Hacker’s Perspective: Web App Vulnerabilities – Invite Feature
Hidden Dangers Within Your Web App’s ‘Invite’ Feature
Many web applications contain an ‘Invite’ feature, allowing users to invite new users to the platform. Modern web applications often rely heavily on this feature to increase engagement. However, the invite feature is a prime target for attackers because it can be abused to send malicious emails from a legitimate source.
Invite features typically work by sending a user invite through a pre-configured email template. These email templates often add user-defined input, such as the project title or name of the user sending the invite. Here is an example of an invite email’s content:
- Jake_Murphy invited you to Project_Title
As attackers, we are drawn to areas of the application we can inject data into to carry out attacks. This attack would require legitimate access to the application by the threat actor, which can often be accomplished by signing up for a free trial. Using our knowledge of the above pattern, we can change our username to “Customer_Support” and project title to “reset your password at http://attacker.com. Your account has been compromised” to create the following legitimate-looking phishing email:
- Customer_Support invited you to reset your password at http://attacker.com. Your account has been compromised.
Here is an example of the above pattern in action:
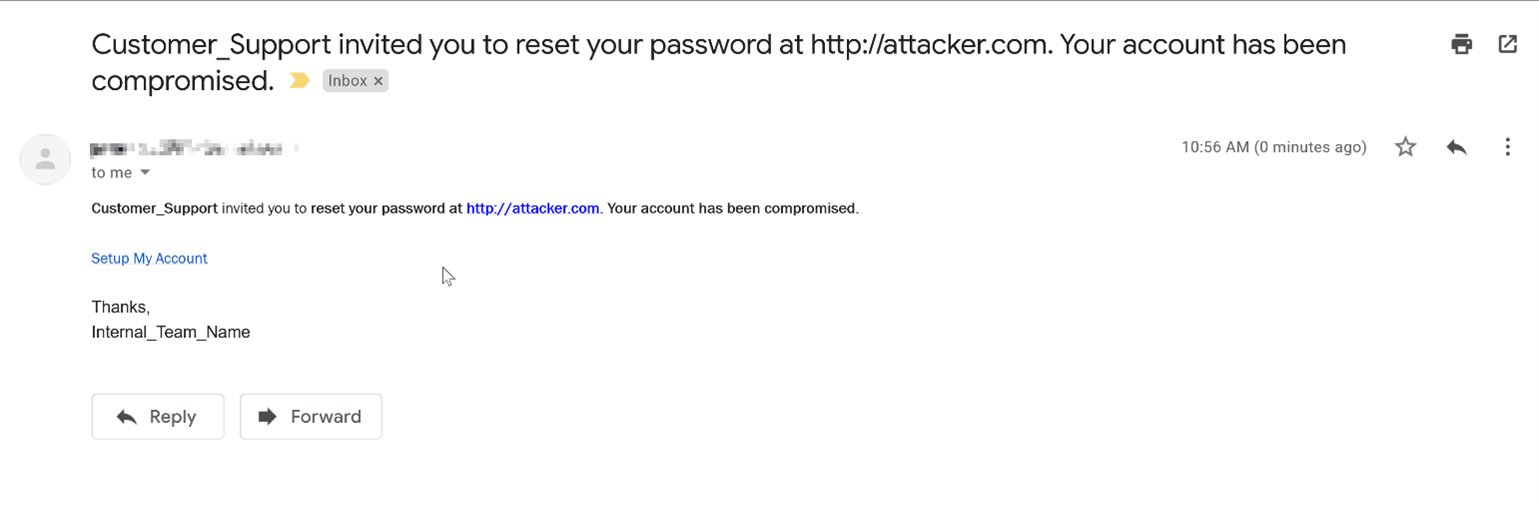
Multiple aspects of this message increase its apparent legitimacy; the email originates from the application’s own trusted email source, and it includes the custom branded colors/fonts as part of the ‘invite’ template. These factors make this attack method especially dangerous and increase the likelihood that a legitimate user would subsequently disclose their credentials.
If a threat actor can guess or gather emails of the application’s current users, they can create a highly effective phishing campaign with relative ease using this method.
Why Does it Matter?
A misconfigured, simple invite feature could allow for a threat actor to create a targeted phishing campaign against users across the globe with ease. The attacker could host a fake login page on any domain they choose and phish specific email addresses directly from the web application’s legitimate email source. Because of this, many users would be unaware of the malicious intent.
This can result in credential compromise affecting many users and could cause legal and compliance nightmares for your organization if there was further harm or damage carried out as a result of the invite feature vulnerability. This could make your organization potentially liable for damages, opening yourself up to legal suits or at best, a PR nightmare. If your application incorporates an invite feature, it is recommended to have it tested for the possibility of various types of exploitation by experienced web application testing professionals that have experience with the threat actor mentality and the use of similar tactics, techniques, and procedures.
How Can You Fix It?
As each application and its invite feature may be coded differently, each recommended fix will depend on the platform’s specific configuration. We suggest a proper penetration test to fully understand how your application may be impacted, and how it can be properly secured. Other than proper testing for these types of vulnerabilities, we suggest the following best practices when developing these features for your web application:
- Restrict links from saving within a user’s profile (first name, last name, project name)
- Provide a character limit for all saved user input
- Limit the amount of user-defined input values placed in ‘Invite’ emails
- Monitor the amount of outgoing ‘Invite’ emails sent by one user account
