DefCon 29 in Review: The Best Sessions, Badge Spoilers and More
For those who don’t know, DefCon is a celebration disguised as a cybersecurity conference. A celebration where hackers and thought leaders come together to discuss new findings and topics, compete against each other in capture-the-flag competitions, and party with new and old colleagues and friends. This month we returned to Vegas after a year hiatus to a very different DefCon 29.
How was it different? The normal sea of people totaling around 20,000 looked to be more like 3,000. The typical nickname of ‘linecon’ didn’t apply this year. The previous time I stood in line to get my conference badge, I waited for close to three hours. This time, I breezed through everything in five minutes. It was great! I even grabbed a few hardware badges, which in the past were almost always sold out. This was probably the perfect DefCon for first-time attendees.
Even with these differences, much still felt the same. The conference badge still offered an enjoyable puzzle; plus, you had all sorts of friendly people throwing out pointers on where to look next. The talks were engaging and interesting. And the parties were REDACTED.
Standout Talks
This year featured interesting topics ranging from breaking into an ATM without a pin or key, to organizing nation states to discuss cyber ‘norms’ and malicious activity at the UN level. While all the talks I attended were engaging, there are two that I consider Best in Show.
The first was A Look Inside Security At The New York Times Or A Media Security Primer For Hackers by Jesse ‘Agent X’ Krembs (https://www.youtube.com/watch?v=U2-8MNx8nsg).
This unique talk discussed threats and problems facing reporters as well as reducing risk through best practices. He talked in depth about the range of threats, from reputation attacks, harassment, and hacking to homicide. I initially assumed this was more of a consideration overseas, but when he hit the audience with a survey showing that 90% of respondents experienced some sort of safety issue / threat within the US, his point felt closer to home.
Overall, the cyber best practices he recommended were typical. Strong passwords, 2FA, VPNs, updating, and secure messaging all made the list. However, his points about the responsibilities of the editor with regards to maintaining the safety of the reporter hit home for me. This section reminded me of the military handled threats during my time there. When sending a reporter into the thick of it, communication cadences and threat reports are critical factors. Overall, this talk opened my eyes to ways that I could help the security of reporters trying to deliver their stories.
My second Best in Show talk was Racketeer Toolkit. Prototyping Controlled Ransomware Operations by Dimitry ‘Op_Nomad’ Snezhkov (https://www.youtube.com/watch?v=VJ8aqReB118).
Typical for DefCon, this talk covered the release of an open-source tool. However, it differed in the nature of the tool being presented and its acute relevance. Racketeer is a ‘defanged’ ransomware command and control platform. As we know, 2021 has been a lucrative year for ransomware threat actors, and clients want to know if they are at risk for this type of attack.
In the past when asked this question, my answer was almost always, “If we get code execution, we could probably execute ransomware.” But with Racketeer, there is no hypothetical. I’ve been using the GitHub release (https://github.com/dsnezhkov/racketeer) and hope to find a way of bringing this as an optional test case to our clients.
Interactive Badges (Spoiler Alert!)
For the first time, I walked out of DefCon with more than two badges. On top of my conference badge, I snagged the Aerospace Village and DefCon TOR 29 badges.
First up is the DefCon badge, and because I’ve completed the puzzle, there are spoilers in the photos below:
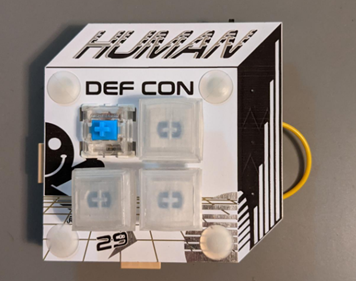
This badge was fun. A few things tripped me up regarding encryption, but everything else seemed to be straightforward. I always feel bad when having to modify the badges (I am possibly the worst at soldering) but thankfully, there wasn’t too much of a need.
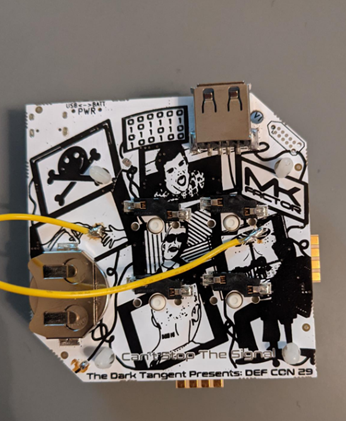
The DefCon theme this year was “Can’t Stop the Signal,” which involved everyone attempting to share the badge signal to reach the next step. All in all, I connected to 64 different badges while sharing the signal only 29 times. Additional to the badge challenge, you can boot the badge into a classic game of Simon (I’ve only been able to get to a high score of 12). The functionality continues when you plug in the badge to your computer, as it acts as a programmable human interface device (HID). I really like this badge.
