Cyber Intelligence Weekly (April 28, 2024): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Before we get started on this week’s CIW, I’d like to highlight that Echelon Risk + Cyber is proud to be represented by Dan Desko (me!), Chad E. LeMaire, and Chris Furtick at RSA this year!
Join Dan, Chad, and Chris at RSA! They are ready to dive into discussions on the latest cyber defense techniques, exchange key insights, or help you enhance your network with their seasoned expertise.
For more details on how you can interact with us at RSA, check out our page: https://lnkd.in/dW8hvcNy
We’re excited to turn #RSAC into a focal point for partnership and creativity. See you there!

Solution Partner Highlight – Prevalent

Echelon Risk + Cyber proudly cultivates a diverse network of strategic relationships with leading vendors in the cybersecurity industry. These collaborations empower Echelon to deliver premium services to our clients through cutting-edge technology and valuable insights. In our ongoing effort to bring top-shelf knowledge, each week, we want to spotlight a distinguished partner solution offered at Echelon. This week’s focus is on Prevalent’s Third-Party Risk Management Platform.
Prevalent's unified platform for third-party vendor and supplier risk management represents a paradigm shift in risk reduction and compliance. Their SaaS solution seamlessly integrates automated, standardized risk assessments with continuous monitoring, assessment workflow, and remediation management across the entire lifecycle of third-party engagements.
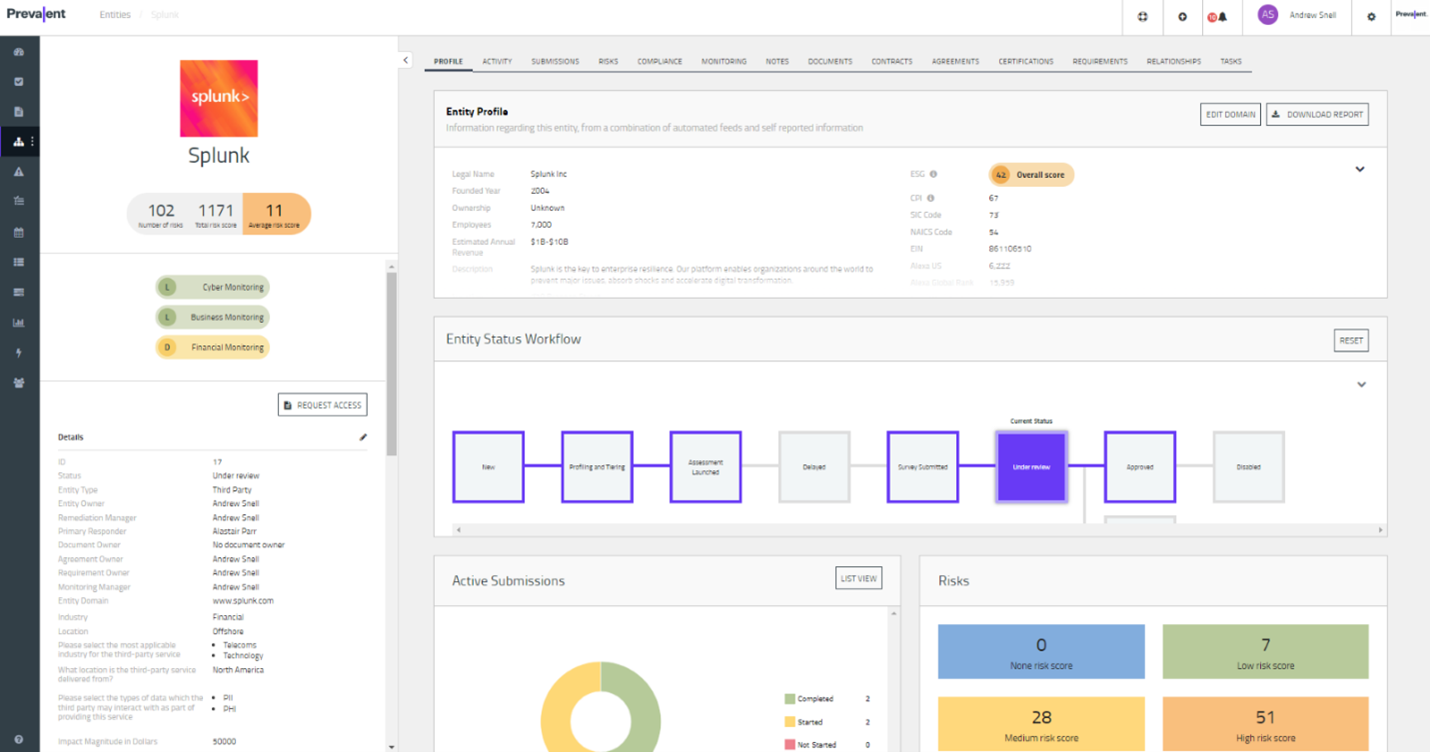
The Prevalent platform is complemented by vendor intelligence networks offering on-demand access to completed, standardized risk reports on thousands of companies. What sets the Prevalent platform apart are its standout features:
- Sourcing and Selection: Prevalent empowers procurement teams to streamline vendor sourcing and selection processes, reducing cost, complexity, and risk exposure.
