Cyber Intelligence Weekly (February 5, 2023): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Also, we are always looking for great people to join our team. If you know anyone who fits the profiles for any of our open positions, drop me a line and let me know!
Before we get started on this week’s CIW, I’d like to highlight an upcoming free webinar organized by Shared Assessments where we are going to talk about five ways to enhance business resiliency in 2023.
Tom Garrubba, our Director of Third-Party Risk Management (TPRM) Services at Echelon Risk + Cyber, and Jenna Wells, CTPRP, Global Head of Customer Experience at Supply Wisdom, will serve as panelists for this free event, designed specifically for risk management professionals.
Gain valuable insights on how to effectively manage risks posed by third-party vendors, stay ahead of the game with regards to ESG regulations, and be prepared for cascading risk events that could result in cyber disruptions.
WHEN: Wednesday, February 8th, 2023 from 11:00am-12:00pm ET
REGISTER: https://lnkd.in/gynZZ8is

Away we go!
1. GoodRx Hit with $1.5 Million Fine for Sharing User’s Health Data
In a recent press release from the Federal Trade Commission (FTC), they announced that they had levied a $1.5 million civil penalty against GoodRx, for failing to report unauthorized disclosure of private information to social media giants such as Google, Facebook, and other.
The summary of the alleged bad behavior is actually pretty long, specifically the FTC said GoodRx:
- Shared personal health information with several social media giants.
- User personal health information to target its users with ads.
- Failed to limit third-party use of personal health information.
- Mis-represented its HIPAA compliance.
- Failed to implement policies and procedures to protect personal health information.
Samuel Levine, Director of the FTC’s Bureau of Consumer Protection had the following to say in a prepared statement, “Digital health companies and mobile apps should not cash in on consumers' extremely sensitive and personally identifiable health information. The FTC is serving notice that it will use all of its legal authority to protect American consumers’ sensitive data from misuse and illegal exploitation.”
GoodRx denies any wrongdoing in statement on their website and notes that they entered into the deal to avoid costly litigation. They also noted that they, “…proactively made updates consistent with our commitment to being at the forefront of safeguarding users’ privacy.”
2. VMware ESXi Servers Targeted in Massive Worldwide Ransomware Attack
In a new report from Bleeping Computer, they outline a story of how various administrators, hosting providers, and even the French Computer Emergency Response Team (CERT-FR) are warning of a new attack against a couple year old remote code execution vulnerability (CVE-2021-21974). Per the CVE, “OpenSLP as used in ESXi (7.0 before ESXi70U1c-17325551, 6.7 before ESXi670-202102401-SG, 6.5 before ESXi650-202102101-SG) has a heap-overflow vulnerability. A malicious actor residing within the same network segment as ESXi who has access to port 427 may be able to trigger the heap-overflow issue in OpenSLP service resulting in remote code execution.”
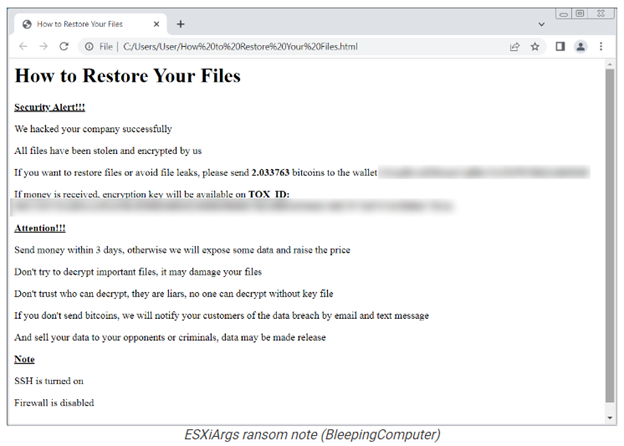
Why the sudden uptick in the exploitation of this old vulnerability is anyone's guess, however, it does look like a new threat actor with a new strain of ransomware is taking advantage of it.
If the host cannot be updated there is a workaround which consists of disabling the SLP service on ESXi hypervisors. Just remember, applying the patch or the workaround may not be enough. If the vulnerable server was exposed to the internet, an attacker may have already exploited the vulnerability and dropped malicious code. It would be wise to perform a compromise assessment to gin better assurance that the threat actors have not compromised the network.
3. Threat Actors Abuse Microsoft’s Verified Publisher Status to Carry Out Attacks
Microsoft was recently alerted to a consent phishing campaign, involving threat actors who have been impersonating legitimate organizations that have enrolled in the Microsoft Cloud Partner Program (MCPP). Microsoft has published a summary of their investigation and results on their blog.
