Cyber Intelligence Weekly (Nov 14, 2021): Our Take on Three Things You Need to Know
Welcome to our weekly post where I will be sharing some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
You can also Subscribe to receive Cyber Intelligence Weekly in your inbox each week.
Away we go!
1. Robinhood Announces Data Breach, Millions of Records Involved.
Last week, the popular trading application, Robinhood, reported a data breach. The announcement notes that the attacker socially engineered a customer service representative by phone and was able to obtain access to certain customer service systems that they later exploited broadly.
Robinhood notes that they don’t believe any financial related data was stolen, and the hacker made off with an email list of over five million people. Full names of a group of two million people and a smaller list of 310 people with a larger set of personal information were also obtained by the attacker.
The report also notes that the attacker tried to demand an extortion payment from the company as well. This is yet another example of threat actors demanding extortion payments after grabbing large amounts of confidential or personal data from an organization. This continues to highlight a shift in the landscape of threat actors. Before, selling this personal data on the dark web was the primary end game, but that has switched to both selling personal data plus outright company extortion. Many organizations do consider paying these demands to avoid naming and shaming and public posting of company confidential data by the threat actors.

This attack is another reminder of the risks of social engineering that companies face. If your social engineering training program only focuses on phishing emails, it is time to rethink your approach. Phishing is far from the final social engineering vector of attack out there. Employees can tricked and scammed through a variety of methods, voice, text, chat programs, etc. Don’t just focus on phishing, ensure that your social engineering training program takes a business process-oriented approach and considers risks from all angles of how you do business.
2. FBI Systems Abused in Hoax Email Blast.
It was an anxiety inducing Saturday morning for hundreds of thousands of system administrators across the country who received an email that appeared to come from the FBI. The email purports to be from the FBI and explains to the recipient that they have observed “exfiltration of several of your virtualized clusters.” The email was also coming from a legitimate FBI email source, which caused a brief moment confusion and panic amongst the greater tech community over the weekend. Spamhaus later put out reports that the email was indeed a hoax and that the emails were being sent to addresses scraped from the American Registry for Internet Numbers (ARIN) registry.
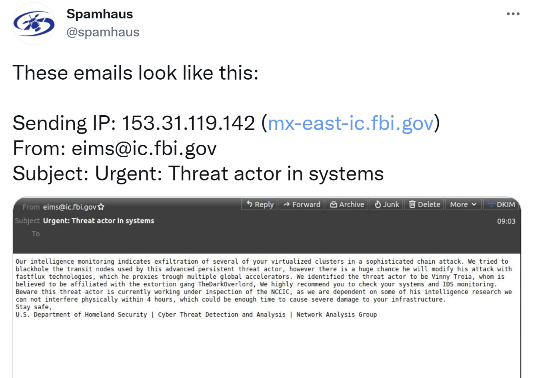
Later that morning, security researcher Brian Krebs penned an article about the incident, but also noted that he was contacted by the individual supposedly behind the hoax. This person called themselves “Pompompurin” and they stated to Brian Krebs that the hack was performed to point out glaring holes in the FBI’s system.
The Krebs article notes that the FBI’s email system abuse began with an exploration of its Law Enforcement Enterprise Portal (LEEP). From here, Pompompurin was able to generate an account whereby they received an email confirmation from ‘[email protected]’ with a one-time passcode, which was viewable in the HTML of the webpage. Pompompurin was then able to abuse a client-side generated POST request from the website and change the content of the email subject and body content and then send to hundreds of thousands of people.
The FBI released an updated statement on November 14th: The FBI is aware of a software misconfiguration that temporarily allowed an actor to leverage the Law Enforcement Enterprise Portal (LEEP) to send fake emails. LEEP is FBI IT infrastructure used to communicate with our state and local law enforcement partners. While the illegitimate email originated from an FBI operated server, that server was dedicated to pushing notifications for LEEP and was not part of the FBI’s corporate email service. No actor was able to access or compromise any data or PII on the FBI’s network. Once we learned of the incident, we quickly remediated the software vulnerability, warned partners to disregard the fake emails, and confirmed the integrity of our networks.
Ironically, this comes on the heels of a CISA Directive from earlier this month with its charge of “drive urgent and prioritized remediation of vulnerabilities that are being actively exploited by adversaries.” While the FBI infrastructure itself had not been significantly compromised, the vulnerable code in its website could have been used to cause much more damage and harm if a threat actor chose to do so. This is yet another reminder that a vulnerability is more than just a missing patch in an operating system and vulnerability management programs need to include all components of people, infrastructure, and software.
3. 50+ Flaws In This Month’s Patch Tuesday from Microsoft.
This past week Microsoft released over 50 patches to help close vulnerabilities in its operating systems, components, and other software. Of the vulnerabilities found, several of them are critical and are being exploited in the wild.
Some of the most critical vulnerabilities include:
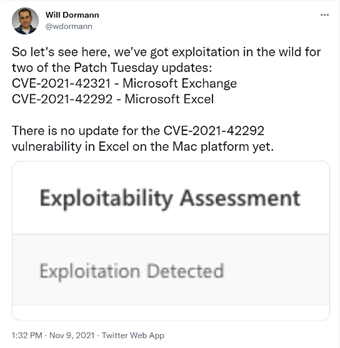
- CVE-2021-42321: Microsoft Exchange Server Remote Code Execution Vulnerability - This is a Microsoft Exchange Server vulnerability that is currently being actively exploited. The alert does note that it is a post-authentication vulnerability, meaning that valid credentials are required to exploit this issue. It has been a tough road for Exchange this year, as there have been several critical issues being exploited regularly in 2021.
- CVE-2021-42292: Microsoft Excel Security Feature Bypass Vulnerability - This patch fixes a vulnerability in Excel that allows code execution when a user opens a specially crafted file with an affected version of Excel. This is likely due to loading code that should be behind a warning prompt that is not occurring. There is no patch yet for MAC OS versions of Excel at this time, so be careful all MAC users!

While the volume of critical issues and overall patches this month is somewhat lower than usual, there are still some nasty issues out there that require immediate attention. Happy patching everyone!