Next up is the aerospace badge, which I haven’t even started to solve. That said, this is one of the cleanest designs I’ve seen from a village badge, and if you had the DC28 badge, you could connect it to expand the badge.
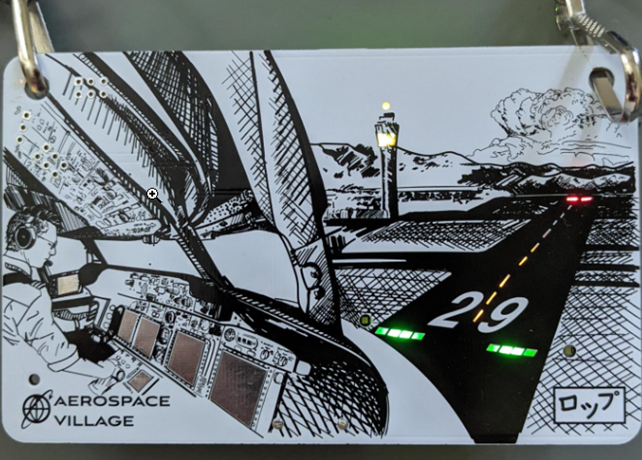
From what I was told, you should be able to interact with the badge and cause the lights to act in different ways following AIM 4-3-13 compliant responses. So I’ll be reading https://www.faa.gov/air_traffic/publications/atpubs/aim_html/chap4_section_3.html
to learn a bit more about these interactions.
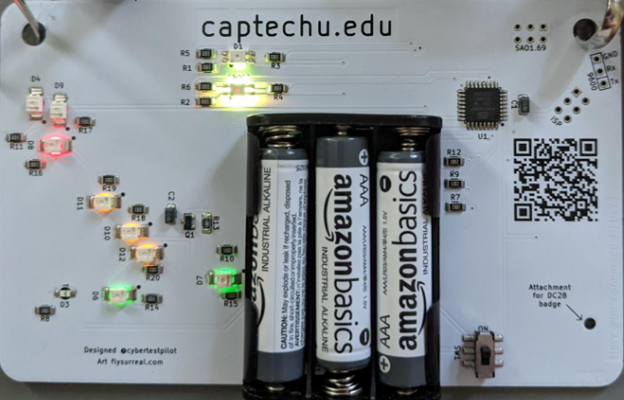
The last badge on the list is the DefCon29 TOR Badge, which is my favorite badge of all time. Not only does it contain a hard challenge, but it also functions as a rudimentary lie detector. Complete with a two-point Galvanic Skin Response (GSR) device and heart rate monitor, you can hook up your friends for shenanigans. Though you do have to take it with a grain of salt, as a real lie-detector machine will have well over 24 GSRs and other sensors, but it is entertaining.

It also has a cheat mode so if you want to force a lie or a truth reaction on the GSR readout, you can make the shenanigan possibilities even higher. I’ve had a lot of fun with this badge so far.
The badge challenge on this one has been a tough one to get through. The starting point involved the morse code on the lanyard, so was easy to figure out, and once running through ROT was KONAMICODEHELPMENU. That brought me to Layer One, which was a fun puzzle, but I’ve been stuck on Layer Two for a minute.

I know I’m probably overlooking something obvious, but I’ve yet to really dig deep. Hopefully I can find some time to complete the puzzle soon.
…About the Parties
What happens in Vegas, stays in Vegas. Except malware.
The Bottom Line
While DefCon 29 felt tame and different, it was still an entertaining trip. To all the speakers and villages in attendance, thank you. I learned a lot on this trip.
To all my friends and colleagues that I shared a drink, it was awesome to see your faces after so long.
Finally, to all the newbies whose first time was DC29: next year is a milestone year, which means its going to be a wild difference from this time around. I’m super excited to see what DC30 will bring us, and I hope to see many more of you there.
If you have any tips you want to share about the badges, need tips, or just want to talk about offensive cyber follow me on LinkedIn at https://www.linkedin.com/in/dahvidschloss/.

