Hacker’s Perspective: Web App Vulnerabilities – Hacking GraphQL
Hacking GraphQL – A query language for your API, or an Entrance for Attackers?
GraphQL is a commonly used query language for manipulating APIs. It allows developers to construct requests that pull data from multiple sources in a single API call.
In its secured state, it is a useful tool for developing a successful web application. However, if configured improperly, it can have devastating results.
Attackers can use GraphQL to map an application’s hidden endpoints and retrieve sensitive information, and sometimes even to execute commands on the web server.
Why Does It Matter?
When pen testing a GraphQL API, the first thing we look for as attackers is if Introspection is enabled. Introspection allows an attacker to retrieve all available queries, types, fields and directives within the API.
Pictured below is an Introspection request:
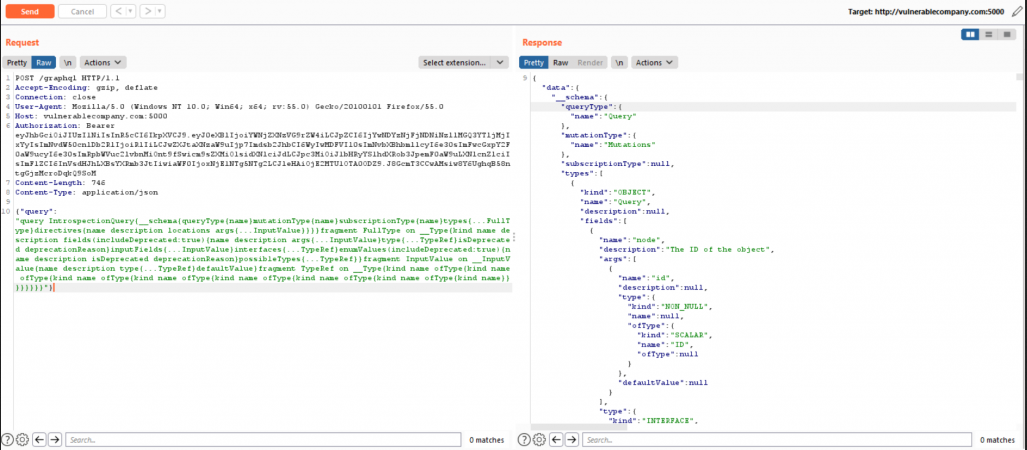
The image above shows that Introspection is enabled, as the request results in a server response containing the API schema. This response can be imported into the GraphQL Voyager application, where it can be represented graphically:
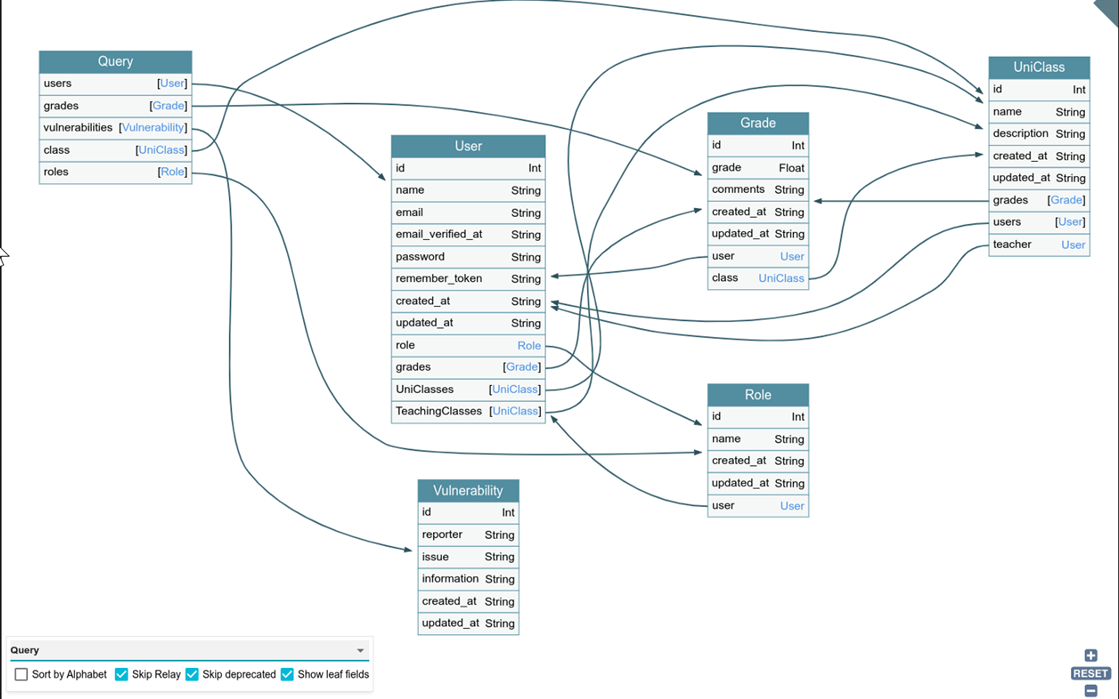
This information is extremely useful and can allow an attacker to go deeper within the application and access hidden endpoints that may reveal sensitive data.
