Cyber Intelligence Weekly (January 1, 2023): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Also, we are always looking for great people to join our team. If you know anyone who fits the profiles for any of our open positions, drop me a line and let us know!
Before we get started on this week’s CIW, I’d like to highlight our Top 10 Cybersecurity Articles of 2022. We’ve had a lot of great thought leadership delivered by our professional staff this past year, and this is a summary of the most popular articles that we released! Happy reading!

Away we go!
1. The LastPass Hack, What You Need to Know
On December 22, 2022, the LastPass team updated their blog with further shocking details on the incident they announced back in August of 2022. Since then, there has been a ton of information flying around out there about the LastPass breach, and I've received a lot of questions about it, so I thought I'd write up some quick thoughts. We can only operate with the information we have, so I will add the caveat that we are acting on the information provided by LastPass to date. Here is a summary of the latest:
Here is what we know:
- Threat actors obtained LastPass cloud storage access keys and dual storage container decryption keys and were able to steal significant amounts of customer data.
- Threat actors did steal unencrypted LastPass user meta data (e.g., company name, end-user name, billing address, telephone numbers and IP addresses of users).
- Threat actors also stole encrypted LastPass user vaults / secrets data (e.g., usernames and passwords).
- The vault / secret data (e.g., website usernames and passwords, secure notes, and form-filled data) is encrypted with AES-256 encryption that is encrypted with a key that is derived from the users' master password.
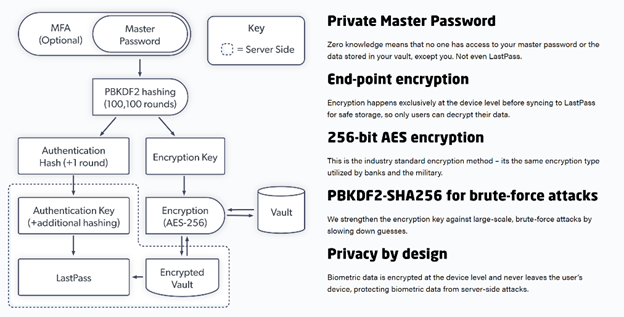
The important thing to remember is that your LastPass Master Password is not known to LastPass. The LastPass encryption functions rely on your Master Password, and all encryption is done client side (on your device). However, this places the onus on the user to set a strong Master Password. Your Master Password essentially serves as a unique seed that then goes through over 100,000 rounds of PBKDF2 hashing to create the actual encryption key that is used to encrypt your vault. The LastPass vault / secret data is encrypted using AES-256 encryption.
With a strong Master Password, it would take an inordinate amount of time for a threat actor to brute force your Master Password and successfully reverse the encryption. But again, this all assumes that Master Password is strong and not easily guessable.
What To Do if You Use LastPass:
- If your LastPass Master Password is weak (e.g., less than 12 characters), your account is at much higher risk and action should be taken immediately.
- If your LastPass Master Password is re-used elsewhere, your account is at much higher risk and action should be taken immediately.
- Even if you believe that your LastPass Master Password was very strong, I’d recommend resetting your passwords. I’d start with the most critical ones that could pose the most harm should a threat actor get ahold of them (e.g., financial sites, healthcare portals, etc.).
- While you are at it changing those passwords, ensure two-factor authentication is on and set for the accounts that have the option to. This adds a whole additional state of complexity to keep the bad guys out.
- Be on the lookout for advanced spear phishing attacks. With the useful knowledge available through the LastPass metadata stolen, you may be targeted by spear phishers more readily.
- Consider other password managers on the market and understand if they are a good fit for you. There are several other options out there, some are cloud based, some are not. I would encourage you to think about all of these options, understand what you need, and what their security measures are before making a move.
2. The Worst Hacks of 2022
Our friends at Wired put out a good summary of the worst hacks of the prior year. 2022 was a wild year, and by all accounts, 2023 should be pretty interesting as well.

Some of the biggest and most notable hacks of 2022 that they outline include:
- Russia’s hacking of Ukraine
- Twilio and 0ktapus
- A slew of ransomware attacks
- The Lapsus$ gang
- LastPass
- Twitter as an honorable mention…
Let’s use these stories as learning opportunities and learn from the hard times of others so we can avoid these same types of outcomes in 2023 and beyond.
3. The Equifax Breach Settlement Offer is Real, For Now
Great reporting by Brian Krebs, who released an article about a recent settlement offer from credit reporting giant Equifax. Millions of people have been receiving email or mail offers from Equifax to cash in on their data being part of their huge and infamous data breach back in 2017.

Equifax agreed to a settlement of nearly half a billion dollars back in 2019 to help those affected by the breach. The settlement funds that are being distributed are miniscule in most cases, and could be much more substantial for those who can prove that they were deeply affected and spent an inordinate amount of time remedying their situation due to the breach. Krebs points out that he and many others are now worried about phishers and scammers that may now use this settlement news to further scam people, so be on the lookout for fake settlement claims that seem too good to be true!
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
