Cyber Intelligence Weekly (May 21, 2023): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Before we get started on this week’s CIW, I’d like to highlight an article that I recently wrote that explores the benefits of adversarial-based red teaming with the TIBER-EU Framework, a comprehensive methodology developed by the European Central Bank. In this article, you'll learn about the key differences between traditional penetration testing and adversarial-based red teaming, the components of the TIBER-EU Framework, and recommendations for implementing this approach.
Read the full article here: https://lnkd.in/giC3_pwi

Away we go!
- KeePass Vulnerability Exposes Master Passwords: A Critical Security Risk
A recently disclosed vulnerability in the popular opensource password manager KeePass has raised concerns about the theft of master passwords. The flaw, designated CVE-2023-32784, allows an attacker to obtain the plaintext master password from a locked user workspace. The proof-of-concept exploit, shared on GitHub by user "Vdohney," demonstrated the ability to recover the master password from KeePass' memory without requiring code execution. The exploit works regardless of whether the memory originates from a process dump, RAM dump, hibernation file, or swap file, and it remains effective even if KeePass is no longer running.

The discovery of this vulnerability has alarmed the cybersecurity community as the theft of a master password poses the worst-case scenario for a password manager. The master password can provide unauthorized access to all stored account logins. The severity of the flaw depends on the individual user's circumstances. While an existing malware infection may not be significantly affected, the vulnerability could be detrimental if someone gains access to the computer and conducts forensic analysis. Dominik Reichl, the developer of KeePass, acknowledged the issue and stated that fixes would be included in the upcoming release of KeePass version 2.54, expected within the next two months.
This incident adds to a growing list of serious threats concerning password managers, with notable examples including the LastPass breaches in the previous year. Users of KeePass are advised to stay updated with the latest releases to mitigate the risk associated with this vulnerability.
2. Unveiling the Risk: Police-Auctioned Cell Phones and Re-Victimization
A new blog post from Brian Krebs highlights a study conducted by researchers at the University of Maryland that have found that numerous smartphones seized by police in the United States are being auctioned online without having their data erased first. This practice poses a significant risk, as it can lead to re-victimization of individuals whose personal information is stored on these devices. PropertyRoom.com, the largest online marketplace for items seized in law enforcement investigations, has announced that it will now ensure that all phones sold through its platform are data-wiped prior to auction.
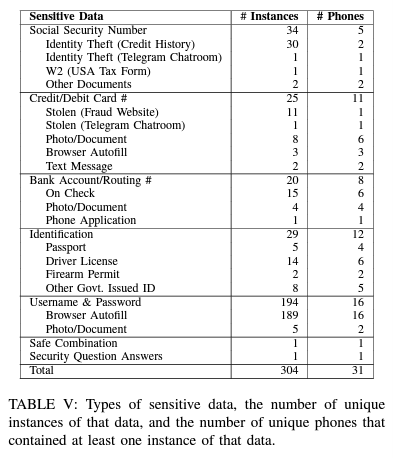
The researchers purchased 228 smartphones from PropertyRoom.com and discovered that 49 of them had no PIN or passcode. Additionally, they were able to guess an additional 11 PINs by using common patterns. These phones could contain sensitive data such as text messages, pictures, emails, browsing history, and location history. In some cases, they also contained significant amounts of data related to criminal activities, including victims' information.
The researchers highlighted the importance of addressing this issue, as it is unclear how these phones ended up for sale on PropertyRoom.com without being wiped first. State laws regarding lost or stolen property often result in these devices being treated similarly to civil asset forfeiture and being sold to resellers. The study raises concerns about the protection of personal information and the potential misuse of these devices by buyers. While PropertyRoom.com has now implemented data-wiping measures, further steps may be necessary to ensure the privacy and security of individuals whose devices are seized by law enforcement.
3. Toyota Japan's Data Breach: Millions of Vehicle Location Data Exposed
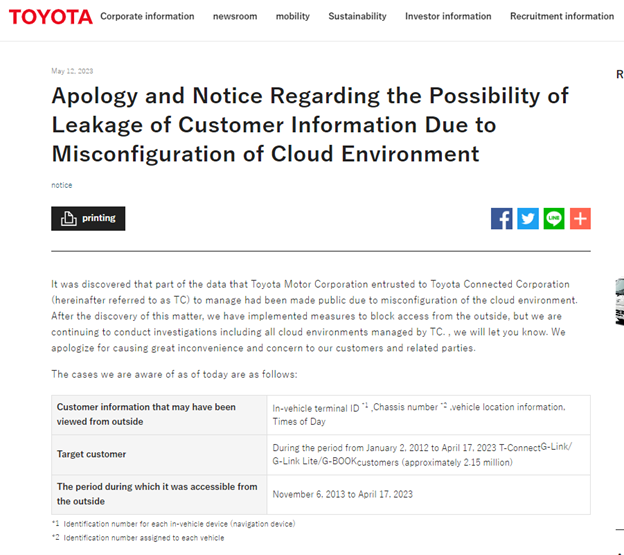
Toyota Japan has issued an apology after revealing that millions of customers' vehicle details, including location data, were exposed on the public internet for a decade. The car manufacturer disclosed that a "cloud misconfiguration" in April resulted in the personal and vehicle information of approximately 2.15 million customers being left vulnerable. The exposed data includes registered email addresses, vehicle-unique chassis and navigation terminal numbers, vehicle locations with timestamps, and videos recorded by the vehicle's drive recorder.
The data breach originated from Toyota's Connected Cloud and was initially exposed in November 2013. However, the incident only affects vehicles in Japan. Toyota's connected service offers features such as vehicle information, in-car entertainment, and emergency notifications in case of accidents or breakdowns. The company claims that the data was secured, and there have been no reports of unauthorized access or malicious use. However, it remains unclear if Toyota has the necessary logging in place to determine if any data was exfiltrated. Toyota has pledged to implement improved monitoring systems for its cloud infrastructure to prevent future breaches.
This is not the first time Toyota has faced a data exposure issue. In 2022, the company admitted that around 300,000 customer email addresses had been exposed for nearly five years due to a subcontractor inadvertently uploading a portion of the company's source code to the internet, including a private key containing customer email addresses. These incidents highlight the importance of robust data security measures and vigilant monitoring to protect customer information from unauthorized access and potential misuse.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
