Cyber Intelligence Weekly (January 22, 2023): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Also, we are always looking for great people to join our team. If you know anyone who fits the profiles for any of our open positions, drop me a line and let me know!
Before we get started on this week’s CIW, I’d like to highlight an article from CyberNews that our very own Paul Matvey was quoted in. The article entitled, “LastPass hack aftermath: can we trust password managers?” is a great op-ed debating the trust or lack thereof password managers have these days given all the recent issues that LastPass has gone through. Enjoy the read!

Away we go!
1. New T-Mobile Breach Affects 37 Million Accounts
Brian Krebs released another bombshell news story last week, when he highlighted a new T-Mobile breach that affected upwards of 37 million customer accounts. Per an SEC filing by T-Mobile on the matter, “On January 5, 2023, T-Mobile US, Inc. (the “Company,” “we,” or “our”) identified that a bad actor was obtaining data through a single Application Programming Interface (“API”) without authorization. We promptly commenced an investigation with external cybersecurity experts and within a day of learning of the malicious activity, we were able to trace the source of the malicious activity and stop it.”

T-Mobile’s investigation suggests that starting on or around November 25, 2022, is when the malicious actor first retrieved data through the impacted API. The threat actor was able to gain access to sensitive customer details through the breach including, name, billing address, email, phone number, date of birth, T-Mobile account number and information such as the number of lines on the account and plan features.
All of this comes on the heels of a massive breach from 2021 that has been settled and is currently in the midst of being paid out. Despite all of these massive breaches, T-Mobile continues to be a leader in the mobile space. It will be interesting to follow the fallout of this latest breach.
2. Thousands of Norton LifeLock Customer Accounts Breached
TechCrunch originally broke the news last week that Norton LifeLock, which is a subsidiary of Gen Digital, suffered what appeared to be a credential stuffing style of attack whereby hackers guess their way into thousands of Norton LifeLock customer accounts.
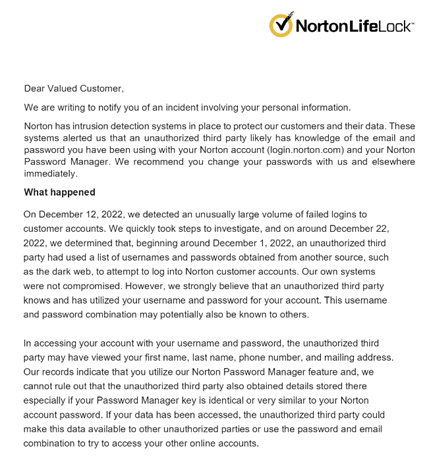
Vermont Attorney General Web Notice
In addition to accessing these customer’s accounts, there is real concern that the threat actor may have managed the password manager tools/feature that these customers also use from Norton. Password managers have been under attack as of late in several other notable breaches, and this is an extension of that trend.
3. Third-Party Administrator, Bay Bridge, Notifies Patients of Data Breach
More than 251,000 patients are just now being informed that their data was taken following a network compromise in September 2022 by Austin, Texas based Bay Bridge Administrators (BBA), a third-party administrator.
They noted that on September 5, a network interruption was initially noticed, prompting BBA to take action and liaise with an outside cybersecurity company to investigate the matter. The attacker was able to exfiltrate data from the network on September 3 thanks to access they had secured more than a week before being found, according to forensics.
BBA attributes the protracted delay in notifying patients to a "thorough inquiry" that was completed on December 5. In accordance with the Health Insurance Portability and Accountability Act (HIPAA), covered entities must notify patients of potential data exposure within 60 days and without undue delay. Information exposed during this breach may have included name and Social Security number, driver’s license or state identification number, date of birth, medical information, and health insurance information. For an example notice, you can view this letter to the Attorney General of New Hampshire. Private health records continue to be a large target of attackers due to the breadth of personal information recorded.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
