Cyber Intelligence Weekly (June 18, 2023): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Before we get started on this week’s CIW, I’d like to highlight our new vCISO Practice Director, Paul Interval! Paul comes to us with tremendous experience leading, managing and growing a vCISO practice for a large MSSP, based out of New York City. Paul is passionate about improving our client’s security posture in a meaningful way and evolving our practice into something very special. Please connect with Paul today: https://www.linkedin.com/in/pinterval/

Away we go!
1. MOVEit Transfer Customers Warned of NEW Critical Flaw, Government Agencies Hacked
The news keeps coming from Progress Software Corporation as they have recently issued a warning to their MOVEit Transfer customers about a new SQL injection vulnerability that could potentially lead to unauthorized access and escalated privileges. The new flaw, identified as CVE-2023-35708, poses a significant security risk, prompting the company to release security patches to address the issue. In response, customers are advised to restrict all HTTP access to their environments and apply the necessary patches to safeguard their systems. This comes in addition to the news that the U.S. government has confirmed that multiple federal agencies have fallen victim to cyberattacks due to the buggy software.
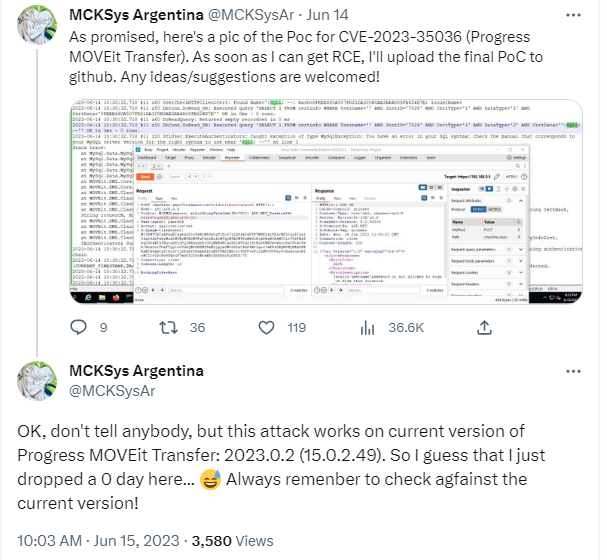
While restricting HTTP access may prevent users from logging into their accounts through the web interface, file transfers will remain unaffected as protocols such as SFTP and FTP/s will continue to operate as expected. Administrators can access MOVEit Transfer by connecting to the Windows server via remote desktop and accessing https://localhost/. By promptly implementing the provided security patches, MOVEit Transfer customers can effectively safeguard their environments and minimize the risk of exploitation.
The emergence of the CVE-2023-35708 vulnerability in MOVEit Transfer underscores the importance of robust cybersecurity measures, such as detailed code review for security vulnerabilities. Progress has taken swift action by releasing security patches to address the flaw and is urging all affected customers to apply these patches promptly.
2. Unsolicited Smartwatches Pose Cybersecurity Threat to Service Members
A recent report from the Army Criminal Investigation Division (CID) has raised concerns about service members across the military receiving unsolicited smartwatches in the mail. These smartwatches, upon use, automatically connect to Wi-Fi and begin accessing cell phones without any prompt, potentially compromising sensitive user data
The report also highlights the presence of malware in these devices, which can grant the sender unauthorized access to various personal information, including banking details, contacts, usernames, and passwords. Moreover, the malware may also enable unauthorized actors to access voice recordings and camera functions, allowing them to eavesdrop on conversations and gain access to accounts associated with the smartwatches.
This alarming practice of unsolicited smartwatches being sent to individuals is attributed to a deception tactic known as "brushing." The intention behind brushing is to distribute products, often counterfeit, to unsuspecting recipients via mail, with the goal of generating positive reviews in the receivers' names. This tactic allows companies to compete with established products by fabricating favorable reviews through the use of unwitting recipients. However, the risk posed by these unsolicited smartwatches goes beyond false reviews, as they contain malware capable of compromising users' privacy and security.
The Army CID report serves as a crucial warning to service members and the wider intelligence and business community about the potential risks associated with unsolicited electronics. It is imperative to exercise caution when receiving such packages and refrain from using or connecting these devices to personal devices or networks. In order to protect personal data and maintain cybersecurity, it is recommended to report any instances of receiving unsolicited smartwatches to the appropriate authorities.
3. SEC Delays Final Rule on Four-Day Breach Notification for Public Companies
The Securities and Exchange Commission (SEC) has announced a delay in finalizing new regulations that would require public companies to promptly report cybersecurity breaches. The proposed rule, which initially aimed for a four-day breach notification period, is now expected to be finalized no earlier than October this year. The decision comes after industry trade groups and public interest organizations raised concerns over the rule's language and potential duplication with other cybersecurity requirements. This delay reflects the challenges in striking a balance between timely breach disclosure and the need for thorough investigation and containment.
The SEC's decision to postpone the final rule on breach notification for public companies has sparked a range of reactions. Various stakeholders, including the Information Technology Industry Council (ITI), cybersecurity vendors, and public interest groups, expressed concerns regarding the proposed rule's wording and its alignment with other cybersecurity regulations. Of particular concern is the potential duplication with the forthcoming 2022 Cyber Incident Reporting for Critical Infrastructure Act (CIRCIA), which requires critical infrastructure entities to report breaches within three days to the Cybersecurity and Infrastructure Security Agency (CISA). The delay provides an opportunity for further deliberation and collaboration among industry experts to ensure streamlined and effective breach notification procedures.
Another prominent point of contention is the four-day disclosure period, which some argue might lead to unintended consequences. Some critics note that the disclosure of an uncontained cyber incident could potentially escalate attacker behavior and lead to additional harm for investors. It has been suggested that a 30-day notification period would provide sufficient time for comprehensive investigation and remediation of cyber incidents, reducing the risk of copycat attacks and further harm to stakeholders. However, others have expressed concerns that the proposed four-day timeframe might hinder a company's primary obligation to remediate the breach and thoroughly understand its nature and impact. Striking a balance between swift notification and comprehensive response remains a key challenge for regulatory authorities.
The SEC's decision to delay the final rule on breach notification for public companies until October reflects the complexities surrounding effective cybersecurity regulation. Balancing the need for timely breach disclosure with comprehensive incident investigation and containment remains a challenge. Industry stakeholders, regulatory bodies, and public interest groups must collaborate to address concerns over duplications, disclosure periods, and the impact on national security. By fostering dialogue and considering diverse perspectives, regulators can develop a robust and practical framework for breach notification that protects stakeholders' interests while encouraging proactive cybersecurity measures.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about