Once an attacker is aware of the endpoint, they can attempt to query sensitive data from it, or update backend information. To make matters worse, Introspection is enabled by default in most implementations of GraphQL. However, even if an application has Introspection disabled it can still be vulnerable to attackers.
Using a tool like Clairvoyance (https://github.com/nikitastupin/clairvoyance), you can create the API schema through fuzzing. Once an attacker has the schema, the next step is discovering what can be done with it.
This is expounded upon in the photos below:
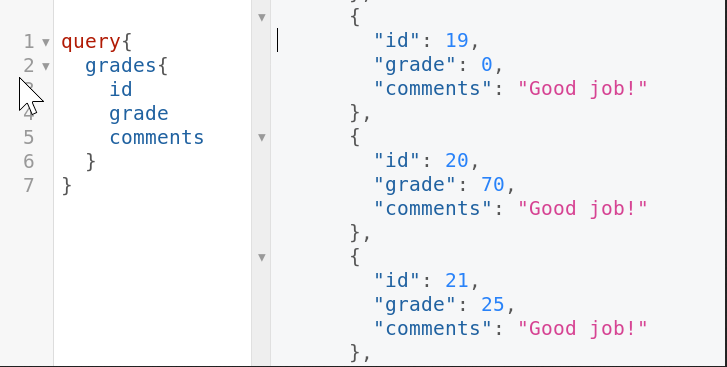
The query above shows an attacker querying the object ‘grades’ and retrieving student grades due to misconfigured authorization.
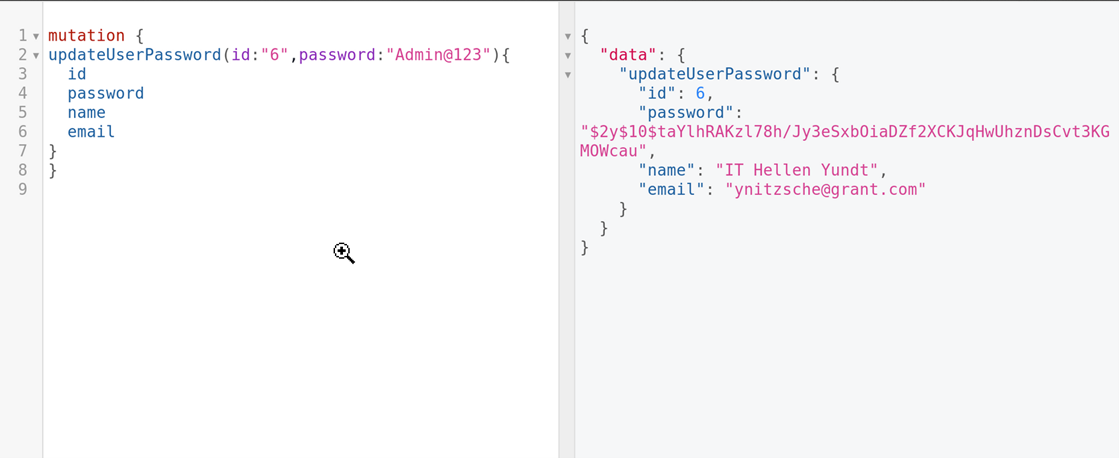
The mutation above shows an attacker updating a user password through a malicious mutation.
How Can You Fix It?
It is highly recommended to disable Introspection within GraphQL, as well as mask detailed errors. Additionally, you should make sure that proper access and authentication is set up surrounding your GraphQL operations.
We recommend every web application conduct an annual penetration test to ensure that GraphQL is properly set up, and that attackers have no way of gathering sensitive information from the API schema.
