Cyber Intelligence Weekly (April 7, 2024): Our Take on Three Things You Need to Know
Welcome to our weekly newsletter where we share some of the major developments on the future of cybersecurity that you need to know about. Make sure to follow my LinkedIn page as well as Echelon’s LinkedIn page to receive updates on the future of cybersecurity!
To receive these and other curated updates to your inbox on a regular basis, please sign up for our email list here: https://echeloncyber.com/ciw-subscribe
Before we get started on this week’s CIW, I’d like to highlight the various roles that we have open over here at Echelon! Please check out our LinkedIn page to see all the great roles and apply today!
We're also excited to announce the fourth installment of our "Chew On This" webinar series, where we'll tackle the intricate world of cybersecurity investment strategies tailored for diverse business portfolios!
Join us for this co-branded episode with Expel, where we'll uncover pivotal insights into effectively securing companies with multifaceted ventures.🎙️
Presented by Matt Donato, Partner at Echelon Risk + Cyber, and Paul Interval, Director of vCISO Services, we'll dissect critical questions surrounding cybersecurity integration within complex business structures. How should companies synchronize their cybersecurity efforts across diverse ventures?
Our distinguished guest, Greg Notch, CISO at Expel, brings extensive expertise in developing secure solutions to drive business strategy. As a seasoned information security and technology executive, Greg's insights will be invaluable in navigating the cybersecurity landscape for expanding portfolios.
🗓️ Save the Date: 📅 April 16th 🕑 12:00 - 12:45 PM ET
Don't miss out on this opportunity to gain practical strategies and perspectives to safeguard your business ventures against evolving cyber threats! Reserve your spot now and ensure your cybersecurity investment aligns with the dynamic needs of your expanding portfolio. Sign up here: https://www.linkedin.com/events/7178404402116898816/comments/

Solution Highlight - Keeper Password Manager

Echelon Risk + Cyber proudly cultivates a diverse network of strategic relationships with leading vendors in the cybersecurity industry. These collaborations empower Echelon to deliver premium services to our clients through cutting-edge technology and valuable insights. In our ongoing effort to bring top-shelf knowledge, each week, we want to spotlight a distinguished partner solution offered at Echelon. This week’s focus is on Keeper’s Password Manager.
Keeper's Password Manager provides a comprehensive solution for safeguarding passwords and confidential information with unmatched security, visibility, and control. Trusted by enterprises worldwide, Keeper offers robust protection against cyber threats, ensuring secure access to critical applications, systems, and IT resources.
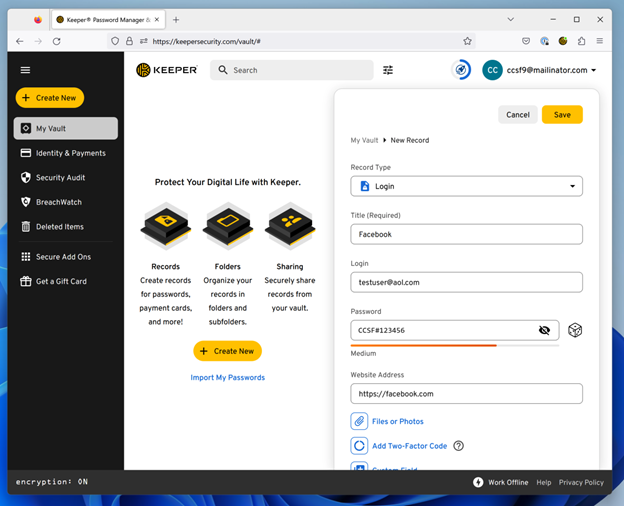
With Keeper, users can effortlessly generate strong passwords, securely store credentials, and seamlessly share them with authorized stakeholders. Its versatility spans various domains, including Password Management, Password Sharing, Secrets Management for DevOps, Privileged Session Management, and Remote Infrastructure Access.
Accessing Keeper is convenient and flexible, with options ranging from the Web Portal, Mobile Application, Desktop Application, to Chrome Extension. Rest assured, your sensitive data is shielded by Keeper's advanced security features, empowering you to navigate the digital landscape with confidence.
Enhance your protection with powerful add-ons:
- Secure File Storage: Safely store, manage, and share sensitive documents and files using Keeper’s Cloud Security Vault.
- BreachWatch: Gain live risk assessments of passwords directly within your vaults, empowering employees with real-time insights.
- Advanced Reporting & Alerts: Elevate standard reporting to fully customizable reports and alert functionality, all built on Keeper’s zero-knowledge security architecture.
- Compliance Reports: Monitor and report access permissions of privileged accounts across your organization with ease.
- Keeper Secrets Manager: Eliminate secrets sprawl by securely storing and managing hard-coded credentials within Keeper Secrets Manager.
- Professional Services: Access instant professional services, dedicated training, ongoing support, and tailored product configuration and implementation for various environments.