- Intake and Onboarding: Security and risk management teams benefit from a centralized hub for supplier risk profiles, intake processes, and seamless onboarding/offboarding workflows.
- Inherent Risk Scoring: Prevalent constructs comprehensive vendor risk profiles, complete with inherent risk scores, guiding users on the likelihood and potential impact of security and compliance risks.
- Risk Assessment: Prevalent simplifies TPRM by assessing vendors across various dimensions including security, compliance, performance, contractual obligations, business continuity, financial health, reputational standing, ethics, and diversity.
- Risk Monitoring: With Prevalent, organizations gain continuous insights into emerging threats, validating assessment results, and enabling proactive risk mitigation strategies.
- SLA & Performance Management: Prevalent facilitates seamless collaboration between procurement, risk, and vendor management teams, offering centralized measurement of program effectiveness and SLA analysis.
- Offboarding and Termination: Automating contract assessments and offboarding procedures, Prevalent reduces the risk of post-contract exposures for organizations.
With the conclusion of the insight into Prevalent’s Platform, we look ahead with anticipation. Echelon Risk + Cyber remains dedicated to pushing the boundaries of cybersecurity innovation, forging partnerships that empower us to stay at the forefront of industry trends. If your organization is grappling with specific security challenges, allow Echelon to help alleviate the burden. Reach out to discuss how we might help your organization and stay tuned for more solution highlights in the weeks to come!
Away we go!
1. Massive Data Breach at UnitedHealth Affects “Substantial Proportion of People in America”
The UnitedHealth cyber breach saga seemingly keeps getting worse. If you recall, UnitedHealth Group disclosed that a ransomware attack targeting its subsidiary, Change Healthcare, led to the theft of private healthcare data concerning a significant number of Americans. While specific figures on the number of individuals affected were not disclosed, the company indicated that the stolen data could potentially impact a vast swath of the U.S. population. Change Healthcare, a key player in the health tech sector, processes insurance and billing information for numerous healthcare providers nationwide, thereby accessing extensive health data on roughly half of all Americans.
Based on initial targeted data sampling to date, the company has found files containing protected health information (PHI) or personally identifiable information (PII), which could cover a substantial proportion of people in America. To date, the company has not seen evidence of exfiltration of materials such as doctors’ charts or full medical histories among the data.
The breach was first brought to light when a new hacking group, known as RansomHub, began to publish parts of the stolen data online in an attempt to extract a secondary ransom from UnitedHealth. Despite prior payments totaling $22 million to another group, ALPHV, for an earlier breach, UnitedHealth confirmed they again conceded to a ransom demand to safeguard patient data from further exposure. The ongoing situation underscores the severity of the breach, which not only compromised patient information but also significantly disrupted healthcare services across the country, resulting in substantial financial losses for UnitedHealth.
UnitedHealth's handling of the incident has come under scrutiny as the healthcare system continues to grapple with the aftermath of the attack. With disruptions causing widespread outages in pharmacies and hospitals, the attack has had far-reaching implications for patient care and financial stability within the sector. As the company works through the extensive data review process, which is expected to take several months, the broader implications for healthcare data security and ransomware attacks on critical infrastructure are becoming starkly apparent.
2. GitHub Exploit: Malware Masquerades as Microsoft Repo Files
A recent cybersecurity concern has emerged from GitHub, where a potential flaw in the platform's design is being exploited by hackers to disseminate malware using URLs that appear to be from legitimate Microsoft repositories. This issue stems from GitHub's feature that allows users to attach files to comments within project repositories. These files, once uploaded, are hosted on GitHub's CDN and are presented with URLs that misleadingly suggest they are official project files. Notably, this vulnerability was highlighted through URLs pointing to malware disguised as legitimate software from Microsoft's repositories, specifically mimicking components like the C++ Library Manager (vcpkg) and the STL library.
