Cyber Intelligence Weekly (April 21, 2024): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Before we get started on this week’s CIW, I’d like to highlight our Security Team as a Service (STaaS) offering. Cybersecurity is a team sport. That's why we tackle our clients' biggest challenges with all our experts at their disposal.
Working together, with one goal in mind: leveling up our clients' cybersecurity posture and protection from threats, so they can focus on running the business.
Interested in learning more about how we can help safeguard your operations? Learn more: https://lnkd.in/d54Pawt5

Solution Partner Highlight - Abnormal Inbound Email Security
Echelon Risk + Cyber proudly cultivates a diverse network of strategic relationships with leading vendors in the cybersecurity industry. These collaborations empower Echelon to deliver premium services to our clients through cutting-edge technology and valuable insights. In our ongoing effort to bring top-shelf knowledge, each week, we want to spotlight a distinguished partner solution offered at Echelon. This week’s focus is on Abnormal’s Email Security Solution.
Abnormal’s Platform offers Inbound Email Security as its core product, leveraging behavioral artificial intelligence (AI) to combat a range of increasingly complex and costly email attacks. With features like detecting novel threats, automatically remediating malicious emails, and simplifying complex attack explanations, Abnormal ensures robust protection.
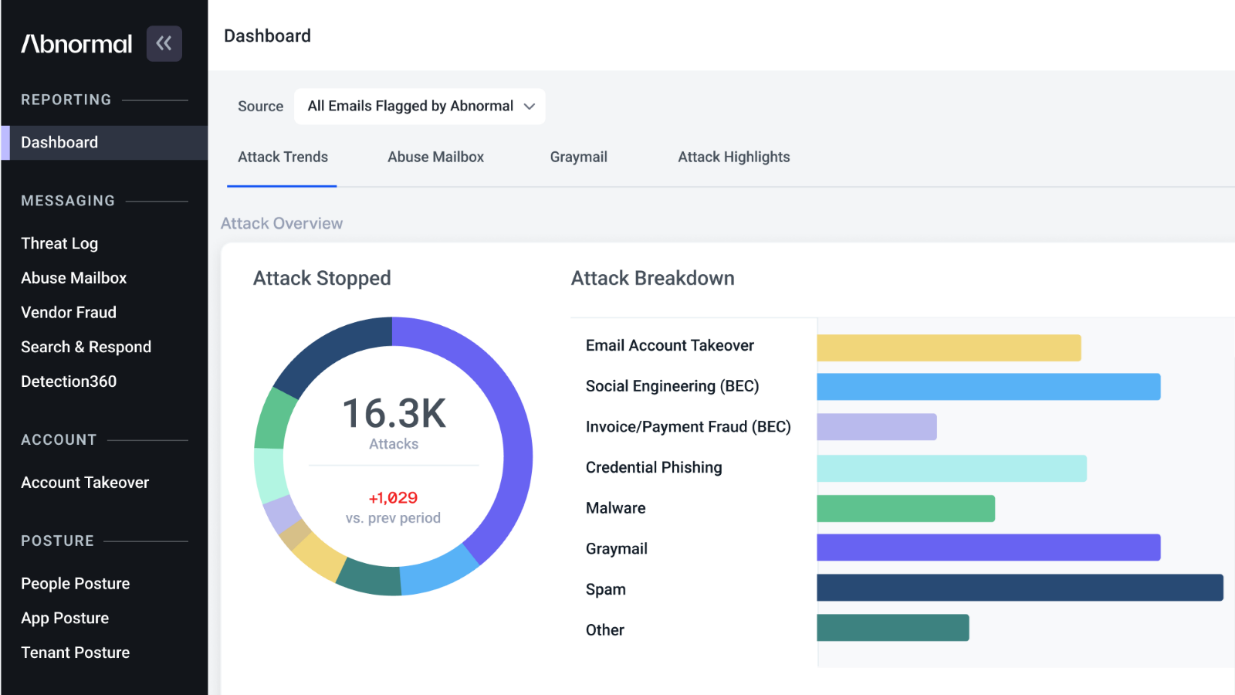
The Inbound Email Security Product operates through three key capabilities: BEC Detection, Behavioral AI, and VEC Detection. BEC Detection analyzes organizational communication patterns to identify Business Email Compromise (BEC) attacks, while behavioral AI detects anomalies in employee and vendor behavior. VEC Detection monitors vendors for risk indicators and adapts protection against attacks from compromised partners.
