Cyber Intelligence Weekly (March 20, 2022): Our Take on Three Things You Need to Know
Welcome to our weekly post where I will be sharing some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
You can also Subscribe to receive Cyber Intelligence Weekly in your inbox each week.
Before we get started on this week’s CIW, I’d like to highlight a webinar this week where our very own Jake Murphy will be a guest with our friends at Horizon3 and their Tech Talk Series, The Attacker’s Journey. They will be talking about becoming an ethical hacker and then deep dive into a discussion about SQL injection attacks and how an attacker can use those techniques to gain a foothold into your network. Register here!

Away we go!
1. Germany Warns Against Use of Kaspersky Antivirus Software
Germany’s top watchdog for information security matters, the Federal Office for Information Security (BSI) recently warned against the use of Kaspersky antivirus software. They cited in their warning that due to the conflict and aggression against the Ukraine, there is a considerable risk of further cyber-attacks. They also mentioned that a Russian IT systems manufacturer may be used to carry out offensive operations itself or they may be forced to help carry out attacks against their will.

While the press release does not outright ban the use of the Kaspersky software, it is strongly suggesting that German organizations replace products made by the Moscow-headquartered security company. An antivirus program such as Kaspersky is deeply rooted in systems and networks and if used against the organization it is supposed to protect, it could prove devastating. The SolarWinds breach is a perfect example of this.
Kaspersky officials have told several news sources that their software is safe and that the Russian government does not have the necessary influence over them for their software to be used in that manner. They very much are taking the angle that this is a politically motivated move, not a move grounded in any real technical concerns. Their full response to the matter can be found on their website.
This isn’t the first time that Kaspersky has come under serious scrutiny for these fears. Back in 2017, the Trump administration banned the use of Kaspersky software across all Executive Branch agencies. In my opinion, there are much better options out there that don’t come with the risk, whether it is real or not.
2. Microsoft Defender Tags Office Updates as Ransomware Activity
We’re going to stick to the antivirus theme here for our second story of this week. A recent article from Bleeping Computer highlighted several reports of Windows system administrators being hit by an onslaught of false ransomware alerts. As it turns out, Office updates were being tagged as malicious and being attributed as ransomware behavior. Understandably causing panic in Windows system admins around the world.

The Bleeping Computer article does note that Microsoft confirmed the Office updates were mistakenly tagged as thought and that their engineers have updated cloud logic for Defender to prevent future false positives.
Microsoft issued a statement on the matter, “Starting on the morning of March 16th, customers may have experienced a series of false-positive detections that are attributed to a Ransomware behavior detection in the file system. Admins may have seen that the erroneous alerts had a title of 'Ransomware behavior detected in the file system,' and the alerts were triggered on OfficeSvcMgr.exe. Our investigation found that a recently deployed update within service components that detect ransomware alerts introduced a code issue that was causing alerts to be triggered when no issue was present. We deployed a code update to correct the problem and ensure that no new alerts will be sent, and we've re-processed a backlog of alerts to completely remediate impact.”
3. Ukraine’s President Zelensky Deepfaked in False Surrender Tactic
Last week, video emerged on social media with a video that purported to be Ukraine’s President Zelensky urging his country to lay down their arms and surrender. In addition, TV Channel Ukraine 24 was hacked and a summary of the fake news was inserted on its website and the scroll on the bottom of the TV screen. This may very well be the first reported use of a deepfake being used during an armed conflict, essentially a weaponization of deepfake technology.
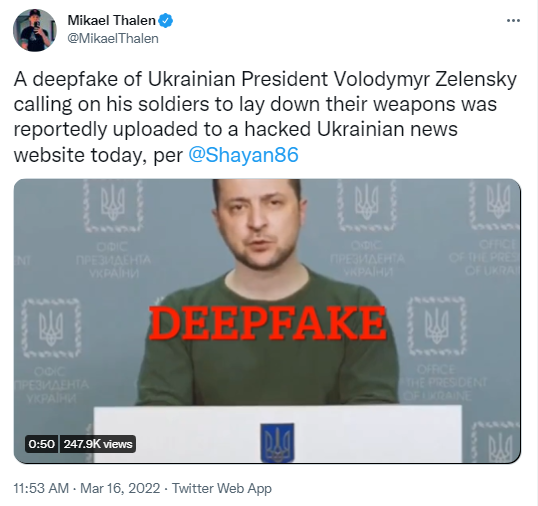
Luckily the video was very poor quality and removed swiftly. While the video was quickly debunked and taken down, many are worried that this is just the tip of the iceberg and there will be many more attempts to come.
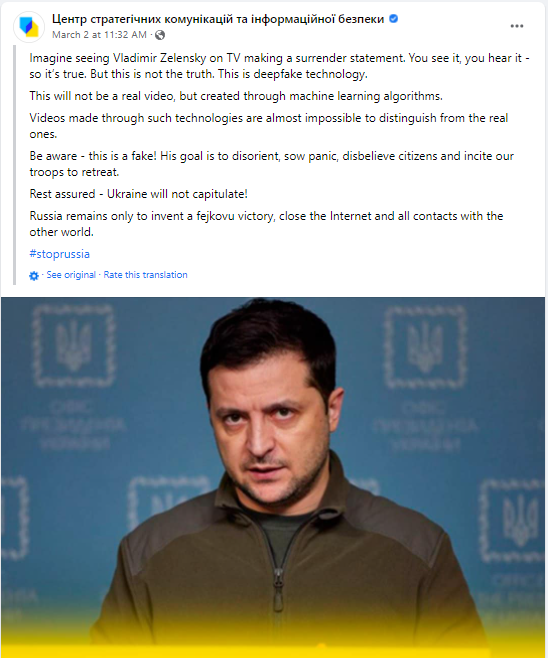
In this case, the Ukrainian government and President Zelensky were prepared as Ukraine’s Centre for Strategic Communications cautioned weeks ago that Russia may attempt these types of tactics (see photo below). In addition, President Zelensky swiftly responded with a Facebook video of his own minutes after, denying that deepfake. These prior warnings, as well as President Zelensky’s swift action, were able to quickly debunk the misinformation. However, it is scary to imagine the damage that could be possible in these types of scenarios if the circumstances were just a little bit different.
Thanks for reading! Echelon is a full service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more point solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