- KeeperChat: Ensure encrypted workplace communication with the highest level of privacy and secure messaging.
- Keeper Connection Manager: Gain instantaneous visibility into your infrastructure, providing DevOps and IT teams with instant access to servers, databases, RDP, SSH, Kubernetes infrastructure, and remote desktops through a web browser.
With the conclusion of the insight into Keeper’s Password Manager Solution, we look ahead with anticipation. Echelon Risk + Cyber remains dedicated to pushing the boundaries of cybersecurity innovation, forging partnerships that empower us to stay at the forefront of industry trends. If your organization is grappling with specific security challenges, allow Echelon to help alleviate the burden. Reach out to discuss how we might help your organization and stay tuned for more solution highlights in the weeks to come!
Away we go!
1. New Cyber Safety Review Board Critical of Microsoft’s Security Efforts
In a recent examination by a newly appointed Cyber Safety Review Board, a series of significant shortcomings in Microsoft's cybersecurity practices were brought to light, revealing a cascade of failures that facilitated a targeted hack by Chinese operatives. This meticulous scrutiny, initiated under the directive of President Biden, shed light on the technology giant's less-than-adequate cybersecurity measures, a culture of indifference towards stringent security protocols, and a noticeable reluctance to share critical information about security breaches. The incident in question, a sophisticated cyberattack that compromised the email accounts of prominent U.S. government officials, underscores a concerning vulnerability within Microsoft's widely utilized cloud infrastructure, prompting calls for a comprehensive overhaul in the company's approach to cybersecurity and transparency.
The independent board's findings underscored that the breach, which affected numerous organizations and individuals globally, could have been averted with more diligent security practices and risk management. Microsoft's acknowledgment of the need for a renewed focus on engineering security within its networks signifies a step towards addressing these deficiencies. However, the delay in correcting misleading public statements about the breach's origins and the technical lapses that allowed it to occur speaks to a broader issue of accountability and responsibility among tech behemoths. This incident serves as a critical reminder of the need for stringent security measures and transparent communication to safeguard digital infrastructure against increasingly sophisticated cyber threats.