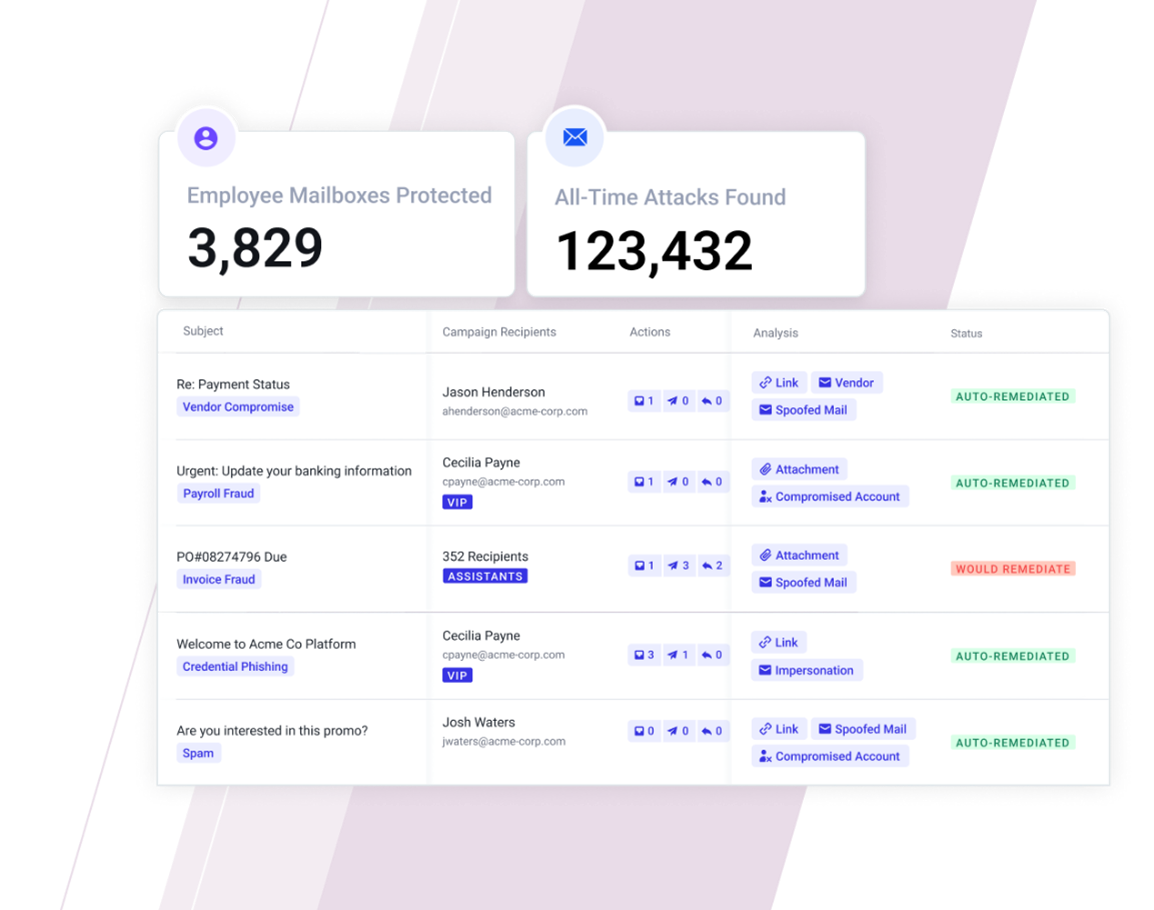
Beyond the core product, additional add-ons such as Abuse Mailbox Automation, Email Account Takeover Protection, Email Productivity, and Email Security Posture Management offer comprehensive email security solutions. These features automate email triage, detect and mitigate account takeovers, improve productivity, and enhance security configurations.
With the conclusion of the insight into Abnormal’s Platform, we look ahead with anticipation. Echelon Risk + Cyber remains dedicated to pushing the boundaries of cybersecurity innovation, forging partnerships that empower us to stay at the forefront of industry trends. If your organization is grappling with specific security challenges, allow Echelon to help alleviate the burden. Reach out to discuss how we might help your organization and stay tuned for more solution highlights in the weeks to come!
Away we go!
1. Urgent Update: 22,500 Palo Alto Firewalls at Risk of Critical Exploit
Cybersecurity professionals have been urgently addressing a critical vulnerability in Palo Alto Networks' GlobalProtect firewalls, specifically identified as CVE-2024-3400. This severe command injection flaw, affecting certain versions of the PAN-OS software, permits unauthenticated attackers to execute commands with root privileges. The vulnerability, disclosed by Palo Alto Networks on April 12, has been under active exploitation since March 26. The company responded swiftly by urging system administrators to implement immediate mitigations and subsequently released patches between April 14 and 18 to close the security loophole.
