Cyber Intelligence Weekly (January 29, 2023): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Also, we are always looking for great people to join our team. If you know anyone who fits the profiles for any of our open positions, drop me a line and let me know!
Before we get started on this week’s CIW, I’d like to highlight our cybersecurity predictions for 2023. In this video, Kaushik Kiran, Director of VCISO and Cyber Strategy Services at Echelon Risk and Cyber, shares his predictions for the cybersecurity landscape in 2023. Please check out this and more predictions from our team here: https://echeloncyber.com/cybersecurity-predictions-for-2023
Away we go!
1. Riot Games League of Legends Source Code Stolen, Hackers Demand $10 Million
Riot games announced on January 20th that they have suffered a social engineering compromise of their systems. As the week progressed, they released additional details of the impact of the breach. Most notably, Riot game confirmed that the threat actors were able to steal source code information for League of Legends (LoL) and Teamfight Tactics (TFT) games, as well as the source code for an older anti-cheat platform.
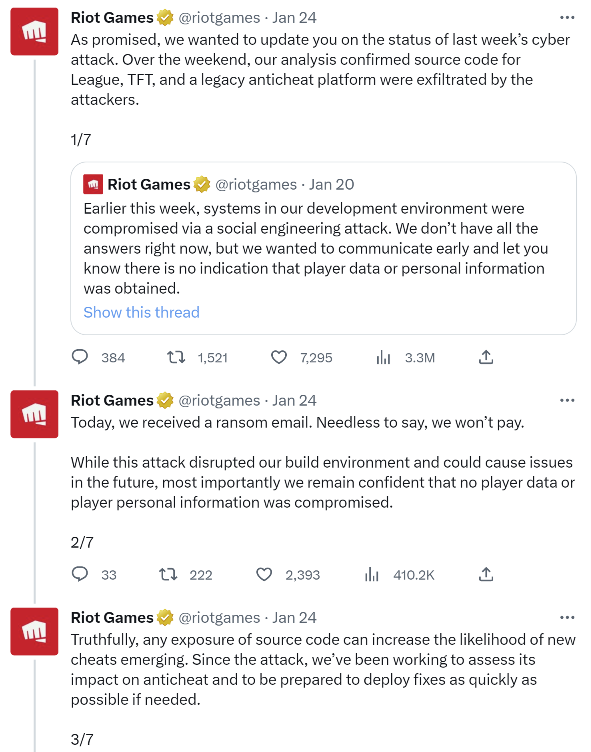
The Vice News Motherboard team received a copy of the ransom email that the threat actors delivered to Riot Games, it reads, “Dear Riot Games, We have obtained your valuable data, including the precious anti-cheat source code and the entire game code for League of Legends and its tools, as well as Packman, your usermode anti-cheat. We understand the significance of these artifacts and the impact their release to the public would have on your major titles, Valorant and League of Legends. In light of this, we are making a small request for an exchange of $10,000,000.”
Riot Game has said through their Twitter account that they don’t plan on paying the ransom. They also noted on their Twitter account that they plan on releasing full details of how the breach occurred and committed to full transparency to their customers.
2. For LastPass Owner, GoTo, Breach Situation Gets Worse
The owner of LastPass, GoTo (formerly LogMeIn), suffered an initial breach last November and they are providing an update on this breach for the first time since November 30, 2022, when they stated that they hired Mandiant and were investigating the breach.
Needless to say, this long-awaited update was a doozy. Paddy Srinivasan, CEO of GoTo, had the following to say in the company update, “Our investigation to date has determined that a threat actor exfiltrated encrypted backups from a third-party cloud storage service related to the following products: Central, Pro, join.me, Hamachi, and RemotelyAnywhere. We also have evidence that a threat actor exfiltrated an encryption key for a portion of the encrypted backups. The affected information, which varies by product, may include account usernames, salted and hashed passwords, a portion of Multi-Factor Authentication (MFA) settings, as well as some product settings and licensing information. In addition, while Rescue and GoToMyPC encrypted databases were not exfiltrated, MFA settings of a small subset of their customers were impacted.”
Most notable in this update is the fact that the threat actor was able to exfiltrate backups, as well as encryption keys for a “portion” of them. That sounds, well, not great. The hits keep on coming for GoTo. Time will tell what impacts these sort of breaches will have on the company, but for a security and technology focused company, it likely isn’t good.
3. CISA, NSA, and MS-ISAC Release Advisory on the Malicious Use of RMM Software
I received a very interesting alert from CISA this past week that I though was worth reporting on. Back in October of 2022, CISA noted that they identified a widespread hacking campaign that was leveraging the use of legitimate remote monitoring and management (RMM) software. Most concerning, performed a retrospective analysis of a federal civilian executive branch (FCEB) intrusion detection system (IDS), called EINSTEIN, and found evidence of suspicious activity on two FCEB networks.
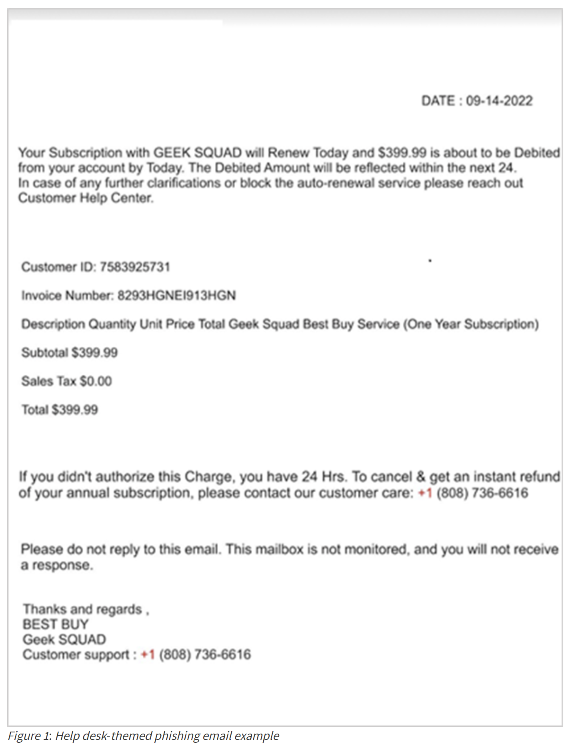
Help-desk themed phishing attacks were used to trick federal employees into refund scams, whereby the attacker would leverage RMM software to connect to the employee’s computer remotely, enticing the employee to login to their banking accounts, the threat actor then modifies the recipient’s bank account summary through the browser. This falsely modified bank account summary then shows the recipient was mistakenly refunded an excess amount of money. The threat actors then instructed the recipient to “refund” this false excess sum to them.
What is most concerning is that RMM software bypasses most traditional anti-virus tools and common software that looks for malicious signatures. The CISA alert provides many mitigation ideas, such as reviewing logs for RMM tool activity that is abnormal to your organization as well as using more advanced EDR style tools (e.g., CrowdStrike Falcon) that would catch RMM tools being loaded in memory.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