This situation not only casts a shadow over Microsoft's security protocols but also signals a pivotal moment for the cloud computing industry at large. The recommendations issued by the review board advocate for a greater emphasis on security and openness within the sector, suggesting that the path to regaining public trust and ensuring the digital safety of governments, businesses, and individuals is fraught with challenges. The incident, while a stark wake-up call, presents an opportunity for Microsoft and its peers to lead by example, strengthening their defenses and fostering a culture of transparency and accountability that can withstand the evolving landscape of cyber threats.
2. Close Call, How the Linux XZ Backdoor Nearly Compromised Millions
The tech community has been buzzing with news of a sophisticated supply chain attack that nearly compromised the integrity of countless Linux systems worldwide. In an almost cinematic twist of fate, the attack centered around a well-timed insertion of a backdoor into XZ Utils, an essential data compression tool integral to Linux and other Unix-like operating systems. This breach, discovered thanks to the vigilance of Andres Freund, a Microsoft developer, highlighted the potential for significant security vulnerabilities within the open-source software ecosystem. Freund's discovery unveiled a meticulously planned effort to integrate malicious code into XZ Utils versions 5.6.0 and 5.6.1, aiming to manipulate the sshd process—a critical component for secure remote login sessions.
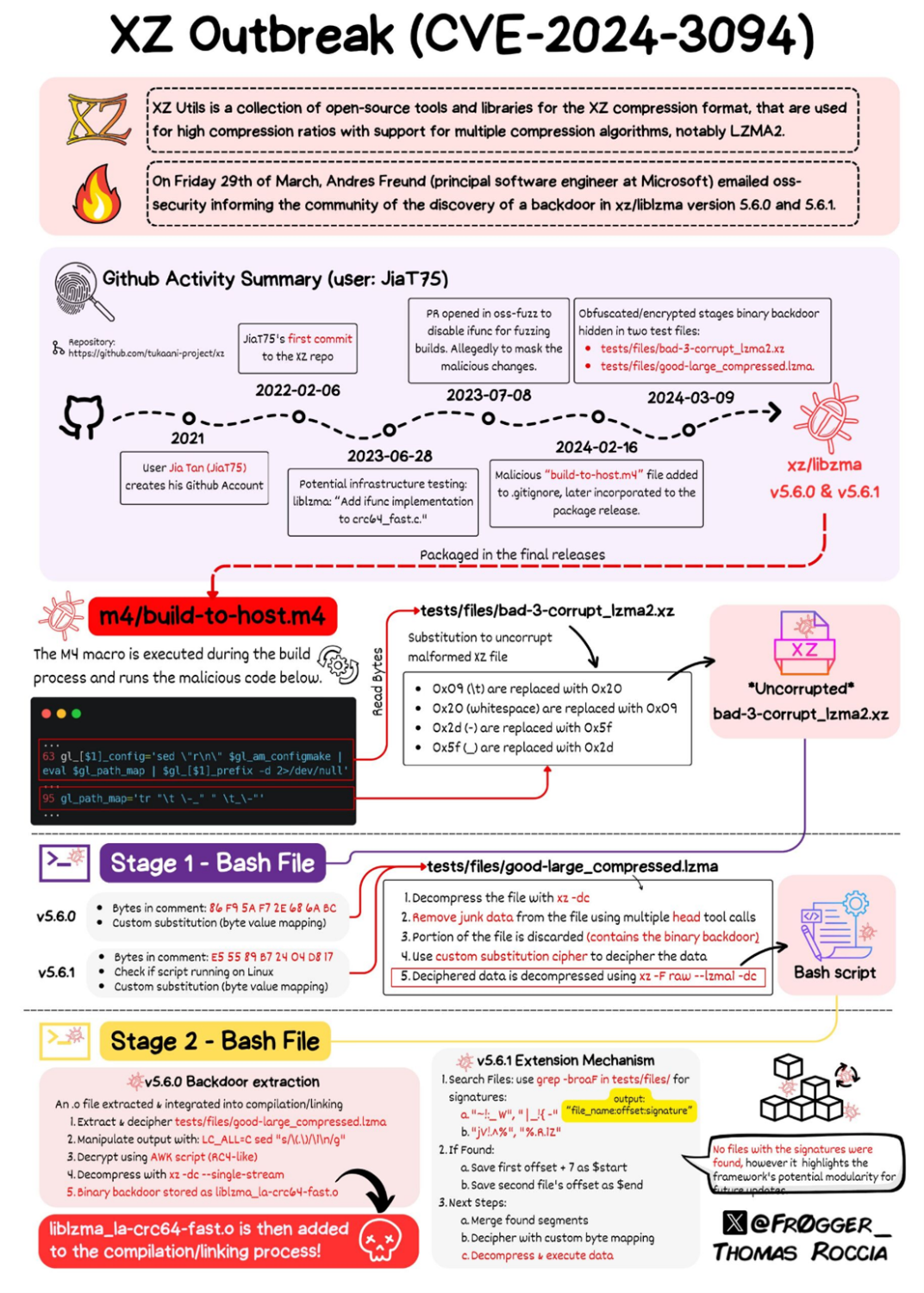
The complexity and audacity of this attempt cannot be overstated. By exploiting the interconnectedness of system libraries and processes, the perpetrators engineered a backdoor that could allow unauthorized execution of arbitrary code via SSH connections, under specific conditions. This backdoor, designed to be triggered only under certain circumstances to evade detection, represents a chilling escalation in the tactics employed by cyber attackers. The involvement of multiple fake identities to push the compromised versions into mainstream Linux distributions underscores the elaborate social engineering aspect of this attack.
What's particularly alarming is the strategic patience and long-term planning evident in this operation. Starting as early as 2021, the attackers began laying the groundwork, gradually building credibility within the open-source community before executing their plan. This incident serves as a stark reminder of the ever-present risks in the digital landscape, emphasizing the need for constant vigilance, thorough vetting of contributions to critical software components, and the importance of community-wide cooperation in maintaining the security and integrity of open-source ecosystems.
Deeper technical dive from our partners at CrowdStrike: https://www.crowdstrike.com/blog/cve-2024-3094-xz-upstream-supply-chain-attack/
3. Attempting to Unmask Jia Tan, The Architect Behind the XZ Utils Backdoor
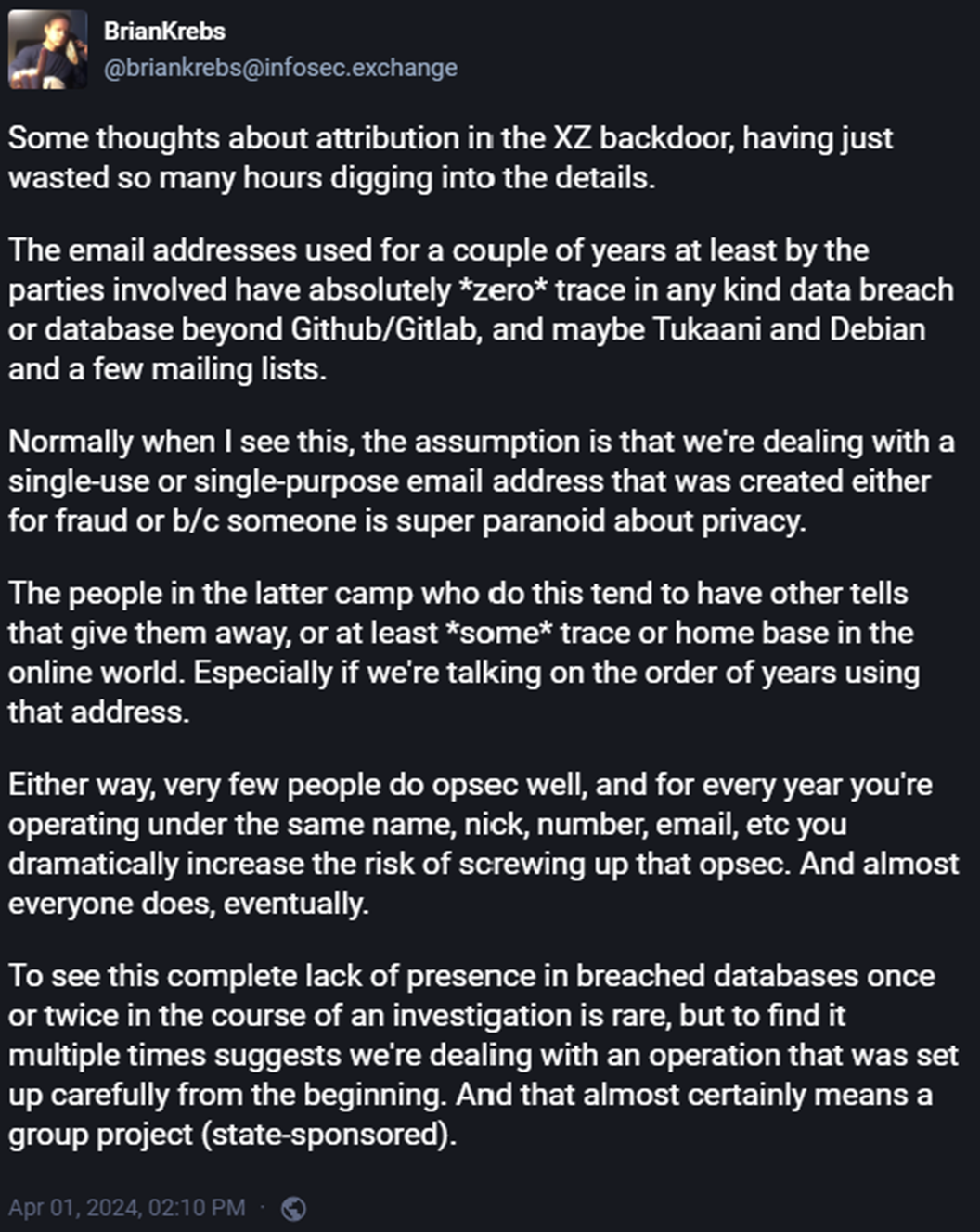
