Cyber Intelligence Weekly (March 17, 2024): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Before we get started on this week’s CIW, I’d like to highlight a new webinar series by the Echelon Defensive security team, Code Blue.
🚀 Exciting Announcement: Code Blue Webinar - "Validating Digital Identity in a Perimeter-less World" Join us for the premiere episode of our Code Blue Webinar Series, where Chad E. LeMaire, Paul Matvey, Chris Furtick engage in a dialogue with expert guest David Neuman! 🔍 Title: Code Blue – Trust and Resilience Episode 1: Validating Digital Identity in a Perimeter-less World In this session, we'll unravel complex IAM concepts, positioning authentication and authorization as the cornerstone for achieving zero trust architectures. 🏛️ Explore the challenges that legacy identity constructs face in today's dynamic threat landscapes and discover pragmatic approaches for continuous verification. Key Topics: • Leveraging adaptive controls for heightened security • Navigating decentralized credentials in the modern landscape • Implementing hardened administrative access for robust defense Don't miss this engaging webinar! Join our cybersecurity professionals in a round-table discussion as they decode the identity imperative. Gain insights into aligning with least-privilege access principles and securing highly dynamic cloud environments. Secure your spot now: https://www.linkedin.com/events/codeblue-validatingdigitalident7169404748817743873/theater/

Away we go!
1. Hearing Your Typing, A Novel Approach to Cyber Espionage
In an intriguing academic study, researchers from Augusta University have unveiled a new method for deciphering user input through acoustic side-channel attacks on keyboards. This approach, distinct from previous methods, does not necessitate controlled recording conditions or a specific typing platform, making it notably more viable for real-world application. By analyzing the unique sound emissions produced by keystrokes and the typing patterns of users, this technique achieves an average success rate of 43% in predicting typed text. The researchers, Alireza Taheritajar and Reza Rahaeimehr, highlighted that the attack leverages specialized software to compile a dataset of these sound emissions under various conditions, including environments with noise or different keyboard models.
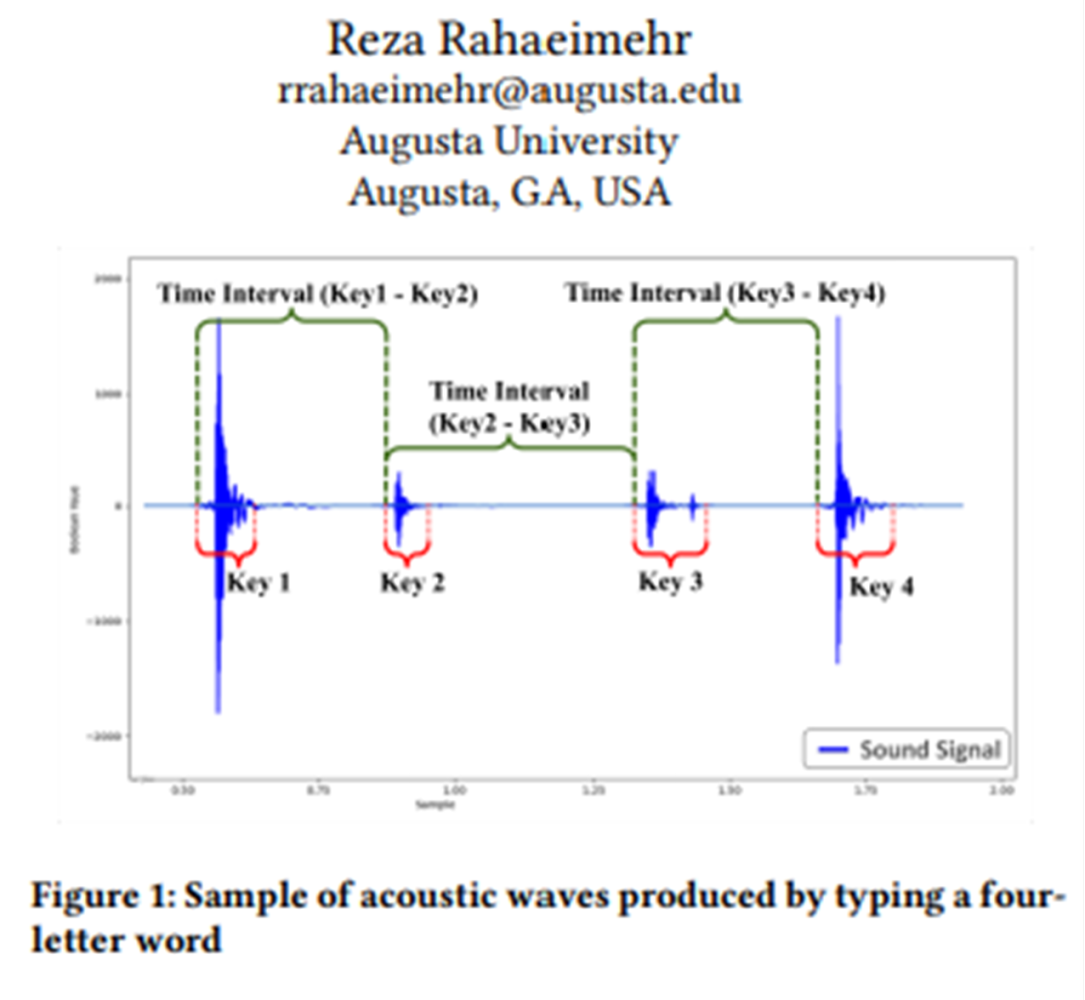
This acoustic attack method requires gathering typing samples from the target, which could be accomplished through various means such as malware or compromised devices. The collected data is then used to train a statistical model that profiles the target’s typing behavior, taking into account the time intervals between keystrokes.
