Cyber Intelligence Weekly (February 11, 2024): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Before we get started on this week’s CIW, I’d like to highlight a solution from one of our strategic technology partners. This week, we highlight…
X-Analytics: Cyber Risk Analytics and Quantification Platform

Echelon Risk + Cyber proudly cultivates a diverse network of strategic relationships with leading vendors in the cybersecurity industry. These collaborations empower Echelon to deliver premium services to our clients through cutting-edge technology and valuable insights. In our ongoing effort to bring top-shelf knowledge, each week we want to spotlight a distinguished partner solution offered at Echelon. This week’s focus is on our recently established partnership with X-Analytics (SSIC).
X-Analytics is a robust platform enabling organizations to quantify financial risk in the cybersecurity realm. It harnesses historical data spanning 23 industries and refines its analysis with internal data from your own business. X-Analytics provides comprehensive forms for inputting organizational data, encompassing audits, 10-K reports, insurance policies, and IT infrastructure.
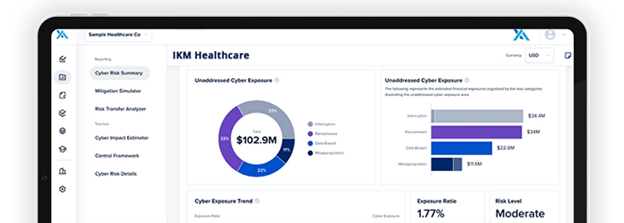
Upon completion of the process, X-Analytics meticulously assesses the data to construct a cyber risk profile for business units, product lines, applications, or security processes. Each profile delivers an estimate of cyber exposure, recommends new strategies to reduce risk, and identifies opportunities to fortify the organization.
X-Analytics empowers organizations to gain cyber-clarity by:
- Translating cyber metrics into financial metrics
- Identifying critical gaps
- Demonstrating which new investments will reduce risk
- Assisting in the management of business exposure to cyber threats
With the conclusion of the insight into X-Analytics, we look ahead with anticipation. Echelon Risk + Cyber remains dedicated to pushing the boundaries of cybersecurity innovation and forging partnerships that empower us to stay at the forefront of industry trends. If your organization is grappling with specific security challenges, allow Echelon to help alleviate the burden. Reach out to discuss how we might help your organization, and stay tuned for more solution highlights in the weeks to come!
Away we go!
1. Beyond NSO Group, The Rise of European Spyware Giants
Google's Threat Analysis Group recently dropped a new report on the proliferation of Commercial Surveillance Vendors (CSVs), and the government hackers they support that exploited previously unknown vulnerabilities in Apple's iPhone operating system last year. In a notable case, these cyber spys utilized spyware developed by Variston, a Barcelona-based startup, to target individuals with sophisticated surveillance technology. The report sheds light on the burgeoning industry of spyware and exploit sellers, highlighting the involvement of several government-backed campaigns leveraging such tools for espionage purposes.
The exploit involved three "zero-day" vulnerabilities, so-called because they were unknown to Apple at the time of their exploitation. The malicious operation was identified in March 2023, targeting iPhone users in Indonesia through a sophisticated method involving a malicious SMS link that installed spyware on the victims' devices, redirecting them to a seemingly innocuous news article. Despite the revelation of these activities, the identity of the government client utilizing Variston's tools remains undisclosed, underscoring the shadowy nature of international cyber surveillance networks.
Variston, founded in 2018 and having acquired the Italian zero-day research company Truel IT, stands out in a report that also mentions other European entities like Cy4Gate, RCS Lab, and Negg, marking a shift in focus from predominantly Israeli firms to European manufacturers in the spyware market. This incident highlights the challenges faced by global cybersecurity efforts in countering the spread of surveillance technologies used against journalists, dissidents, and political figures, posing significant risks to privacy, freedom of speech, and the integrity of democratic processes.
2. The Rise and Pause of OnlyFake, a Glimpse into the World of Synthetic ID Fraud
The underground website OnlyFake, notorious for its ability to produce highly realistic fake IDs through the use of neural networks, has been temporarily shut down. This development follows an investigation by 404 Media, which highlighted the site's capability to create convincing counterfeit documents, including a successful attempt to bypass the identity verification process of a cryptocurrency exchange using a fabricated ID. OnlyFake's swift offline transition underscores the growing concern over synthetic image technologies and their implications for fraud, money laundering, and overall cybersecurity challenges.
