things turn out like this.
