Cyber Intelligence Weekly (August 14, 2022): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Also, we are always looking for great people to join our team. If you know anyone who fits the profiles for any of our open positions, drop me a line and let me know!
Before we get started on this week’s CIW, I’d like to highlight our great team of web application penetration testers. If you didn’t know, we work with leading SaaS companies and developers to help bolster their web application security. If you have a website and want to understand what flaws may be lurking, reach out to us today!

Away we go!
1. Sounding the Alarm on the Emergency Alert System (EAS)
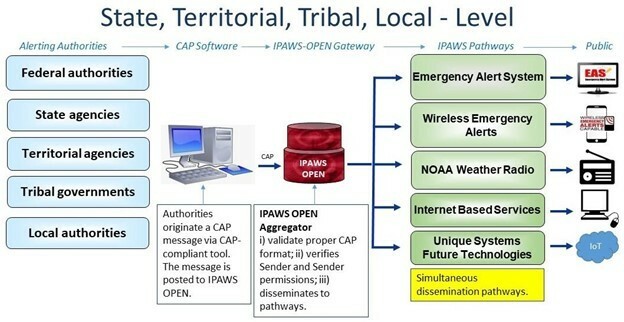
Brian Krebs recently released an article outlining a scary vulnerability within Emergency Alert System (EAS) encoder/decoder devices, that if exploited, could allow a remote attacker to take over the systems. Per an advisory from FEMA’s Integrated Public Alert & Warning System (IPAWS), “We recently became aware of certain vulnerabilities in EAS encoder/decoder devices that, if not updated to most recent software versions, could allow an actor to issue EAS alerts over the host infrastructure (TV, radio, cable network).” IIPAWS is FEMA's national system for local alerting that provides authenticated emergency and life-saving information to the public through mobile phones using Wireless Emergency Alerts, to radio and television via the Emergency Alert System, and on the National Oceanic and Atmospheric Administration's Weather Radio.

Having someone with ill intent taking over these systems could obviously cause some major damage by sending out false alarms and creating public chaos. The EAS encoder/decoder devices in question are made by Digital Alert Systems out of Lyndonville, NY. Digital Alert Systems issued the following advisory earlier this month, citing the security vulnerability that they became aware of back in August of 2019.
One of the most troubling facts is that the alerting authorities that may be operating these devices could be numerous. To top that off, these alerts are meant to broadcast far and wide for public safety reasons, hence the IPAWS OPEN Aggregator functionality in the figure above from FEMA. Basically, one malicious/bad alert could be propagated far and wide if it made it through.
The manufacturer gave some specific of the issue in their advisory, “DASDEC/One-Net software relating to cross-site scripting and other potential issues” and they recommend updating the device firmware to version 4.1 and above, previous software versions are deprecated.
2. Starlink Satellite Dish Hacked with $25 in Parts
As recently reported in WIRED, a security researcher, Leonard Wouters, from Belgian university KU Leuven, released a talk at Black Hat last week entitled, “Glitched on Earth by Humans: A Black-Box Security Evaluation of the SpaceX Starlink User Terminal” showing how to root a Starlink Satellite.
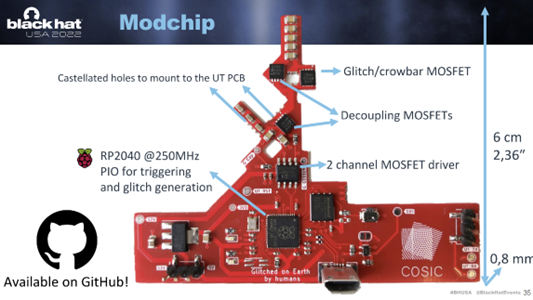
Mr. Wouters’ techniques require physical access to one of the Starlink satellite dishes to be able to execute. He physically dismantled one of the Starlink dishes and created a custom modchip to connect to the device in order to alter the functionality, which eventually allowed him to obtain root access to the dish’s software after using a fault injection attack.
Starlink has awarded Wouters with a bug bounty and has encouraged his research. In fact, after his Black Hat talk, they released a white paper discussing their bug bounty program, the security research they perform, as well as this vulnerability in particular. They had this to say in response to Wouters’ research and Black Hat talk, “First of all we want to congratulate Leonard Wouters on his security research into the Starlink user terminal – his findings are likely why you are reading this, and help us create the best product possible. They describe an attack where invasive physical access (taking apart the Starlink user terminal and attaching wires and additional components to it) can be used to bypass the secure boot protections within the user terminal by messing with the electrical power rails at just the right time during the boot. We find the attack to be technically impressive, and is the first attack of its kind that we are aware of in our system.”
This isn’t the first time Wouters has targeted an Elon Musk owned company, at DEFCON 29 he gave a talk showing how he compromised Tesla’s keyless entry system. Whether he has it out for Musk, or they pay the biggest bounties, I can’t be sure. One thing I am sure of, I agree with the “technically impressive” assessment of Starlink to this research, this one took some dedication and serious hardware know-how.
3. Cisco Confirms Cyber Attack in May of 2022, Ties to $Lapsus
Last week, Cisco announced a network security incident on their corporate blog. The corporate blog post noted, “Cisco did not identify any impact to our business as a result of this incident, including no impact to any Cisco products or services, sensitive customer data or sensitive employee information, Cisco intellectual property, or supply chain operations. On August 10 the bad actors published a list of files from this security incident to the dark web.”

In a follow up blog post from Cisco’s own Talos Intelligence Group, they lay out the post-mortem of how the attack went down. The initial access started with a successful compromise of a Cisco employee’s personal Google account where they had enabled password synching within Google Chrome. This synching allowed the threat actor to gain access to the employee’s Cisco VPN account, then the threat actor bypassed MSA through vishing and/or MFA alert fatigue by sending many VPN push requests.
Once the threat actor was inside, they were able to successfully elevate to administrative privileges and login to several systems. This is the point at which Cisco’s Security Incident Response Team (CSIRT) was alerted to the attack and responded. Cisco’s Talos blog post goes on to describe the threat actor’s movements in much greater detail as well as an attempt to attribute the attack. Cisco’s Talos noted that, “Based upon artifacts obtained, tactics, techniques, and procedures (TTPs) identified, infrastructure used, and a thorough analysis of the backdoor utilized in this attack, we assess with moderate to high confidence that this attack was conducted by an adversary that has been previously identified as an initial access broker (IAB) with ties to both UNC2447 and Lapsus$.”
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
