Cyber Intelligence Weekly (November 27, 2022): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Also, we are always looking for great people to join our team. If you know anyone who fits the profiles for any of our open positions, drop me a line and let us know!
Before we get started on this week’s CIW, I’d like to highlight our platinum sponsorship of PGH InfoSec Day at the Rivers Casino in Pittsburgh on December 5, 2022. Come see us in the sponsor hall or come listen to one of our two thought leadership talks (Credentials are the New RCE and Mitigating (Radio) Active Directory) throughout the day!
More information and to sign-up, click here: https://www.pghinfosecday.com/

Away we go!
1. Department of Defense Releases Zero Trust Strategy and Roadmap
This past week, the Department of Defense (DoD) released their zero trust strategy and roadmap to implement zero trust principles within all DoD systems and networks by 2027. The DoD strategy lays our four high-level strategic goals that define what the DoD will follow to achieve its vision for zero trust:
- Zero Trust Cultural Adoption – All DoD personnel are aware, understand, are trained, and committed to a Zero Trust mindset and culture and support integration of ZT.
- DoD information Systems Secured and Defended – Cybersecurity practices incorporate and operationalize Zero Trust in new and legacy systems.
- Technology Acceleration – Technologies deploy at a pace equal to or exceeding industry advancements.
- Zero Trust Enablement – Department- and Component-level processes, policies, and funding are synchronized with Zero Trust principles and approaches.
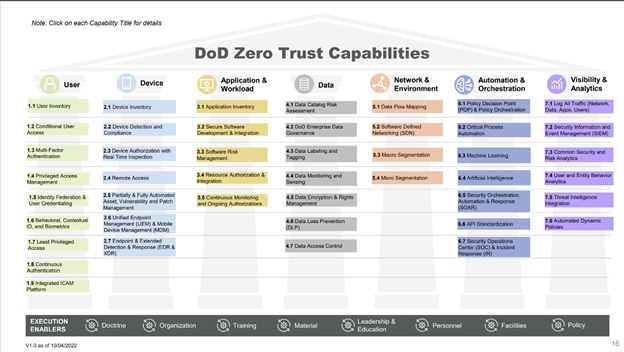
This DoD Zero Trust strategy comes on the heels of a wider White House Zero Trust Strategy from earlier this year (January). The DoD’s approach to zero trust implementation includes 45 capabilities that are organized around seven pillars (user, device, application & workload, data, network & environment, automation and orchestration, visibility, and analytics. There are two levels of maturity that they will aspire to across those pillars, “target” and “advanced."
DoD, CIO John Sherman had this to say in a foreword to the overall strategy, “Zero Trust is much more than an IT solution. Zero Trust may include certain products but is not a capability or device that may be bought. The journey to Zero Trust requires all DoD Components to adopt and integrate Zero Trust capabilities, technologies, solutions, and processes across their architectures, systems, and within their budget and execution plans. Perhaps most importantly, they must also address Zero Trust requirements within their staffing, training, and professional development processes as well.”
This concept of zero trust lives the mantra of “never trust, always verify” and it is a key shift in information security philosophy. This shift in philosophy is from an external perimeter protection focus, to more of a wholistic approach across the entire technology lifecycle. Given the mode of today’s attacks being more and more identity based, this approach has lots of merit in theory, it will be interesting to see how this all plays out in actuality.
2. FCC Bans Authorizations for Devices That Pose National Security Threat
Just a couple days ago the Federal Communications Commission (FCC) announced new rules that will prohibit importation or sale of certain communications equipment that is deemed to pose an unacceptable risk to national security of the United States. This is a larger step from a ruling earlier in the year by the Department of Commerce, who added the entities to the department’s “entity list.”

The FCC’s new rule is a big deal because it prohibits the authorization of equipment through the FCC’s certification process and bans any of the devices from being imported or marketed in the United States. The following entities are the manufacturers of the banned devices, Huawei Technologies, ZTE Corporation, Hytera Communications, Hangzhou Hikvision Digital Technology, and Dahua Technology. The entire list of FCC banned equipment and services can be found here: https://www.fcc.gov/supplychain/coveredlist
FCC Chairwoman Jessica Rosenworcel has this to say in a prepared statement, “The FCC is committed to protecting our national security by ensuring that untrustworthy communications equipment is not authorized for use within our borders, and we are continuing that work here. These new rules are an important part of our ongoing actions to protect the American people from national security threats involving telecommunications.”
3. Hundreds Arrested in UK Fraud Service Website iSpoof
Big win for the good guys last week in the United Kingdom where more than 100 people have been arrested in connection with what the Metropolitan Police Service are calling one of the biggest fraud services ever uncovered, iSpoof. The police delivered this snarky video via the organization’s Telegram site: https://t.me/ispoofclub/328
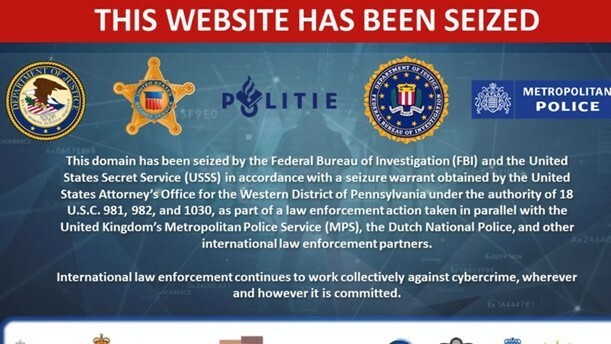
The service has been used by criminals to spoof legitimate businesses, such as the customer’s bank. The spoofing service would be used by bad guys to pose as employees of banks such as Barclays, HSBC, Lloyds, and others in order to steal data and funds from customers. The Metro police believe that over 200,000 people in the UK may have been victims of the scam. The police have identified at least 70,000 UK citizens, that were potentially victims of these scams, that they plan on reaching out to.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
