Cyber Intelligence Weekly (Jan 30, 2022): Our Take on Three Things You Need to Know

Welcome to our weekly post where I will be sharing some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
You can also Subscribe to receive Cyber Intelligence Weekly in your inbox each week.
Before we get started on this week’s CIW, I’d like to highlight a new series of articles (“Hacker’s Perspective: Web App Vulnerabilities.”) that we are authoring for our “Intelligence” blog. Our team does a significant amount of work hacking web applications on a regular basis and we consistently see the same issues pop up. To give back to the community we’ve decided to author a regular set of articles that highlights these regular issues that we come across, and also give you all some ideas on how to remediate them. Please see our first in the series, Hacking the Invite Feature:
Away we go!
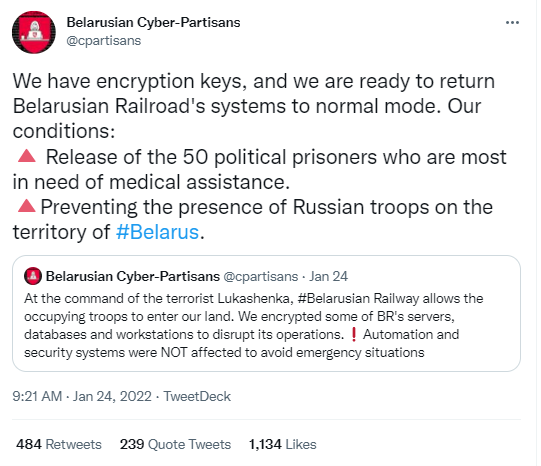
1. Supposed Belarusian “Hacktivists” Disrupt Belarusian Railways with Ransomware
Last week, it was widely reported that state-run railroad system, Belarusian Railways was disrupted through a ransomware attack by a supposed hacktivist group, calling themselves the “Belarusian Cyber-Partisans.” The attack interrupted some services such as ticketing and scheduling, as well as encrypted many major databases and backups at the railway.
The move comes on the heels of the continued buildup of Russian forces on the border with Ukraine. The Belarusian Cyber-Partisans called out the assistance that the state-run railway provides in these operations, and that they are keen on disrupting their operations. Reports show that they have been at least mildly successful in achieving that goal. The below photo is from an anti-regime Belarusian Telegram channel posted on Twitter by Patrick Howell O’Neill showing the buildup of military vehicles and supplies.

What is most interesting about this story is that this hack appears to be using ransomware purely for political purposes, rather than financial gain, which is more of the norm for ransomware. There are some in the industry however that doubt the motivations behind the hack and are skeptical that the Belarusian Cyber-Partisans are actual hacktivists. Juan Andrés Guerrero-Saade of SentinelLABS makes his case of how state sponsored groups often operate under the guise of grassroots operations in his recent blog post. My heart wants me to believe the Luke Skywalker rebel narrative, however, my brain is telling me, let’s see how this plays out.
2. Ukraine Wiper Malware Used Code Repurposed from Another Ransomware
An interesting development popped up last week as Kim Zetter reported on her Substack blog that the wiper used in the attack against Ukrainian government systems, had elements of it that related back to past ransomware strain, called “WhiteBlackCrypt Ransomware.”
The WhiteBlackCrypt ransomware was used against Russian targets over the past couple of years, per the report. Microsoft was also cited in the report as confirming several elements between the two ransomware strains that were similar. Not only does some of the actual malware code line up, but the crypto wallet highlighted in the false ransom demands is also the same.
The researchers close to the details of the malware note that they believe the actors behind WhisperGate may have used the WhiteBlackCrypt ransomware code to potentially plant a false flag and to point the finger internally within the Ukraine and away from potential Russian related involvement.
3. White House Making Good on Promised Cyber Strategy
The White House recently unveiled a plan to move the U.S. Government toward a Zero Trust strategy and infrastructure. The White House press release states this this is a key step forward in delivering on President Biden’s Executive Order from May of last year for improving the nation’s cybersecurity.
The Zero Trust model is one that no longer relies upon the one-time authentication at the edge, which is typically then inherently trusted from that point on. The foundational tenant of the Zero Trust Model is to inherently not trust any device, user, network, etc. and verify anytime something tries to access something.

Per a memorandum published by Shalanda Young, Acting Director for the Office of Management and Budget (OMB), federal agencies will have until the end of the fiscal year 2024 to achieve specific zero trust security goals. They have 30 days from the publication of the memorandum to designate a zero trust strategy implementation lead for their agency.
The goals laid out in the strategy are aligned to the five pillars from CISA that outline protection methodologies at all layers of the infrastructure stack Identity, Devices, Networks, Application & Workloads, and Data.
Lastly, the memorandum outlines several distinct tasks with key milestones, I took the liberty of posting a few below that I believe to be significant:
- Agencies must remove password policies that require special characters and regular password rotation from all systems (within one year).
- Agencies must ensure their EDR tools meet CISA’s technical requirements and are deployed and operated across their agency.
- Agencies must resolve DNS queries using encrypted DNS wherever it is technically supported.
