Cyber Intelligence Weekly (May 15, 2022): Our Take on Three Things You Need to Know
Welcome to our weekly post where I will be sharing some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
You can also Subscribe to receive Cyber Intelligence Weekly in your inbox each week.
Before we get started on this week’s CIW, I’d like to highlight our continuous penetration testing service. Our Continuous Penetration Testing offering combines the knowledge of our talented adversarial emulation engineers with best-in-class continuous and autonomous penetration testing tooling through our partners at Horizon3 and PlexTrac. This combination enables your organization to persistently emulate threat actor activity within your environment at machine speed. Check out our website or reach out to me for more information!
Away we go!
1. Thousands of Websites Collect Your Data in Web Forms Before Form Submission
In a recent study by researchers from KU Leuven, Radboud University, and University of Lausanne, they found that thousands of websites in the EU and the US scrape data from forms prior to the user actually hitting submit on a form.

By most accounts, one would reasonably assume that their data is not being collected by a third party prior to actually hitting submit on a form, effectively giving consent at that moment. However, the study found 1,844 websites from the UK and 2,950 websites from the US exfiltrated users’ email addresses to tracking, marketing and analytics domains before form submission and consent.
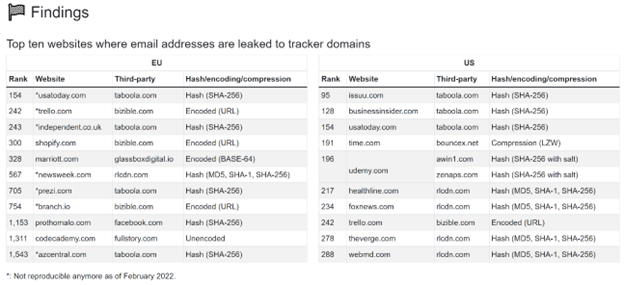
Amongst the websites that attribute this behavior are Meta (formerly Facebook) and TikTok. The top 10 observed websites where email addresses are leaked is found below. The researchers notified many of the affected websites and many said they had no idea that data was being scraped in this way. The study does contribute some of the activity to third party data collectors and aggregator scripts that may be embedded in the website.
In my opinion, organizations must understand what their website is doing, they can’t claim no responsibility because it was a third-party plugin. Data Protection Authorities were notified of the behavior found by the researchers, it will be interesting to if there is any legal fall out from this.
2. DEA Law Enforcement Portal Possibly Breached
While we are on the topic of leaky websites, we look at this recent bit of news from Brian Krebs last week. Krebs received a tip in early May that hackers may have access to some sensitive law enforcement systems, including esp.usdoj.gov, which is the Law Enforcement Inquiry and Alerts (LEIA) system run by the DEA.
The Krebs story outlines how the LEIA system provides users with access to other systems, databases and information repositories that are “law enforcement sensitive” and “mission sensitive” to the DEA. The hacker shared screenshots with Krebs, showing how these systems were accessed and could be used to query this sensitive data.
Krebs also spoke to a researcher about the issue who noted that the access to this type of data would be priceless to significant criminal groups and cartels and how they could use this access to not only query data, but also potentially submit false records into law enforcement databases.
The Krebs story also dives into an analysis of these government operated sites and notes how some of them only require a username and password, with no multi-factor authentication (MFA) in place at all. Lack of MFA is one of the top ways that threat actors are able to abuse systems. Not having MFA on such sensitive government systems is a scary notion, and shows that we still have a long way to go.
3. Businesses Seek to Soften Up SEC Cybersecurity Reporting and Disclosure Rules
A recent Wall Street Journal story summarized how many businesses and big consulting firms are weighing in during the public comment period for the new SEC cybersecurity reporting requirements.

Back in early March, we wrote about the new rules coming down the line from the SEC and how they were set to transform the cybersecurity reporting and disclosure landscape for public companies. Since then, organizations have been weighing in with their opinions on how these changes will affect their businesses.
Here are some of the key themes that the SEC is hearing:
- The cost of compliance will continue to rise to meet more demanding requirements
- There may be additional cyber risks associated with a company reporting about specific issues that they have had, it could draw additional unwanted attention
- Completing a materiality determination could takes weeks, if not months to perform, therefore many are calling for the 4-day requirement AFTER the materiality has been confirmed
- Identifying other factors that make a cyber event material is still a very gray area
- Reporting of incidents that are material in the aggregate is also a very gray area, as different incidents may not relate to one another ad the materiality assessments may vary by type of incident involved
It will be interesting to watch as the comments are considered, and the final rulemaking takes place. Will the SEC acquiesce to the comments and criticism, or will they hold strong and make overarching changes? We will continue to watch this closely and report back.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