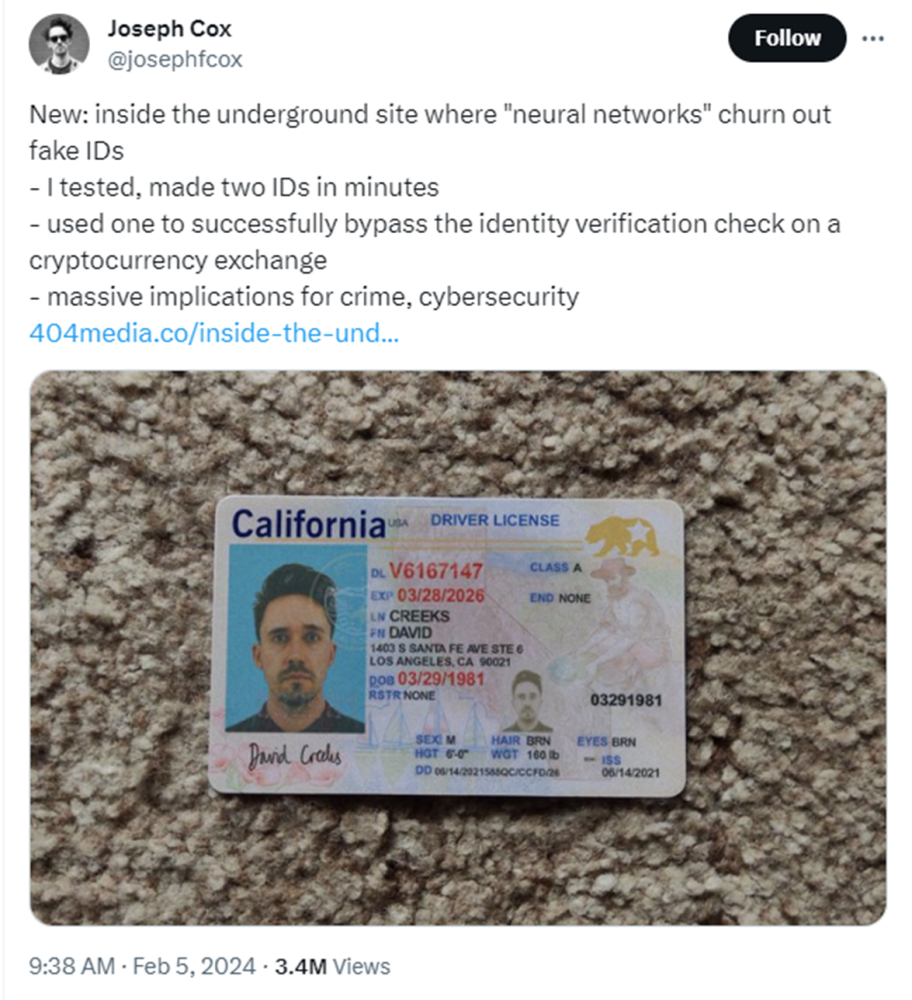
Despite its temporary closure, the legacy of OnlyFake underscores a significant threat in the digital age: the ease with which synthetic images can be used to fabricate identity documents. The site's owner, known by the pseudonym John Wick, had indicated plans to expand the service's offerings, including a selfie generator, hinting at the potential for such technologies to evolve and become more accessible to individuals with nefarious intentions. This situation has sparked debate within the cybersecurity community and among users of the OnlyFake platform, as evidenced by exchanges in a Telegram group dedicated to the site.
The incident with OnlyFake raises critical questions about the responsibility of technology creators in preventing the misuse of their innovations. Despite assertions from the site's administrator that the service was intended for legal use only, the demonstrated application of these fake IDs for bypassing security measures at financial institutions reveals a gap in regulatory and verification frameworks. This episode serves as a reminder of the ongoing battle against fraudulent activities in the digital realm and the necessity for continuous improvement in cybersecurity measures to counteract the sophisticated tools available to cybercriminals.
3. Ransomware's Record Year, The $1.1 Billion Threat
In 2023, ransomware payments surged to a record high of $1.1 billion, marking a significant rebound from a previous downturn in 2022. This stark increase, as reported by Chainalysis, a firm specializing in tracing cryptocurrency transactions, underscores the escalating challenge of ransomware as a major cybersecurity threat. The year 2022 had presented a moment of hopeful decline in ransom payments, suggesting that enhanced security measures, law enforcement efforts, and international sanctions were beginning to curb the tide of ransomware attacks. However, the latest figures from Chainalysis indicate that this was merely a temporary lull in what has become an increasingly lucrative and disruptive cybercriminal enterprise.