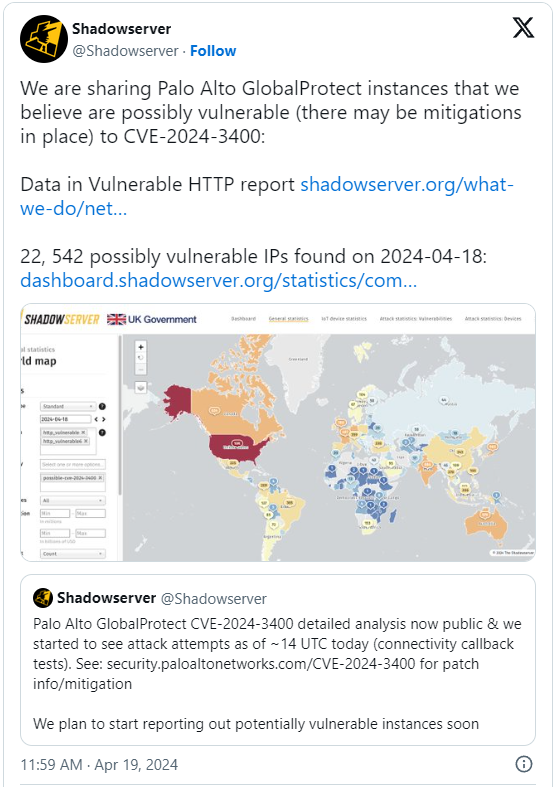
Despite these efforts, ongoing attacks have revealed that a significant number of devices remain at risk. As of late April, approximately 22,500 GlobalProtect firewall units were reported "possibly vulnerable" to the CVE-2024-3400 flaw, with the bulk of these devices located in the United States. Researchers, including those from Volexity, noted that the exploit had been utilized by state-backed actors, dubbed 'UTA0218,' to distribute a custom backdoor named 'Upstyle,' amplifying the severity of the threat. The discovery prompted additional scrutiny, with researchers releasing technical details and a proof-of-concept that demonstrated the ease with which the attacks could be executed.
The situation underscores a critical lesson for the cybersecurity community: the speed of response to such vulnerabilities is crucial. While Palo Alto Networks acted promptly, the window between disclosure and patch availability proved critical as the number of exploits surged. System administrators are now faced with the task of rapidly applying patches to prevent further compromises. The ongoing exploitation of CVE-2024-3400, despite available fixes, is a stark reminder of the challenges in maintaining cyber hygiene across large networks of devices.
2. Critical Infrastructure at Risk: The Escalation of Cyber Attacks by Russian Hackers
In a startling series of cyberattacks, a group known as Cyber Army of Russia Reborn, which claims links to Russia's infamous Sandworm unit, has reportedly sabotaged water utility systems in the United States, Poland, and France. This group, displaying a new level of audacity, has taken responsibility for manipulating the digital interfaces that control physical equipment within these utilities. Their activities include changing operational settings and causing potential disruptions, evidenced by their posting of video proof on Telegram. These incidents have targeted multiple US water utilities, a Polish wastewater treatment facility, and a French water mill—mistakenly thought by the hackers to be a hydroelectric dam.
Recent findings by the cybersecurity firm Mandiant suggest a direct connection between the Cyber Army of Russia Reborn and Sandworm, a notorious segment of Russia's GRU military intelligence. Sandworm has been recognized for its disruptive cyber tactics over the past decade, but the Cyber Army of Russia Reborn appears to be operating with even fewer restraints, engaging directly in sabotage against critical infrastructure. Mandiant's investigation indicates that while this group might initially have been a product of Sandworm, it now operates with a level of independence, executing more reckless and hazardous attacks that directly impact operational technology systems.
The implications of these attacks are profound, as they represent a significant escalation in cyber warfare tactics, directly targeting essential services and creating a potential for real-world chaos. This situation poses serious questions about the security of critical infrastructure and the increasing boldness of state-sponsored cyberattacks. As these hacking incidents continue to unfold, the international community remains on alert for the potential consequences of these increasingly aggressive cyber operations.
3. New York Legislative Commission Faces Cyber Sabotage Amid Budget Season
The Legislative Bill Drafting Commission of New York, a crucial state office involved in shaping legislation, suffered a cyberattack early Wednesday, significantly disrupting the assembly of the fiscal year 2025 budget. The attack occurred just as the office was preparing to print the state budget bills, putting a temporary halt to their operations. However, officials managed to mitigate the disruption by switching to a backup system, allowing them to continue with less contentious budget bills. The identity of the attackers and the full extent of the data breach or damage to the commission's systems remain unclear.
Governor Kathy Hochul and legislative officials have been quick to address the fallout, ensuring that the incident does not stall the overall budget passage. Gov. Hochul noted on WNYC radio that the state was "finding the path forward with 1994 computers," and expressed confidence in resolving the situation thoroughly. Despite the initial setbacks, a spokesperson for the state Senate Democrats reassured that the budget process would not be delayed, emphasizing the ongoing efforts to rectify the issue and finalize the budget efficiently.
This cyberattack highlights the vulnerabilities in crucial state-operated digital infrastructures and raises questions about the readiness of such systems to fend off similar incidents in the future. The quick response to implement a workaround demonstrates a preparedness to maintain legislative operations, but it also underscores the continuous need for robust cybersecurity measures, especially as digital processes become increasingly integral to government functions.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
