Cyber Intelligence Weekly (September 25, 2022): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Also, we are always looking for great people to join our team. If you know anyone who fits the profiles for any of our open positions, drop me a line and let me know!
Before we get started on this week’s CIW, I’d like to highlight the wonderful time we had at CrowdStrike’s Fal.Con conference this past week at the Aria in Las Vegas. The week was full of wonderful talks as well as learning about all the new features and functionality coming to the platform. CrowdStrike really knows how to take care of its partners and customers, and we can’t wait to go back again next year!

Away we go!
1. Microsoft Releases Out-of-Band Security Update for Microsoft Endpoint Configuration Manager
Per a recent bulletin from the United States Cybersecurity and Infrastructure Agency (CISA), Microsoft has recently released a security update to address a serious vulnerability in Microsoft Endpoint Configuration Manager. The vulnerability has been published as CVE-2022-37972, which is described as a Microsoft Endpoint Configuration Manager Spoofing Vulnerability.
Microsoft Endpoint Configuration Manager, formerly System Center Configuration Manager (SCCM) and Systems Management Server (SMS) is a systems management software product developed by Microsoft for managing large groups of computers providing remote control, patch management, software distribution, operating system deployment, and hardware and software inventory.

The Microsoft Endpoint Configuration Manager vulnerability had to do with allowing NTLM connection fallback. There is a newly released patch (KB15498768) where this update prevents any attempt at NTLM authentication for client push style of installation when the “Allow connection fallback to NTLM” option is disabled. Prior to this patch it was possible to force NTLM auth for the “Client Push” account. The “Client Push” account is a risky account because this account is used to connect to computers and install the Microsoft Endpoint Configuration Manager client software. We recommend installing this patch as soon as possible to prevent exploitation of this vulnerability.
2. American Airlines Data Breach Exposes Employee and Customer Data
American Airlines recently disclosed a data breach that has supposed only affected a small number of customers. Per a recent breach disclosure letter, American Airlines disclosed the potential scope of the breach, “In July 2022 we discovered that an unauthorized actor compromised the email accounts of a limited number of American Airlines team members. Upon discovery of the incident, we secured the applicable email accounts and engaged a third party cybersecurity forensic firm to conduct a forensic investigation to determine the nature and the scope of the incident. Our investigation determined that certain personal information was in the email accounts.”
While the breach disclosure statement states they don’t have any evidence that the personal information found in the emails was misused, they decided to inform the potential victims out of an abundance of caution. An article covering the matter through Bleeping Computer included a statement from a company spokesperson that noted a small number of employees accounts were compromised through a phishing attack, and a small amount of employee and customer personal data were included in those email boxes.

It is no secret that people tend to store all types of data they shouldn’t in the email mailboxes. We need to do a better job at data governance and controlling where we store and allow sensitive data. This is where new tools like Abnormal Security come into play in a big way, rather than trying to change decades old habits, use new tech to your advantage and secure PII sitting in mailboxes at scale.
3. Australian Telecom Giant Optus Suffers Hack
In a recent press release from Australian Telecom giant, Optus, they confirm that they suffered a cybersecurity incident and data breach. Kelly Bayer Rosmarin, Optus CEO, had this to say about the attack, “We are devastated to discover that we have been subject to a cyberattack that has resulted in the disclosure of our customers’ personal information to someone who shouldn’t see it.” The press release did note that a good bit of sensitive customer data was exposed in the attack, they noted the following data types were included: customers’ names, dates of birth, phone numbers, email addresses, and, for a subset of customers, addresses, ID document numbers such as driver's license or passport numbers.
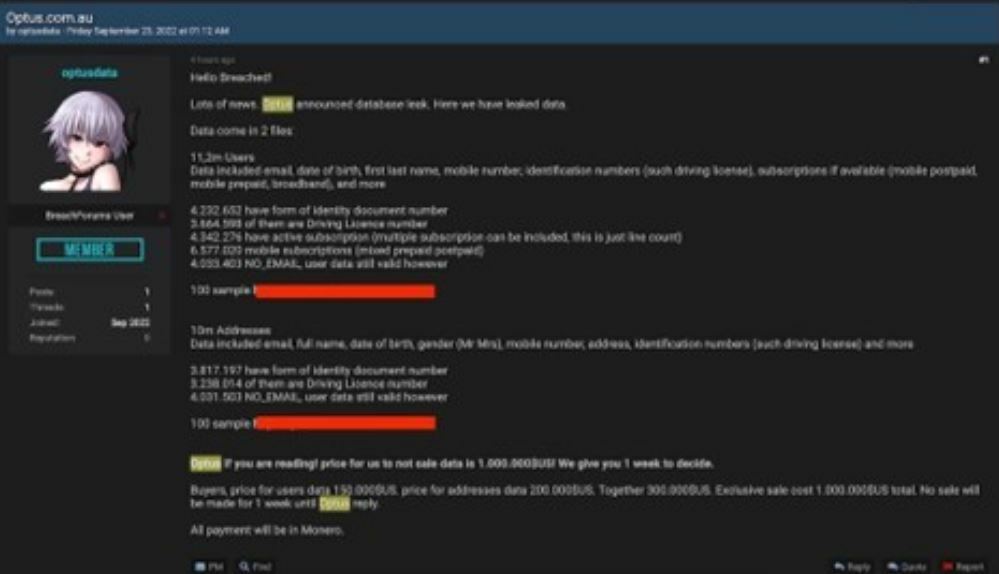
Image Source: https://www.bankinfosecurity.com/optus-under-1-million-extortion-threat-in-data-breach-a-20142
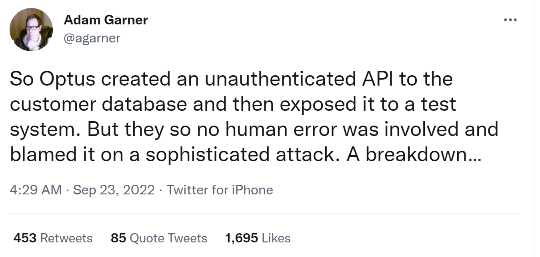
A report from ISMG group’s Jeremy Kirk shows that the hackers have published data samples on the dark web and are holding the data hostage for $1 million dollars in Monero cryptocurrency. The cause of the data breach was said to be an unauthenticated API (no authentication needed) that was connected to the internet through a test network that allowed for the initial access of Optus.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about
