Cyber Intelligence Weekly (Feb 13, 2022): Our Take on Three Things You Need to Know
Welcome to our weekly post where I will be sharing some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
You can also Subscribe to receive Cyber Intelligence Weekly in your inbox each week.
Before we get started on this week’s CIW, I’d like to highlight a new service that our team has been hard at work on. We are constantly looking for ways to give our client’s an edge in the fight against cybercrime. A common theme that we consistently see when we uncover issues on penetration tests and other assessments, is issues and misconfigurations within Active Directory. That is why we created our Active Directory Security Assessment service. It is a focused assessment that helps shine a light on skeletons in the IT closet that are created from Active Directory misconfigurations. Drop me a line if you’d like to learn more about how we can help you tighten the security of your AD environment.

Away we go!
1. Laundering $4.5 Billion of Bitcoin is Apparently Difficult
On Tuesday of last week (February 8, 2022), Ilya Lichtenstein, 34, and his wife, Heather Morgan, 31, both of New York, New York were arrested and accused of laundering a record $4.5 billion worth of stolen cryptocurrency, per a press release from the Department of Justice.
Yes, that is billion, with a “B.” The two allegedly stole nearly 120,000 bitcoins from the cryptocurrency exchange, Bitfinex, in 2016. After the couple allegedly stole the funds, they used several means to split up the bitcoin and funnel it into various other accounts and used various obfuscation techniques such as chain hopping and bitcoin tumbling through a service like that of AlphaBay. Chain hopping is moving funds from one type of cryptocurrency blockchain to another, while bitcoin tumbling is pooling large amount of bitcoin together and then have it come out the other side clean.
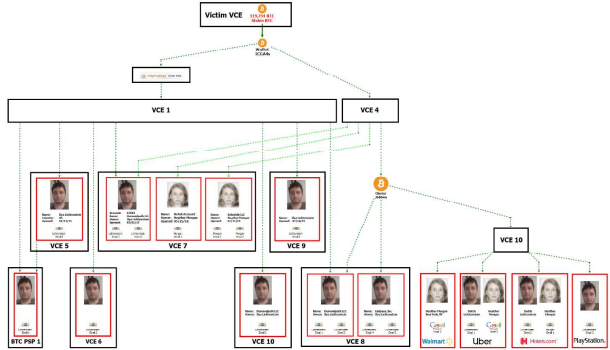
It is uncertain exactly how the IRS traced the funds all the way to their resultant accounts through the obfuscation methods, however, some call out the 2017 bust of AlphaBay as a pivotal point for law enforcement to connect the dots. A breakdown of the fund tracing by the IRS and Department of Justice can be found here. If it wasn’t the shoddy obfuscation techniques used, maybe it was the cringe inducing rap videos that she produced that did the accused in. Warning, the video is pretty awful…
2. Decryptor Released for Several Ransomware Strains
In a bit of positive news from this past week, the supposed threat actor group behind the Maze, Egregor, and Sekhmet ransomware strains have released the master private keys for the various ransomware strains that they were responsible for through a blog post on Bleeping Computer.

Security firm Emisoft has tested and released a decryptor for public consumption on their webpage. While these strains of ransomware and the threat actors behind them are allegedly no longer very active, it is still a big win for IT professionals that may have archived troves of encrypted data in the hopes that they would one day get the keys back. The decryptor currently has 2,458 downloads at the time of this writing.
The Maze ransomware group was made infamous not long ago through their propensity for their execution of double extortion attacks, whereby they will not only encrypt your files, but they will also threaten to post your data publicly online. Many are postulating that these ransomware gangs are somewhat rattled by recent events, such as the recent arrests of the REvil group and have thus taken a more relaxed stance.
3. IRS Transitions Away from Plans to use Facial Recognition
Last week, the IRS announced that it will transition away from its plans to use facial recognition technology, ID.me. In a prepared statement, IRS Commissioner Chuck Rettig said, “The IRS takes taxpayer privacy and security seriously, and we understand the concerns that have been raised. Everyone should feel comfortable with how their personal information is secured, and we are quickly pursuing short-term options that do not involve facial recognition.”
Since last year, the IRS webpage advertised that by the summer of 2022 that taxpayers would have to use the facial scans through ID.me to gain access to records at IRS.gov. Many have challenged the IRS to consider using another option that didn’t require biometrics due to privacy concerns and massive data sharing with an external third party like ID.me.
Many of these challenges have come on the heels of intense criticism of the service and the idea behind using facial recognition as a means for citizens to access important federal resources. The ACLU and others have been citing privacy concerns related to the use of internet based biometric systems to restrict access to government services and how they would put people with disabilities or limited access to technology or Internet at a disadvantage, compounded with concerns that facial recognition systems tend to be less accurate for people with darker skin.
In addition to that, there are some concerns about the effectiveness of the chosen solution, or any solution for that matter. The Washington Post and other news outlets have cited a recent indictment against a California man (Eric Jaklitsch) that was able to bypass ID.me’s identify verification systems that were employed by California’s Employment Development Department (EDD). The EDD is where California citizens file unemployment and other hardship claims. Jaklitsch alleged used fake IDs and selfies where he wore a wig to bypass the identity verification process while filing for unemployment insurance. To their credit, ID.me identified this fraudulent scheme after the fact and referred the case to law enforcement. However, the fact that the man was able to bypass the security and identity verifications has caused a great deal of concern over the principles of the service in general.

Photo Exhibit from U.S. District Court for the Eastern District of California
While I have no doubts that everyone has the right intentions to protect the privacy of US citizens and validate identity before using government services, there are valid concerns across the board that need to be mitigated before anything like this moves forward in a material way.