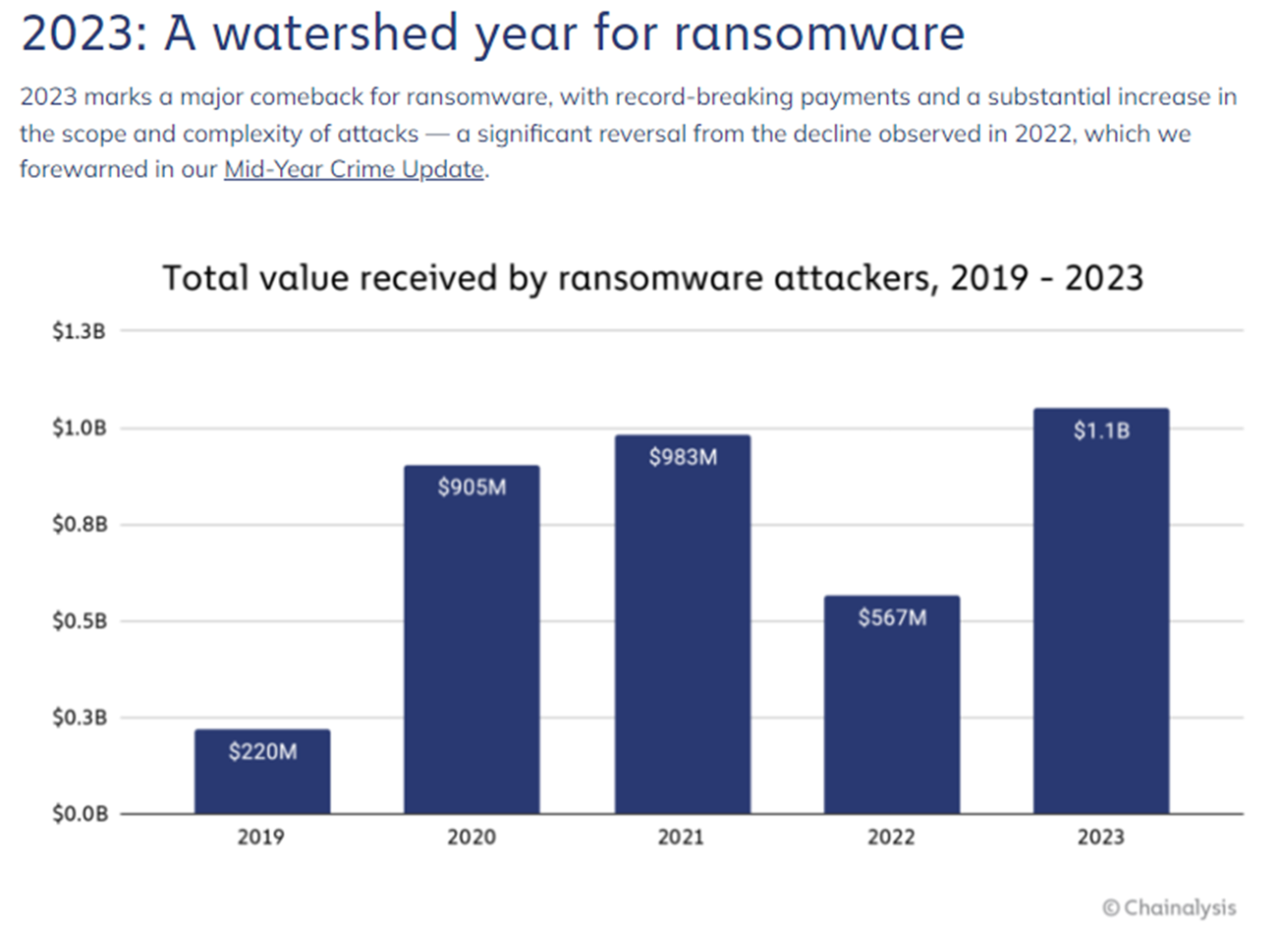
The rise in ransomware payments in 2023 can be attributed to a combination of factors, including a spike in the number of attacks and demands for larger ransoms from selected victims. Despite a decrease in the percentage of victims paying ransoms, the overall volume of attacks and the strategic targeting of entities with a critical need to restore their operations quickly have contributed to the record-breaking total. This trend of "big game hunting" has seen a significant portion of the ransom payments coming from transactions exceeding $1 million. The dynamic nature of ransomware operations, as evidenced by the adaptation and evolution of tactics by ransomware groups, highlights the persistent and sophisticated threat they pose.
The resurgence of ransomware in 2023 also reflects the challenges in disrupting the financial infrastructure that supports these cybercriminal activities. Despite efforts to combat cryptocurrency-related crime and to dismantle ransomware operations, as in the case of the FBI infiltrating the Hive ransomware group, cybercriminals continue to develop new laundering methods and evade capture. The situation is further complicated by geopolitical factors, such as the war in Ukraine, which have had mixed effects on ransomware groups' activities. The ongoing battle against ransomware thus remains a critical concern for cybersecurity professionals, law enforcement, and the wider community, emphasizing the need for continued vigilance, innovation in defense strategies, and international cooperation.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
