Cyber Intelligence Weekly (November 20, 2022): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Also, we are always looking for great people to join our team. If you know anyone who fits the profiles for any of our open positions, drop me a line and let us know!
Before we get started on this week’s CIW, I’d like to highlight this great article by our very own Chereese Langley, Senior Cybersecurity Consultant, where she breaks down everything you need to know about the ISO 27001:2022 changes and provides advice for how to get (and stay) compliant.

I also would like to mention that we are still looking for our final sponsors and speakers for the PGH Infosec Day 2022. If you would like to attend, speak, or sponsor, feel free to shoot me a note and/or checkout the event website to register to attend! Our keynote speaker is Brett Johnson, former United States Most Wanted, referred to by the United States Secret Service as "The Original Internet Godfather.”

Away we go!
1. CISA Announces Iranian Government-Sponsored APT Actors Compromise Federal Network
The U.S. Cybersecurity and Infrastructure Security Agency (CISA), recently put out a press release announcing that a U.S. government entity at a Federal Civilian Executive Branch (FCEB) observed suspected advanced persistent threat (APT) activity. They concluded in their alert that after an investigation that they believe that the FCEB network compromise was by Iranian government-sponsored threat actors. The alert did not state which FCEB entity was compromised in this attack.

In this alert, CISA describes how the threat actors compromised the systems. From an investigation that dates to the summer months, they noted that the threat actors exploited the several months old Log4Shell vulnerability in an unpatched VMware Horizon server, they then installed the XMRig crypto mining software, they moved laterally to the domain controller), compromised credentials through the use of Mimikatz, and then implanted Ngrok reverse proxies on several hosts to maintain persistence.
CISA has also published a very detailed breakdown of the compromise so that other agencies and businesses can learn from the events. Essentially, the threat actors exploited Log4Shell to gain initial access, used PowerShell to add an exclusion tool which whitelisted the entire c:\ drive, persisted through changing of the local administrator account on several hosts, used Mimikatz to create a new domain administrator account, and voila!
As far as the recommended CISA mitigations go, most of them are tried and true:
- Apply patches to known vulnerabilities
- Keep all software builds up to date
- Minimize your internet-facing attack surface
- Use IAM best practices, like implementing phishing resistant MFA
- Secure and protect credentials
2. Researchers Quietly Cracked Zeppelin Ransomware Keys
A new Brian Krebs story from last week tells the story of how researchers found a way to beat a certain strain of ransomware. The Krebs article talks about how a cybersecurity consulting firm in New Jersey called Unit 221B has discovered vulnerabilities in the Zeppelin ransomware’s encryption routines that they were able to take advantage of and brute-force the decryption keys.

Unit 221B was motivated by the fact that the Zeppelin ransomware actors were using their malware against rather helpless organizations such as non-profit organizations, homeless shelters and charities. The Unit 221B team was able to capture the RSA-512 public key out of memory, which they were then able to crack thanks to a cluster of 800 donated CPU’s at Digital Ocean.
This is a rare win in the fight against ransomware. Sometimes, the bad guys can have vulnerabilities too!
3. Russian Software Disguised as American Present in 8,000+ Apps
An exclusive report from Reuters’ James Pearson and Marisa Taylor call into question a popular mobile application development company named, Pushwoosh. The Reuters journalists show that Pushwoosh is primarily a Russian based company, that has appeared to try and cover up its origins as such. Pushwoosh code allows app developers to send notifications to, and also track users and is used in upwards of 8,000 iOS and Android apps per the Reuters story. Pushwoosh has also responded to this story on their blog.

Jerome Dangu, co-founder of Confiant, a firm that tracks misuse of data collected in online advertising supply chains said this in the Reuters story, “Pushwoosh collects user data including precise geolocation, on sensitive and governmental apps, which could allow for invasive tracking at scale. We haven't found any clear sign of deceptive or malicious intent in Pushwoosh's activity, which certainly doesn't diminish the risk of having app data leaking to Russia.”
Most notably, mobile applications used by the U.S. Army and the CDC both removed the Pushwoosh code from its apps. The Army removed the code from its apps back in March of this year, while the CDC removed the code after it learned about the potential concerns from Reuters. James Pearson also points out in his article and his Twitter page about how the company used several methods in trying to hide their origins, for example, there were several executives listed on LinkedIn that appeared to be completely fake profiles, with one of the pictures below belongs to an Austria-based dance teacher.
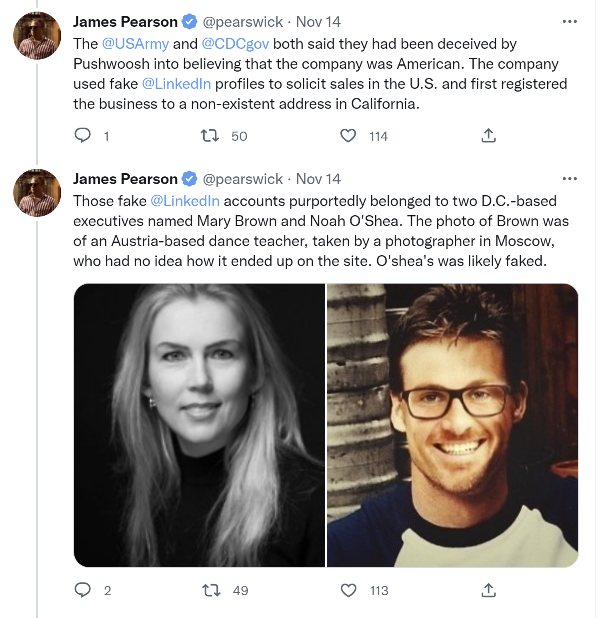
While there are several organizations that use off-shore or near-shore development resources, it is highly unusual to go to these sorts of lengths to hide it.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
