Cyber Intelligence Weekly (October 2, 2022): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Also, we are always looking for great people to join our team. If you know anyone who fits the profiles for any of our open positions, drop me a line and let me know!
Before we get started on this week’s CIW, I’d like to highlight one of newest hires, Steve Snider. Steve is a Senior Offensive Security Consultant at Echelon where he brings nearly twenty years of experience to the Echelon team. Steve previously worked as an operator for offensive cyber operations with DoD organizations and intelligence agencies. Following his military career, he spent four years performing red team assessments, adversarial emulation engagements, penetration testing, and wireless assessment for large organizations during his time working as part of a Big 4 consulting firm. Please help me welcome Steve to the team!

Away we go!
1. Microsoft Exchange Server Experiencing Two New Zero-Day Vulnerabilities
The popular enterprise email tool, Microsoft Exchange, has a long history of serious issues and vulnerabilities discovered within its code. This past week did not help the buggy reputation of Exchange. Microsoft has reported two new previously unknown vulnerabilities in their Exchange Server product that are very serious in nature. The first vulnerability, identified as CVE-2022-41040, is a server-side request forgery (SSRF) vulnerability, and the second one, CVE-2022-41082, allows for remote code execution (RCE) when Exchange PowerShell is accessible to the attacker.
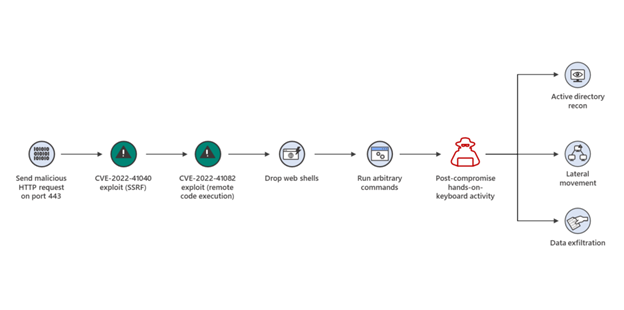
Microsoft Security Threat Intelligence: Diagram of attacks using Exchange vulnerabilities CVE-2022-41040 and CVE-2022-21082
The Microsoft Security Threat Intelligence (MSTC) center has observed a small number of targeted attacks in the wild exploiting these vulnerabilities in tandem. In these cases, the threat actors dropped a web shell that allowed hands-on-keyboard access and the threat actors then performed Active Directory reconnaissance and data exfiltration. MSTC believes that the group behind the initial exploitation is state-sponsored in nature.
As far as mitigation goes, the above noted blog posts outlines the mitigation steps for on-premises Exchange, while Microsoft Exchange Online customers do not need to take any action.
2. LinkedIn Riddled with Fake Fortune 500 CISO Profiles
A new report from Brian Krebs last week outlined a slew of fake CISO profiles on LinkedIn that appear to be targeting some big companies, many in the Fortune 500. In the example screenshot below is a profile for Victor Sites, fake CISO for Chevron. In the profile it says Victor is from Westerville, OH and that he attended Texas A&M University.
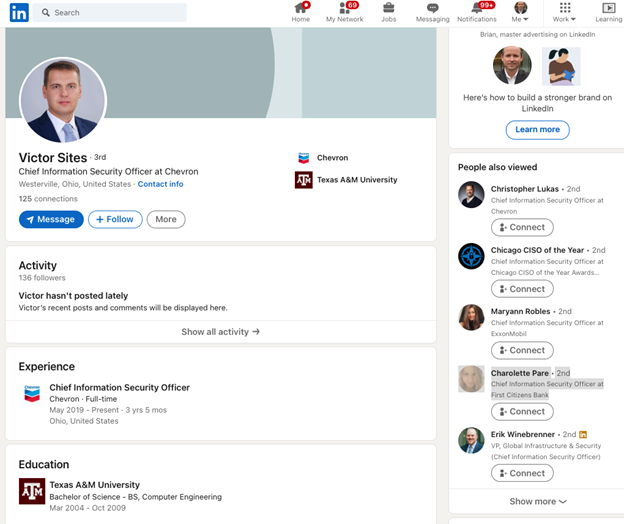
Source: www.krebsonsecurity.com
There is concern that these profiles could be used to help perpetrate fraud or carry out cyber attacks. What was especially concerning in these cases was how downstream data aggregators (e.g., top CISO lists in America) scrape this LinkedIn data and accept it as truth in many cases. Krebs reached out to LinkedIn, and they noted that they have several human and automated systems to combat fake profiles, however some still slip through the cracks. There is really no telling who is behind these false profile attempts, but it is concerning given how much people rely on sources like LinkedIn as a source of truth.
3. Fast Company Content Management System Hacked, Offensive Apple News Alert Sent
Last week, the popular news website, Fast Company was hacked and the hacked abused their content management system to post obscene language on their website as well as push out an offensive news alert via the Apple News aggregator.
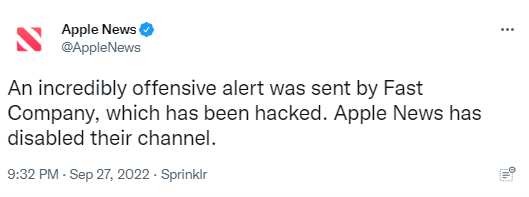
Per a Bleeping Computer article, the hacker took over the Fast Company content management system and site because they found a WordPress instance that was allegedly secured using only HTTP basic authentication with a very easy default password.
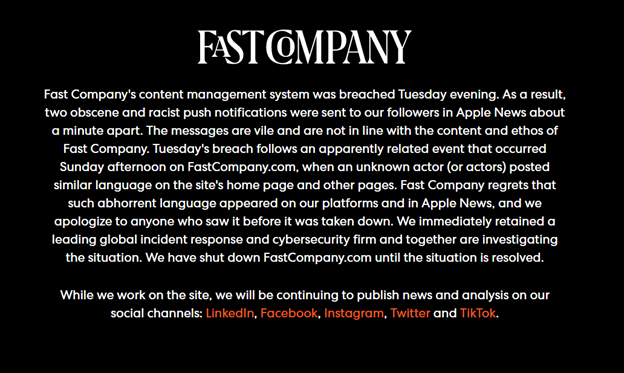
The Fast Company website is still down as of this writing. While the hacker decided in this case to simply embarrass Fast Company, they could have made a choice to deliver a fake news alert that could have had sparked a panic or caused much harm. This begs the question, should news outlets and large sources of online media be subject to regular cybersecurity guidelines and audits much like other critical resources and infrastructure organizations?
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
