Cyber Intelligence Weekly (April 2, 2023): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Also, we are always looking for great people to join our team. If you know anyone who fits the profiles for any of our open positions, drop me a line and let me know!
Before we get started on this week’s CIW, I’d like to highlight that our very own Dahvid Schloss, Director of Offensive Security Services, and Ross Flynn - CISSP, CEH, CCSK, HISP, Cybersecurity Manager, will be speaking at Hack Space Con 23. Their talk, "C2 Connoisseuring: How to Turn Anything into a Masterful C2 System," will take you on a journey to learn how to turn any object into a powerful C2 system, potentially leaving your blue teams in the dark.
Whether you're a seasoned ethical hacker or just starting out, this talk is a must-attend! Don't miss out on the opportunity to learn from these two cyber experts. See you there!
Sign up here: https://www.eventbrite.com/e/hack-space-con-23-cybersecurity-space-aero-defense-hacker-conference-tickets-516298802617

Away we go!
1. Kremlin Cyber Espionage Tactics Revealed in Released Vulkan Files
When it comes to disruptive and clever cyberattacks targeting infrastructure, the Russian government and military continue to be the most aggressive in the world. However, according to a new story released by the Guardian and several other news outlets, it appears that the Kremlin has been using more of a hybrid war playbook according to documents leaked by a whistleblower inside a Russian intelligence contractor, that shows evidence that the Kremlin outsources some work to a private company named NTC Vulkan.
The leaked files, which were also examined by Mandiant, show that Vulkan provided software tools are used by Russian intelligence organizations like the FSB, which succeeded the KGB, and the GRU, which is known for its famed Sandworm malware team. The group provided tools, training materials, as well as a red team platform that was meant to help practice many sorts of offensive cyber operations, such as cyber espionage, IO, and operational technology (OT) attacks.
The takeaways from the Mandiant article were very interesting. They mention how the development of tools like “Scan”, which allow must faster open source intelligence gathering at scale, signal that the GRU may be trying to push more fast paced operations by becoming more streamlined and efficient. Most concerning, these documents and plans released demonstrate the notion that the Kremlin and its supporters are developing capabilities to attack critical infrastructure systems, especially those related to energy, oil, and gas, but also those related to water, and those that involve rail, sea, and air transportation.
2. Massive Supply Chain Attack Hitting 3CX Desktop App
3CX, the popular internet phone, video and corporate chat software, used by millions worldwide, has been hit with a malicious supply chain attack. 3CX’s website boasts it has 600,000 customers worldwide, with logos of PWC, Mercedes Benz, BMW, Toyota, CocaCola, Airfrance, McDonald’s and more on its website.
Threat hunters from CrowdStrike Falcon’s Overwatch team were amongst the first to spot the malicious activities that were originating from the software. The original post from CrowdStrike reads as follows, “On March 29, 2023, CrowdStrike observed unexpected malicious activity emanating from a legitimate, signed binary, 3CXDesktopApp — a softphone application from 3CX. The malicious activity includes beaconing to actor-controlled infrastructure, deployment of second-stage payloads, and, in a small number of cases, hands-on-keyboard activity. The CrowdStrike Falcon platform has behavioral preventions and atomic indicator detections targeting the abuse of 3CXDesktopApp. In addition, CrowdStrike Falcon OverWatch helps customers stay vigilant against hands-on-keyboard activity. The 3CXDesktopApp is available for Windows, macOS, Linux and mobile. At this time, activity has been observed on both Windows and macOS. CrowdStrike Intelligence has assessed there is suspected nation-state involvement by the threat actor LABYRINTH CHOLLIMA. CrowdStrike Intelligence customers received an alert this morning on this active intrusion.”
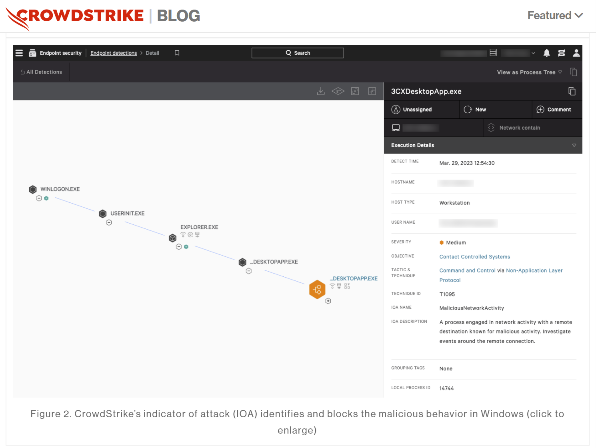
The details of how the application was compromised in the first place are not yet clear. One thing is for certain, supply chain attacks will continue to be favored by threat actors around the globe to covertly carry out their misdeeds.
3. U.S. Executive Order Restricts Procurement of Commercial Spyware
President Joe Biden recently signed an Executive Order that prohibits operational use by the U.S. Government of commercial spyware tools. The Executive Order notes, “The proliferation of commercial spyware poses distinct and growing counterintelligence and security risks to the United States, including to the safety and security of U.S. Government personnel and their families. U.S. Government personnel overseas have been targeted by commercial spyware, and untrustworthy commercial vendors and tools can present significant risks to the security and integrity of U.S. Government information and information systems.”
The Executive Order specifically targets commercial spyware products that pose a risk to national security. This includes products that have been developed or sold by companies that are owned or controlled by foreign governments, as well as those that have been identified as being used for malicious purposes.

By prohibiting the use of these products by United States government agencies, the Executive Order aims to protect national security and safeguard the privacy and civil liberties of individuals. The Executive Order is a positive step forward in the fight against the proliferation of commercial spyware. It sends a clear message that the United States government will not tolerate the use of these tools for malicious purposes and will take action to protect the privacy and civil liberties of individuals.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
