Cyber Intelligence Weekly (June 26, 2022): Our Take on Three Things You Need to Know
Welcome to our weekly post where I will be sharing some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
You can also Subscribe to receive Cyber Intelligence Weekly in your inbox each week.
Before we get started on this week’s CIW, I’d like to highlight this great presentation that our very own Ross Flynn gave at BSides Buffalo, “Say Hi to the New Guy: How Diverse Backgrounds Can Mature Your Security Program.”

Away we go!
1. The TikTok Tapes, Leaked Meeting Recordings Show US User Data Accessed Regularly in China
TikTok has long responded to data privacy concerns by stating that information gathered on its users in the United States, remains in the United States. However, new information leaked from the company suggests that the opposite is true.

The recordings reportedly contain several statements from many different TikTok employees indicating that engineers in China had unfettered access to US user data between September 2021 and January 2022, at the very least. In the files, a member of TikTok’s Trust and Safety department purportedly said that “everything is seen in China.” All of this newly leaked information is contrary to the sworn testimony in October 2021 from a Senate hearing where TikTok executives stated that a “world-renowned, US-based security team” is the one who decides who gets access to this data.
The obvious concern is that Chinese based ByteDance, who owns TikTok, would be subject to the whims of the Chinese Communist Party and that the data of millions of Americans that use the platform could be shared with the authoritarian regime.
Remember, if the app is free, you are the product.
2. Microsoft Releases New Report; Defending Ukraine, Early Lessons from the Cyber War
Each war in history reflects the use of the technology available at that time as countries that wage war uses the latest and greatest technology to enable their efforts. In a recent report from Microsoft, they contend that the Russian war on Ukraine is no different. This time around, the technology du jour is cyber enabled warfare.
Microsoft’s report outlines three distinct but often coordinated areas of effort, destructive cyber attacks within Ukraine, network penetration efforts and espionage outside of the Ukraine, and cyber enabled influence operations targeting people all over the world.

The Microsoft report also outlines how Russian cyber operations often coincide with major physical or kinetic based operations within Ukraine. Similar to military missions of the past where a country may strike from the sea and land, Russia is using cyber warfare as another pillar to buttress its efforts.
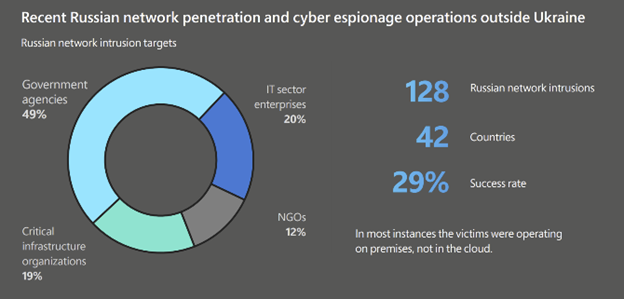
Microsoft has also reported Russian network intrusion efforts on 128 target entities, across 42 countries outside the Ukraine so far. Of the 128 targeted institutions, 128 of them have been government entities that are playing critical roles in the West’s response to the war on Ukraine. American targets lead the way, per the report, garnering 12% of the targeted entities. Following America, the other most closely targeted entities are in NATO supporting countries like Poland, who plays a crucial role in the delivery of aid to Ukraine.
Today’s war has clearly evolved greatly with the advance of cyber capabilities. Cloud resources and major technology companies also play a huge role in the active defense of countries from a cybersecurity perspective. This isn’t something that I’d think I would’ve had to say before, but ensuring that your major technology partners align with your political views is likely a very important factor today.
3. Users Being Targeted by New Zero-Day Spyware, Hermit
Google’s Project Zero and their Threat Analysis Group (TAG) have been monitoring and tracking spyware makers and their customers for years. Just recently they put out a report detailing capabilities of a group, RCS Labs, an Italian vendor that they say uses a combination of tactics to target mobile users. This follows a report from Lookout a couple weeks ago that originally uncovered the spyware.

This malware campaign appears to be using drive by downloads as its main source of target infection. TAG notes that all campaigns that they observed started with a unique link sent to the target mobile user. They also noted that they believe that the actors worked with the target’s ISP to disable the target’s mobile data connectivity. They would then send a malicious link via SMS asking the target to install an application to recover their data connectivity.
Ultimately, the malware is highly sophisticated spyware/surveillanceware with “enterprise-grade” capabilities to collect and transmit data. While these vendors who sell this spyware supposedly only sell it to organizations with legitimate interests, we all know that the ability for this type of software to be abused is very high.
To protect against this type of spyware or malware in general, be sure to follow these best practices:
- Update your phone and apps on a regular basis
- Never click on unknown or unexpected links, always go to a browser and visit the site directly yourself
- Never install unknown or unprovoked apps
- Use a mobile security solution to protect your phone
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
