Cyber Intelligence Weekly (September 24, 2023): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Before we get started on this week’s CIW, I’d like to highlight Episode 1 of our Hackin’ SaaS Webinar Series on October 10th, 2023, where we dive deep into the world of SQL Injection.
At Echelon, our Offensive Security team confronts web app vulnerabilities daily, and SQL Injection remains one of the most prevalent threats. In this webinar, we'll not only demonstrate how to break into SQL statements but also teach you how to prevent these attacks.
Don't miss this chance to boost your application security expertise and safeguard your web apps with Jake Murphy, Evan Isaac, and Kristofer Johnson. Secure your spot now!
📅 Date: October 10th, 2023
🕒 Time: 3:00 PM EST
Register for this LinkedIn Live event here: https://www.linkedin.com/events/hackin-saas-top10webappvulnerab7105295202419949568/theater/

Away we go!
1. Caesars Entertainment Confirms Major Data Breach in SEC Filing
Caesars Entertainment, a popular hotel and casino conglomerate, confirmed on Thursday that a significant amount of customer data was stolen in a recent cyberattack, validating prior media reports. The company disclosed in an 8-K notice submitted to federal regulators that hackers acquired a copy of its loyalty program database. This database contains sensitive data, including driver's license and Social Security numbers of a considerable number of members. An 8-K notice is a requirement for public companies to report events that could substantially impact their business.

While Caesars acknowledged that other data was compromised during the breach, specific details were not provided. The exact number of individuals affected by this incident remains uncertain. The company's statement in the SEC filing suggests that they have paid a ransom, aligning with a Wall Street Journal report that Caesars paid half of the demanded $30 million to the hackers to inhibit the release of the stolen data.
The breach was reportedly executed by leveraging social engineering tactics on an external IT vendor, as per Caesars' separate data breach notice. Bloomberg suggests that the hackers, believed to be the group called Scattered Spider or UNC3944, initiated their attack on Caesars in late August. This group is notorious for using social engineering techniques to dupe employees into providing access to expansive corporate systems. Notably, Caesars is the second hotel and casino behemoth to suffer a cyberattack recently, following MGM Resorts, which also experienced a significant "cybersecurity issue." While the FBI is actively investigating the MGM incident, they refrained from commenting on the Caesars situation. Caesars, adhering to protocols, has reported the cyberattack to law enforcement.
2. Rise in Thefts of Kia and Hyundai Vehicles in U.S. Cities, Patch Coming to Help
U.S. cities are witnessing an alarming surge in car thefts, particularly involving Kia and Hyundai vehicles. Recent data from Motherboard indicates that cities such as Chicago, Denver, and Atlanta are experiencing theft rates much higher than previous years. For instance, Chicago has seen its average monthly stolen cars jump from around 850 to over 2,000. These heightened theft numbers are largely attributed to Kia and Hyundai vehicles, which were sold in vast numbers, exceeding nine million over a decade, without integral anti-theft technology. This absence makes these cars exceedingly easy to steal.
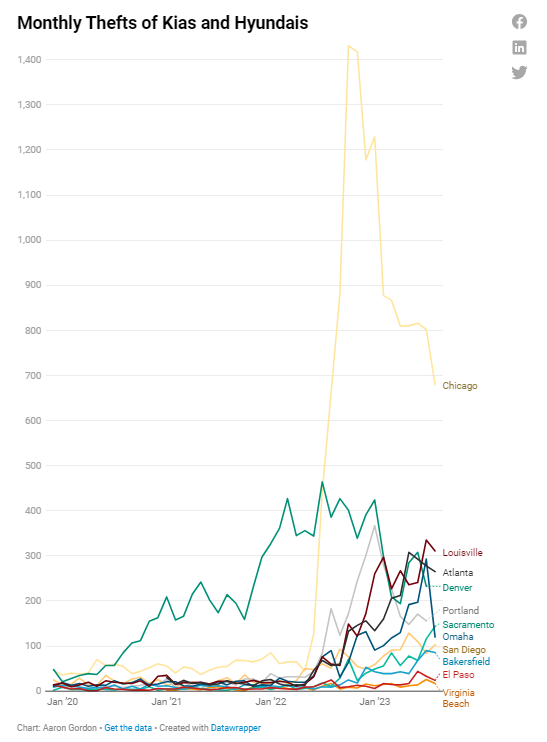
To gain more insight into the magnitude and consequences of the thefts, Motherboard sourced car theft data from police departments in the top 100 U.S. cities by population and also incorporated data from lawsuits lodged by 17 cities against Kia and Hyundai. It was revealed that from 2011 to 2021, many Kia and Hyundai vehicles, especially the more affordable models, lacked engine immobilizers. This anti-theft device, costing around $100 to integrate, thwarts hot-wiring attempts. While such anti-theft devices are mandatory in Canada and are standard in most of the auto industry, only about 26% of Kias and Hyundais in the U.S. had them by 2015. This glaring security gap, paired with a new subculture known as "Kia Boys" or "Kia Boyz" that has made a game out of pilfering these cars, has fueled an unprecedented surge in car thefts. In many cities, the stolen car rates have skyrocketed, with thefts of Kias and Hyundais in particular increasing exponentially.
To further exacerbate the issue, stealing a Kia or Hyundai without an immobilizer is shockingly simple. Equipped with just basic tools like a screwdriver and a USB cord and after viewing a couple of tutorials, almost anyone can steal these cars. Lawsuits filed against Kia and Hyundai suggest that the majority of these thefts are executed by teenagers, many not even of driving age. These vehicles are often used for joyriding, vandalism, or even to perpetrate other crimes. Current efforts by both car manufacturers and law enforcement to curb this trend have so far proved largely ineffectual.
After months of thefts the car makers are offering free software updates to roughly 8.3 million cars that can be stolen with the aid of a USB-A cable. The National Highway Traffic Safety Administration said that the manufacturers' updates make it so affected cars require a key to be in the ignition switch to start. The cars' no-key alarms will also sound for one minute instead of 30 seconds. The updates should start arriving later this month, with phased rollouts over subsequent months for 3.8 million Hyundais and 4.5 million Kias.
3. Microsoft AI Researchers Accidentally Expose 38TB of Data
Wiz Research identified a significant data exposure on Microsoft’s AI GitHub repository caused by a misconfigured SAS (Shared Access Signature) token. Due to this error, 38 terabytes of confidential data, including over 30,000 internal Microsoft Teams messages, were accidentally made accessible. Along with the intended open-source training data, the misconfiguration revealed private data, including two employees' workstation backups, containing passwords, secret keys, and private messages.
The root cause of this oversight is due to the way SAS tokens inherently work. In Azure, SAS tokens grant access to Azure Storage data, and their permissions range from read-only to full control. This granularity can be powerful but also presents risks when misconfigured. In Microsoft’s case, a link intended for specific data shared the entire storage account, which was made even riskier by the token having "full control" permissions. This allowed for not just viewing, but also overwriting and deleting files in the storage account. A significant security concern was that attackers could potentially tamper with the AI models in this storage, leading to users unknowingly using malicious code.
There are inherent risks in using SAS tokens, especially concerning permissions, hygiene, and management. Tokens often have very long lifetimes, and monitoring their use can be both challenging and costly. The Microsoft incident shines a spotlight on the urgency of better managing these tokens. Recommendations include treating Account SAS tokens with the same caution as account keys, using Service SAS with a Stored Access Policy for external sharing, and leveraging User Delegation SAS for time-limited sharing. Monitoring tools, such as Azure Metrics and secret scanning tools, can also be employed to enhance security and detect potential breaches in time.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
