Cyber Intelligence Weekly (Jan 9, 2022): Our Take on Three Things You Need to Know
Welcome to our weekly post where I will be sharing some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
You can also Subscribe to receive Cyber Intelligence Weekly in your inbox each week.
Before we get started on this week’s CIW, I’d like to highlight a great webinar we have coming up later this week. The cybersecurity threats we face are constantly evolving — so if your penetration testing routine doesn't evolve as well, you are putting yourself at risk. Kick off the new year with a more creative approach to continuous pentesting.
Join this webinar — featuring Dan DeCloss from PlexTrac, Dan Desko and Dahvid Schloss from Echelon Risk + Cyber, and Nick Popovich — for a discussion on the ways that businesses can update their penetration testing routines to achieve iterative cycles that are continuous and flexible. These ideas will help you be more aware of blind spots and decrease your attack surface by prioritizing tests that mimic the most advanced and creative threat actors.
Attendees will learn specific recommendations for how to spice up your pentesting routine, practical tips for getting started without boiling the ocean, and much more.
Tune in live on Wednesday, January 12th at 10 am Pacific / 1 pm Eastern. Register today! Click HERE or on the photo below to sign up!

Away we go!
1. Commercial Antivirus Products Now Come with Free Crypto Miners! (Not Kidding)
I almost had to do a double take last week when I read the latest email alert from Brian Krebs. Krebs broke a story about popular consumer antivirus product Norton360 and how that it now comes with a crypto miner. I thought to myself that Norton was surely the result of another crafty supply chain attack and that attackers had snuck crypto mining software into their customer’s environments. I was bewildered to find out that the product actually had the crypto miner as an “opt-in” function that mines Ethereum while the customer’s computer is idle as long as it has the requisite horsepower to mine. What is wild about this, is that Norton actually takes a cut from the mining activity for themselves.
In similar news, it was later reported that Avira anti-virus is performing a similar function with their Avira Crypto option. Avira has 500 million users and was recently purchased by the same company that owns Norton.

In my opinion antivirus software should be detecting and killing crypto mining software, not installing it as a side hustle. Additionally, one of the major concerns here is how there will potentially be millions of unsophisticated users who will now be mining cryptocurrencies that know little to nothing about securing and/or protecting their online funds or their computers.
2. Stalking/Privacy Concerns Abound with Apple AirTag Device
Apple’s AirTag devices which are popular amongst the forgetful and disorganized sort, have also been very popular devices for stalkers. The relatively inexpensive AirTags can easily be slipped into someone’s pocket, bag, car, etc. and used to track them.
Some of these concerns have been brought up as early as last May by a Washington Post journalist. Most recently, Apple AirTags were used in a frightening way to stalk model Brooks Nader in New York City. The Engadget piece linked above tells a story about how model Brooks Nader was waiting for someone in a crowded bar in Tribeca with her coat on her chair behind her and then had her movements tracked for several hours after that by a rogue AirTag.
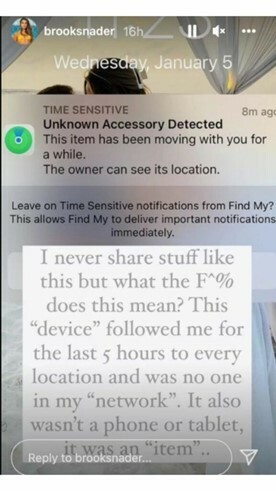
Nader noticed that her iPhone alerted her of the unknown accessory as seen in the screenshot from her Instagram account above. Apple rolled out this iPhone notification to inform users that they may be traveling with an unauthorized tracker on them earlier last year. Unfortunately this alert does not apply to half of the population that uses Android devices. To combat this shortcoming, Apple has rolled out an Android App, Tracker Detect, that is designed to find and alert users of unwanted trackers. However, the user must know to download this application, it is not automatic like on the Apple iOS.
This issue with Nader is not an isolated incident by any means, there have been reports of thieves using the technology to track and steal high end cars. It will be interesting to follow this story and see how Apple reacts and responds as these stories continue to surface and highlight the privacy and security concerns these devices cause. It is hard to see how Apple can engineer themselves out of this one as there seem to be many situations and edge cases that can’t be controlled.
3. Russian IT Exec Recently Captured for Insider Trading May Have Deep Kremlin Ties
Vladislav Klyushin of Moscow, Russia, accused of insider trading on information gained from elicit hacking activities was arrested earlier this year while traveling on holiday in Sion, Switzerland on March 21, 2021, and was recently extradited to the United States on December 18, 2021. According to the indictment, Klyushin and his coconspirators hacked into the networks of filing agents to obtain material financial information before it became public in order to front run the announcements and enrich themselves with their insider information.
A recent report from Bloomberg intimates that Klyushin is much more than a good capture from a securities fraud perspective. The Bloomberg piece paints Klyushin as a close insider to Moscow political elites and as a useful source of information for US officials. Klyushin ran a cybersecurity technology company, M-13, that supposedly worked with the Russian government’s top echelons. It was also reported that Klyushin has access to information related to the hacking of Democratic Party servers during the 2016 election that could prove who was behind the attacks.
It will be interesting to watch this story unfold as Klyushin makes his way through the US justice system, and if strikes any deals for giving up incriminating information on his homeland and their supposed hacking activities over time. If anything can be learned from this story, it is that the FBI and the Federal justice system always do their part to ensure that bad actors meet the consequences they deserve when they travel to countries with friendly extradition treaties with the United States.