Email security company, Proofpoint, discovered the campaign and released a blog post describing the find. Per the post, they described, “Proofpoint researchers discovered a new malicious third-party OAuth app campaign that abused the Microsoft “verified publisher” status to satisfy some of Microsoft’s requirements on OAuth app distribution. This increased the probability that users were tricked into granting consent when a malicious third-party OAuth app (hereafter referred to as “OAuth app” or “malicious app”) requests access to data accessible via a user’s account. We observed that the malicious apps had far-reaching delegated permissions such as reading emails, adjusting mailbox settings, and gaining access to files and other data linked to the user’s account.”
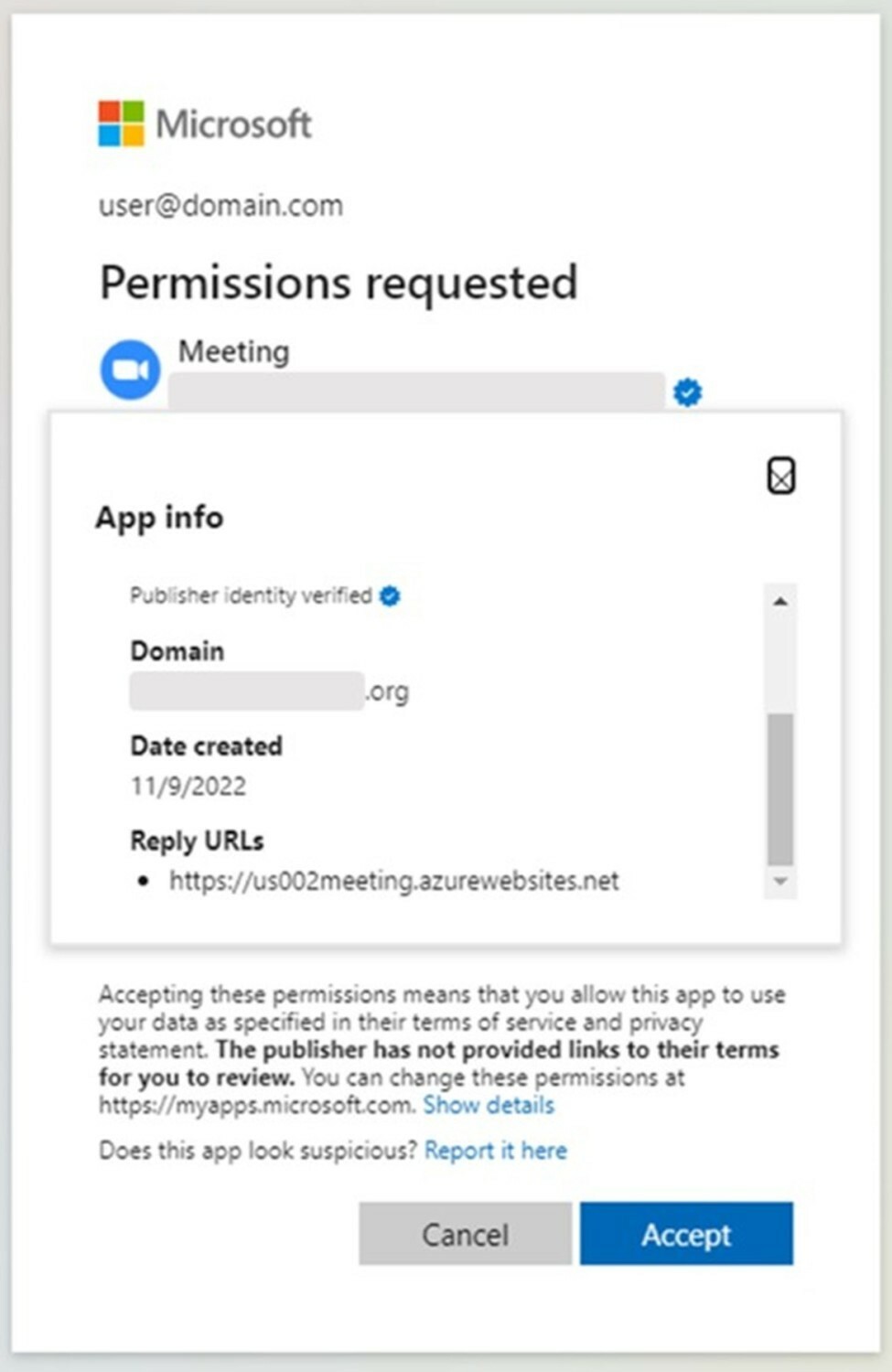
At the end of the day, threat actors used these malicious OAuth applications to exfiltrate emails from the targets that used them. It is pretty scary to think that Microsoft’s own processes can be circumvented this easily and used by threat actors at scale to take advantage of and breach confidential data. There is a blog posting that describes Microsoft’s publisher verification, which is supposed to give app users information about the authenticity of the developing organization. The blue check on Twitter doesn’t mean what it used to anyone, I guess Microsoft falls into that same category now as well.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
