Cyber Intelligence Weekly (March 6, 2022): Our Take on Three Things You Need to Know
Welcome to our weekly post where I will be sharing some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
You can also Subscribe to receive Cyber Intelligence Weekly in your inbox each week.
Before we get started on this week’s CIW, I’d like to highlight our partnership with CrowdStrike. Cyber threats are constantly evolving that’s why we need to evolve with them too. Employing the best of breed solutions is important to us and CrowdStrike's Falcon platform will help us keep being part of this evolution. Combining Echelon´s expert advice, and full suite of cybersecurity services with CrowdStrike´s industry-leading endpoint protection will help prevent breaches and keep our clients safe.

Away we go!
1. Senate Passes Cyber Incident Reporting Bill, House Next Up
Last Tuesday, the Senate passed a major cybersecurity package that would require organizations that are classified as critical infrastructure to report cybersecurity incidents to the government.
Cyber attacks against critical infrastructure companies and federal systems have increased over the previous years and have disrupted the lives of countless Americans. Now with increased geo-political tensions and the threat of further cyber-attacks, United States politicians have united to pass the Strengthening American Cybersecurity Act of 2022 through the Senate.
The Strengthening American Cybersecurity Act of 2022 is actually a combined bill that actually has three major components to it:
- Federal Information Security Modernization Act of 2022 – Improving cybersecurity measures and putting guidelines in place for good cybersecurity management protocols for government systems for taking a risk-based approach to cybersecurity.
- Cyber Incident Reporting for Critical Infrastructure Act of 2022 – Mandatory cyber incident reporting for any an entity in a critical infrastructure sector, as defined in Presidential Policy Directive 21.
- Federal Secure Cloud Improvement and Jobs Act of 2022 – Ensuring the government can leverage cloud computing assets to continue to modernize its systems through enhancements to the FedRAMP program.
For the Cyber Incident Reporting for Critical Infrastructure Act, covered entities will have to report cyber incidents no later than 72 hours after the covered entity reasonably believes that the covered cyber incident has occurred, and ransomware payments must be reported no later than 24 hours after the ransom payment has been made. Some examples of the critical infrastructure sector include energy, financial services, defense industrial base, nuclear, and more.


While the bill clearly outlines the entities in scope for these new reporting requirements, CISA will have the final say in a formal rulemaking process, as well as deciding more specifically the type of events that qualify and what the covered entities must share. In the rulemaking period CISA would have two years after enactment of the law to propose rules, and an additional 18 months to complete them. To encourage information sharing, covered entities under this bill would have liability protections for information they share and would face no fines for not complying.
We have been down this road before many times over the past decade and have failed. While this bill still needs to pass the house, there seems to be much greater support this time around from lawmakers from both sides of the aisle who seem to be standing in support of these measures as global cyber tensions mount. There is nothing like a common enemy to bring politicians together during trying times. We will certainly be monitoring this closely as it progresses.
2. Kinetic and Cyber Warfare, Microsoft Responds
A recent fascinating blog post by Microsoft President and Vice Chair Brad Smith outlines how Microsoft quickly reacted to the looming cyber threats that have accompanied the Russian war against Ukraine. On February 24th, Microsoft’s Threat Intelligence Center (MSTIC) detected a new round of offensive and destructive wiper malware directed against Ukraine.
Within hours, Microsoft responded to this intelligence by notifying Anne Neuberger, the White House’s deputy national security adviser for cybersecurity, they then notified NATO and the Ukrainian cyber defense. Microsoft also quickly updated their anti-malware programs to detect and block these new threats. The blog post by Smith also notes that the Ukrainian government is a customer, among many other organizations and individuals in the Ukraine.

Smith’s comments also raised concerns about the use of cyber attacks against critical infrastructure components as well as Ukrainian civilian digital targets. In his blog he cites the targets specifically as the financial sector, agriculture sector, emergency response services, humanitarian aid efforts, and energy sector organizations and enterprises.
While Smith points out at the outset of his remarks that Microsoft is “a company and not a government or a country,” they clearly stand on the side of good in times like these and are actively supporting the Ukraine, NATO, and its allies against these damaging nation state sponsored cyber-attacks.
3. Conti Ransomware Group Data Leaked by Security Researcher
The Conti Ransomware-as-a-Service gang has had some major issues over the past week, as many of their internal files, chats, code, and other items were leaked. The Conti group had published on their website earlier last week that they will use their “full capacity” to retaliate against the “west” should they use any of their cyber capabilities against Russia.
This was shortly followed by a new Twitter account called “Contileaks,” that began posting Conti group chat logs and several other troves of juicy insider data, including their ransomware source code. Among the messages, there have been other interesting tidbits discovered, including indications in the messages that show Conti’s relationship with the TrickBot and Emotet malware gangs.
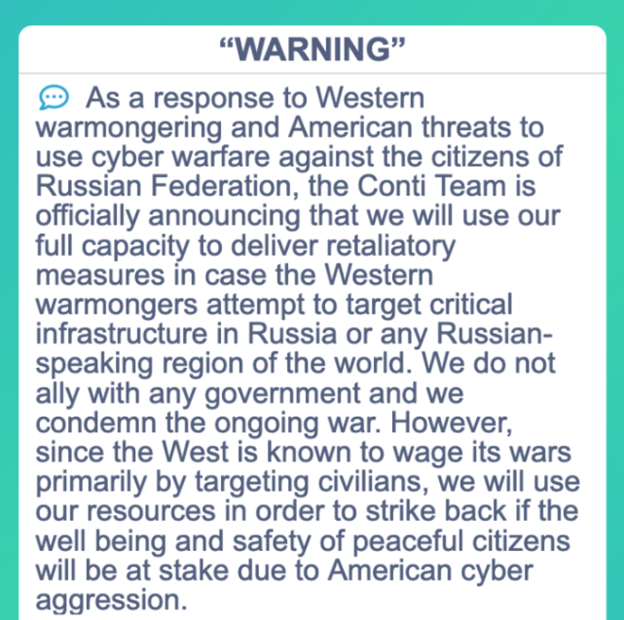
While no one knows exactly who is behind the leak, many have surmised that it is from a Conti insider who is pro-Ukraine that has decided to dissent. While many of these ransomware groups work across international borders, it is widely believed that the Conti group has members from both Russia and the Ukraine within its ranks. However, according to Brian Krebs and security researcher, Alex Holden, the leaker of the Conti files is not a Conti affiliate or insider and is a pro-Ukrainian independent security researcher.
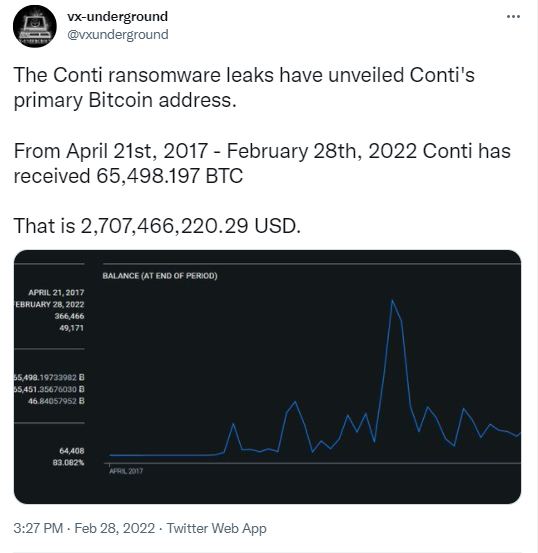
What is most startling about these discoveries is the amount of Bitcoin that the Conti Group has received at it’s primary BTC addressed that was revealed as part of this data dump, over 65,000 BTC!