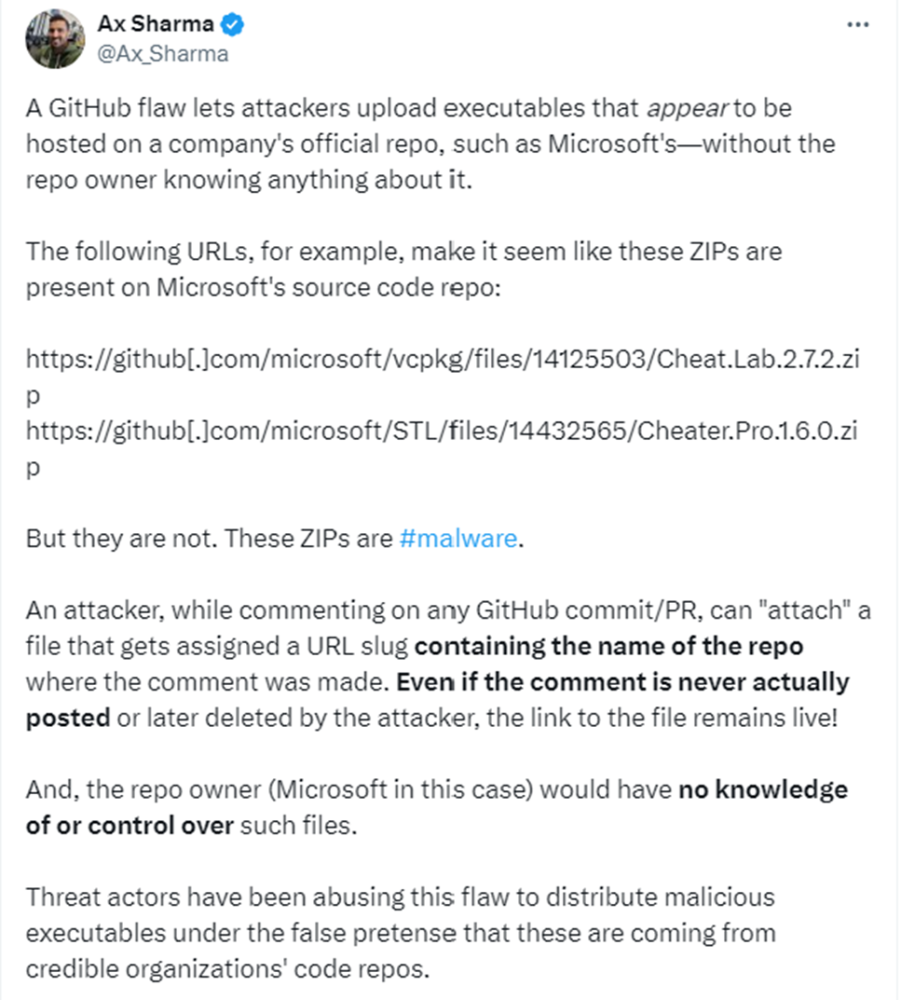
The security firm McAfee unearthed this deceptive method when it discovered a new LUA malware loader that seemed to be distributed through Microsoft's vcpkg repository. This discovery has raised alarms about the ease with which malicious files could be associated with well-respected repositories, creating highly credible lures for potential victims. Despite the appearance of these URLs, investigations such as those by BleepingComputer revealed that these files were never part of the official project code but were instead attachments in comments made on the platform.
The exploitation of this GitHub functionality poses significant risks not just for unsuspecting users but also for the reputations of companies whose repositories are mimicked. GitHub and Microsoft were contacted regarding this misuse of repository URLs for malicious purposes but had not responded at the time of the initial reports. The persistence of accessible malware through this method underscores the ongoing challenges and potential threats posed by sophisticated cyber-attacks leveraging trusted digital platforms.
3. ArcaneDoor Exploit, How Cisco Firewalls Became Gateways for Spies
Cisco has recently warned that its security appliances, specifically the Adaptive Security Appliances, were compromised by sophisticated cyber espionage efforts targeting government networks globally. This campaign, dubbed ArcaneDoor, leveraged previously unknown vulnerabilities within Cisco's equipment to facilitate unauthorized access and data exfiltration. The implicated devices, which combine functionalities like firewalls and VPN services, are integral to network security, making their compromise particularly concerning. Cisco's investigation, supported by insights from Microsoft and other cybersecurity entities, suggests that the hackers were state-sponsored, pointing to a high level of strategic planning and technical prowess.
The vulnerabilities exploited by the attackers, referred to by Cisco as Line Dancer and Line Runner, allowed them to execute malicious code and maintain persistent access to the compromised networks, even through device reboots and updates. This breach underscores the criticality of edge devices in network security architectures and the potential they hold as entry points for sophisticated adversaries. Following the discovery of these breaches, Cisco has issued patches and strongly advised their immediate implementation by all users of the affected products. Moreover, a hard reboot of the devices, which involves physically disconnecting them, has been recommended as a temporary countermeasure to disrupt any ongoing unauthorized access.
The ArcaneDoor incident is a sobering reminder of the evolving landscape of cyber threats, particularly those orchestrated by state actors with specific espionage agendas. These threats increasingly exploit the very tools designed to protect digital infrastructures, turning them against the organizations they are supposed to safeguard. As cyber adversaries continue to refine their tactics and target critical infrastructure, the importance of robust cybersecurity measures and rapid response to emerging threats becomes ever more apparent.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