The cybersecurity world is still reeling from the above story and the revelation of a backdoor in XZ Utils, a critical compression utility used across various Linux distributions. This backdoor, discovered by Andres Freund, a Microsoft engineer, during an investigation into SSH performance issues, was traced back to a developer known as Jia Tan. This discovery has led to intense speculation about Jia Tan's true identity and the possibility that this persona is the front for a nation-state sponsored hacking group, given the sophisticated nature of the attack and the years of preparation involved. The methodical infiltration of the open-source project by Jia Tan, who first appeared in the coding community in 2021, involved contributions to multiple projects before taking a significant role in XZ Utils. This long con, culminating in the integration of a stealthy backdoor, underscores the strategic patience and technical prowess behind the operation, leading experts to believe in the involvement of a state-backed group with long-term cyber espionage objectives.
The meticulous execution of this supply chain attack reveals a deep understanding of open-source software's inner workings and the trust-based community that maintains it. By assuming control over the XZ Utils project and pushing a compromised version, Jia Tan nearly succeeded in embedding a tool that would allow remote command execution on millions of systems worldwide. The discovery of this backdoor before it could inflict widespread damage was fortuitous, highlighting the fragility of software supply chains and the constant vigilance required to protect them. The incident has prompted a reevaluation of the security measures surrounding open-source projects and the need for a more thorough vetting process for contributors.
The investigation into Jia Tan's identity and related activities has uncovered a web of deceit, including the use of a VPN to mask their location and meticulously planned interactions with the open-source community to build trust over several years. This operation's sophistication, along with the technical nuances of the backdoor, points to a carefully orchestrated campaign by a highly organized and possibly state-sponsored group. As the cybersecurity community continues to unravel the implications of this breach, the saga of Jia Tan serves as a cautionary tale about the potential vulnerabilities within even the most trusted software components and the ever-evolving threat landscape in cyberspace.
Thanks for reading!
About us: Echelon is a full-service cybersecurity consultancy that offers wholistic cybersecurity program building through vCISO or more specific solutions like penetration testing, red teaming, security engineering, cybersecurity compliance, and much more! Learn more about Echelon here: https://echeloncyber.com/about

