Right in your Lapsus$ – How Attackers are Playing a Different Game
Large organizations with cutting-edge security programs base their defenses on sophisticated, nation-state level threat actors. How, then, have so many of them gotten hacked recently by a new and less-sophisticated group, Lapsus$?
It’s simple – attackers are playing a different game.
This article provides a refresher on Lapsus$ and outlines the unique attack flow and implications of an attack that relies on complicit insiders to succeed.
Lapsus$ Refresher
Lapsus$, the hacking group responsible for compromising several major corporations in a short time, has recently made waves in the cyber community. Their sophistication is far below that of APTs, and their roster is believed to be comprised mostly of 16 to 21-year-olds. Nonetheless, their victim list touts major names, including Samsung, LG, Microsoft, Ubisoft, and Nvidia.
Most recently, their attack on Okta gave them major coverage, and since then they have leaked ~70GB of data from Globant, a large app developer.
They have reached such success because their attacks are different. They communicate with their growing Telegram group frequently and use their large following (at the time of writing, nearly 60,000 subscribers) to source exploits and access to companies.
While Lapsus$ does not always disclose how they compromised organizations, there is a general understanding in the group that they are both purchasing access from employees and buying zero-day exploits to get in.
Though Lapsus$ has claimed that only one attack was accomplished by paying an insider, their methods seem to be an open secret in the group.
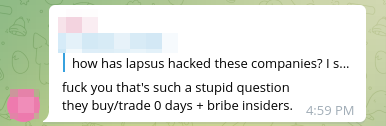
Additionally, followers may assist Lapsus$ and not require money.
The Differences of the Lapsus$ Attack Flow
The Lapsus$ approach varies greatly from the typical threat actor targeting companies of the same grade. The attack flow typically looks like the following:
Obtain access with help from an insider / a purchased exploit
Exfiltrate information
Release information publicly
(Optional Step) Shame company for the specific poor security practices that led to this
Repeat
The key differences in this flow from a ‘typical’ attack are:
1. Initial access is significantly easier when you have an insider helping you
Security programs are currently built to prevent accounts with high levels of privilege from becoming compromised, but rarely focus on the post-compromise security of these accounts. However, if a person with a high level of privilege is actively cooperating with threat actors, the controls can be mitigated, leaving only the more vulnerable post-exploitation attack surface.
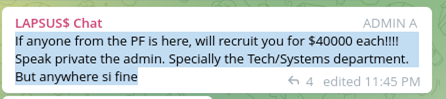
2. Public information release
The key here is not just what information is getting released, but where and how. Lapsus$ releases information to tens of thousands of followers simultaneously, many of whom are actively engaging with the release and encouraging further attacks.
This changes an organization’s attack surface dramatically; not only is this threat group a concern, but now they must consider the ramifications of releasing the results of a compromise to tens of thousands of enthusiastic followers.
This means the security community still has not seen the full consequences of the attacks and leaks so far because they are playing out in real time, furthered by scores of independent operators.
3. Motivations -> Money and Clout
Why are they doing this? Nobody knows. The two biggest contenders are money and clout, as is common with independently operating hacker outfits. The Telegram community chat has been split on what Lapsus$ is after. And despite saying that some attacks are not financially motivated, earlier messages stated differently:
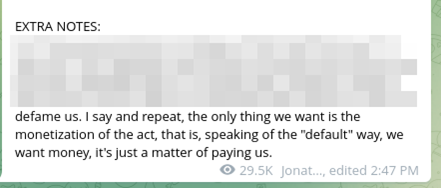
My belief is that the group has various internal motivations and that these motivations have changed over time, especially with how high-profile the group has become. Possibly informing these changes is internal volatility; the members of the group have publicly warred with each other, doxing themselves and others in the process.
Implications for Companies
What does this mean for organizations? It means that even a group that is unhinged and volatile can cause significant damage and disruption to a business by simply abusing implicit trust.
The threats that the cybersecurity community must protect against are not just those that can be mitigated with the newest, shiniest widget, but rather with serious threat modeling around the idea of insiders who are willing cooperators with threat actors.
Additionally, the risk of massive IP release to a community of hackers must be considered – the 70GB of Globant data may contain sensitive information for several other organizations as well as information that may lead to the compromise of Globant applications and sites.
Mitigating the Risk with Zero-Trust
Preparing for this kind of threat requires adhering to Zero Trust principles and technology, especially when adding new technology to your environment. These principles include continuously verifying devices, authenticating users, and limiting user access to least privilege. When setting user permissions, it is important to remember that you are setting them not just for users, but for anyone who compromises their accounts.
Additionally, perform testing to emulate what a Lapsus$-esque attack would look like in your organization. Staging such an attack differs from a traditional pen test in various ways.
We recommend an approach that includes the following activities:
Perform threat profiling of real employees and roles in the organization, e.g., if someone with “this” role got compromised, what would an attacker do with their access?
Test for susceptibility to new vulnerabilities and recently released proof-of-concepts
Put a large emphasis on data leakage / exfiltration:
- Analyze of the type(s) of data that can be exfiltrated
- Assess feasibility for a threat actor to transfer large amounts of data externally through various means
- Analyze of what a data dump of your organization would look like from an attacker’s perspective, i.e., what can be inferred from a no-context dump of your databases
Challenge the trust that your organization places on identity and authorization, and make detailed recommendations for implementing zero trust principles based on environmental observations made during the test
Preparing for modern attacks requires a modern approach to your security programs and testing practices. To keep up, it is imperative to perform tests that speak to the kinds of emerging threats targeting your organization.

