Cyber Intelligence Weekly (June 13, 2022): Our Take on Three Things You Need to Know
Welcome to our weekly post where I will be sharing some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
You can also Subscribe to receive Cyber Intelligence Weekly in your inbox each week.
Before we get started on this week’s CIW, I’d like to highlight that our very own Offensive Security Lead, Dahvid Schloss will be teaching a two day immersive malware development course at DEFCON 2022! Tickets are on sale now in the link above as well as here, become a malware pro this summer with Dahvid!

Away we go!
1. NSA, CISA, and FBI Expose PRC State-Sponsored Exploitation of Network Providers, Devices
Last week the National Security Agency (NSA), Cybersecurity and Infrastructure Security Agency (CISA), and Federal Bureau of Investigation (FBI) released a Cybersecurity Advisory that outlines how the People’s Republic of China (PRC) state-sponsored threat actors have been targeting major telecommunications companies and network services providers.
They go on to describe how the PRC state-sponsored cyber actors are readily exploiting vulnerabilities to compromise unpatched network devices. The report notes that, “These cyber actors are also consistently evolving and adapting tactics to bypass defenses. NSA, CISA, and the FBI have observed state-sponsored cyber actors monitoring network defenders’ accounts and actions, and then modifying their ongoing campaign as needed to remain undetected. Cyber actors have modified their infrastructure and toolsets immediately following the release of information related to their ongoing campaigns.”
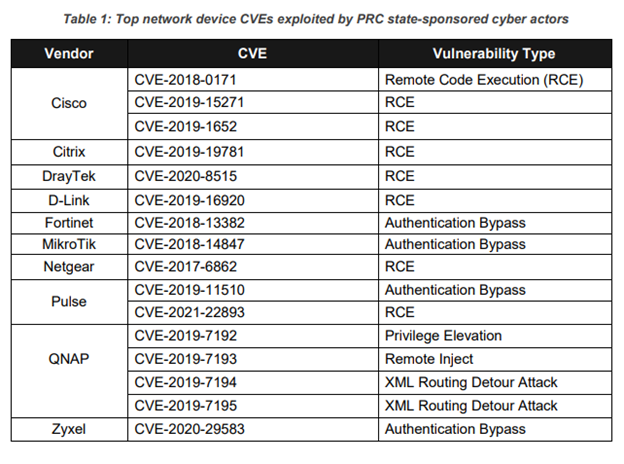
The report also outlines the top network device vulnerabilities that are being exploited.
Most notably, the report details how the PRC threat actors will configure port mirroring to copy all network traffic to a local interface, then ship it all out of the network to their own infrastructure.
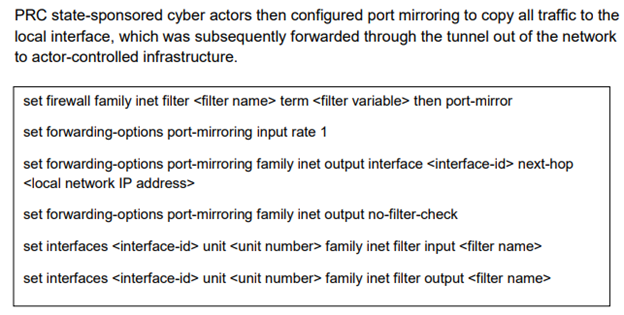
Scary stuff right there, to be sure. It is never good to see a politically motivated actor establishing this type of foothold in critical data infrastructure. As in most advisories from CISA and others, the remediations noted include patching and updating systems, segmenting networks, enforcing MFA, implementing strict password requirements, etc.
2. Back From the Dead, Emotet Returns in 2022
When I hear the word Emotet, it always sends chills down my spine. I have personally witnessed that malware wreak havoc across a number of organizations in the past. Last week, Deep Instinct, a cyber protection software company, released a report on Emotet and its rise again in 2022.
But wait a minute you say, didn’t Emotet get busted?! Yes, that is the same Emotet that the Justice Department took down in January of 2021. However, we all known you can’t keep a good cybercriminal down for long. Like a hydra, you cut off one limb, and it will be replaced by two more.

The Deep Instinct report notes that for Emotet deliver there has been a 900% increase in the use of Microsoft Excel macros compared to what they had observed in Q4 2021. Other key findings include the fact that Emotet is now using 64bit shell code as well as more advanced PowerShell and active scripts.
3. Follina Exploiters Growing by the Day, Still No Patch from Microsoft
While organizations around the world are waiting for a patch from Microsoft for CVE-2022-30190, malware operators and ransomware gangs are licking their chops at the ripe opportunities in the wild today to exploit organizations who haven’t protected themselves adequately.

As noted in this tweet from Proofpoint, they are seeing the Follina vulnerability used as a mechanism to deliver Qbot. The Qbot malware can be used by threat actors to steal keystrokes and other sensitive information from infected machines.
We continue to highly recommend that organizations follow the Microsoft noted workaround to disable the vulnerable service until there is a viable patch that closes this vulnerability.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
