Cyber Intelligence Weekly (June 5, 2022): Our Take on Three Things You Need to Know
Welcome to our weekly post where I will be sharing some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
You can also Subscribe to receive Cyber Intelligence Weekly in your inbox each week.
Before we get started on this week’s CIW, I’d like to highlight that our very own Dahvid Schloss and Paul Matvey will be out at the RSA Conference this week! It is always great to get to RSA and learn about the latest and greatest in the cyber world and see all of our friends in the expo halls. Drop them a line on LinkedIn and look for them to meetup in person!

Away we go!
1. Microsoft “Follina” Zero-Day Vulnerability Causing Worldwide Concern
Earlier last week, security researchers warned that a flaw in Microsoft’s Support Diagnostic Tool (MSDT) could be exploited by simply opening a Word document. CISA has put out an alert, stating, “A remote, unauthenticated attacker could exploit this vulnerability to take control of an affected system. Microsoft has reported active exploitation of this vulnerability in the wild.” Microsoft has released a workaround while they work on a patch. The workaround can be found here, and consists of deleting the “ms-msdt” registry key. The vulnerability is currently present in all supported versions of Windows and can be exploited through Microsoft Office 365, Office 2013 through 2019, Office 2021, and Office ProPlus.
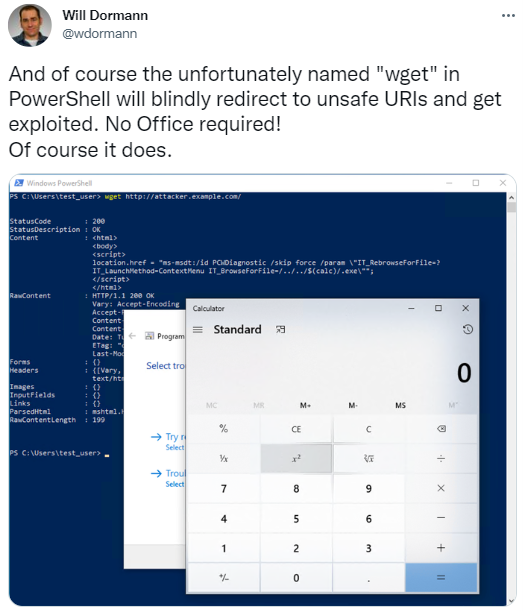
The vulnerability also has been reported to work whether or not Office is installed. Using “wget” in PowerShell will blindly execute any code via MSDT, no MS Office necessary. This type of vulnerability is so widely available, it is obviously very concerning. Also very concerning is just how easy it seems to exploit.
We highly recommend implementing the Microsoft noted workaround, and we also recommend watching for updates and patches that will be forthcoming from them. We also suggest checking with your anti-malware tooling and ensuring that the prevention and detection of these types of attacks, such as suspicious process blocking is enabled and handled appropriately. For example, our partner, CrowdStrike has outlined just how they prevent and stop these types of attacks in their blog.
2. Massive Cyberattacks Crippling Costa Rica
Costa Rica, a rugged, rain forested Central American country is known for its beautiful coastlines on the Caribbean and Pacific. Most recently, it is also known for a massive cyber-attack that has brought down several government services for the country.

Costa Rica declared a national emergency in May due to a crippling ransomware attack that was attributed to the Conti ransomware gang. Last week, the Hive ransomware gang targeted Costa Rica’s national health service as reported by Brian Krebs. Krebs also suggests in his article how Conti and the Hive groups are working together. Over 30 government agencies have been targeted and these agencies and critical services have been reduced to pen and paper.
The government refused to pay the original requested ransom in early May, which was $15 million dollars. At this point, the $15 million seems like a drop in the bucket compared to the amount of money the government, and the rest of country, is supposed losing due to the attacks. Per a recent report, “In the first two days of the attack alone, the Costa Rican Chamber of Foreign Commerce estimated losses of over $125 million. The economy is hemorrhaging an estimated $30 million a day since, according to congresswoman Gloria Navas.”
3. Several Universities Put on Watch, Credentials Offered for Sale
The FBI recently put several Universities on notice as they have informed a number of academic institutions that their credentials are for sale on public and dark web forums. They warn that the exposure of sensitive credentials or administrative credentials can be very damaging for a number of obvious reasons.
Higher education continues to be a heavily targeted industry for many reasons. Higher education institutions often face the challenge of open and accessible systems for purposes of educational freedom and research falling out of balance with locking down systems for cybersecurity protection reasons. This recent warning from the FBI notes that they have seen a big uptick on dark web forums of stolen credentials from higher education institutions that can be used for brute force attacks, credentials stuffing and more.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