A notable aspect of this method is its flexibility; it remains effective across different keyboards, in noisy environments, and does not require high-quality recording equipment. However, the researchers acknowledge limitations, including difficulties in profiling individuals with irregular typing patterns or those who type exceptionally fast. Test results across 20 subjects varied significantly, suggesting that some individuals may be more vulnerable to this type of attack than others.
2. Reddit's AI Revenue Plan Under FTC Scrutiny
Reddit is embarking on a new revenue strategy by licensing user-generated content to tech giants like Google for AI training purposes, a move that's anticipated to generate over $200 million in the coming years. This plan, revealed ahead of Reddit's impending initial public offering (IPO), has caught the attention of the US Federal Trade Commission (FTC). The FTC, concerned with privacy risks and the fairness of using user-generated content without explicit consent, has initiated an inquiry into Reddit's practices. The scrutiny comes amidst a growing debate over the ownership of digital content and the ethical implications of its commercial use, particularly when that content is instrumental in training increasingly influential AI systems.
The controversy underscores the broader concerns surrounding the use of publicly sourced data in developing AI technologies. While Reddit sees its vast trove of user discussions as a valuable asset for AI research, questions arise about the rights of content creators and the potential risks of personal data leakage through AI models. This situation is emblematic of the challenges facing the tech industry as it navigates the complex interplay between innovation, privacy, and regulatory compliance. The FTC's interest in Reddit's activities reflects a heightened regulatory focus on how data partnerships between major tech companies and AI developers might impact competition and user privacy.
As Reddit prepares to go public, the FTC's inquiry highlights the potential pitfalls of monetizing user content in the age of AI. This move by Reddit, while financially promising, illustrates the delicate balance companies must maintain between leveraging data for growth and respecting the privacy and rights of their users. The outcome of this inquiry could set precedents for how user-generated content is utilized in the rapidly evolving AI sector, affecting not just Reddit but the entire digital ecosystem.
3. Busy Patch Tuesday, Microsoft Patches 60 Windows Vulnerabilities, Apple 2 Zero Days
Last week saw a very busy Patch Tuesday as tech giants Apple and Microsoft have rolled out critical updates to mend a plethora of security vulnerabilities within their operating systems, marking a significant moment in the ongoing battle against cyber threats. Microsoft's recent update tackled no fewer than 60 vulnerabilities across its Windows operating system. Concurrently, Apple released updates for its macOS Sonoma and iOS platforms, addressing at least 68 security issues and two zero-day exploits that had been actively exploited, underscoring the urgency of these fixes. These updates are pivotal in safeguarding user data against potential cyber-attacks and exploitation.
The updates span a broad spectrum of concerns, from memory safety issues—a topic that has sparked wider industry dialogue about the need for memory-safe programming languages—to specific threats like elevation of privilege vulnerabilities identified by Microsoft. Notably, one vulnerability in the Microsoft Authenticator app could allow attackers to steal multi-factor authentication codes and alter or delete accounts. Another critical flaw was found in Microsoft Azure’s Open Management Infrastructure, allowing for remote code execution without authentication. These vulnerabilities highlight the sophisticated nature of cyber threats and the necessity for ongoing vigilance and rapid response from tech companies and users alike.
In addition to operating system updates, Adobe has also released patches for a host of security vulnerabilities across its products, including Adobe Experience Manager and Adobe Premiere Pro, among others. Moreover, Adobe has introduced a "new generative AI feature" for Acrobat users, which, while innovative, has also prompted the company to offer instructions for those wishing to opt out, reflecting the growing intersection between cybersecurity, user privacy, and the advancing frontiers of technology. As the digital landscape continues to evolve, these updates and the challenges they address underscore the critical importance of cybersecurity measures in protecting both individual users and the broader digital ecosystem.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about

