Hackin’ SaaS – Echelon’s Top 10 Web App Vulnerabilities
At Echelon, our Offensive Security (OffSec) team of ethical hackers perform penetration test of web applications every day. In this article, we will cover the top 10 most common application security findings we discover within our penetration tests. These findings vulnerabilities range from detailed error messages to advanced SQL injections.
If you’d like to dive deep into these common vulnerabilities, please join our upcoming Hackin’ SaaS webinar series kicking off October 10th. Our hope in this webinar series is to shed light on the modern state of application security, assisting everyone from beginner penetration testers to senior-level managers on how to build more secure a web applications.
As part of the Hackin’ SaaS webinar series, we will be creating an intentionally vulnerable testing environment, and showing you how to both exploit and fix common web app vulnerabilities.
Top 10 Web App Vulnerabilities
Without further ado, here are Echelon’s top 10 most common web app findings that we will be discussing in the upcoming webinar series:
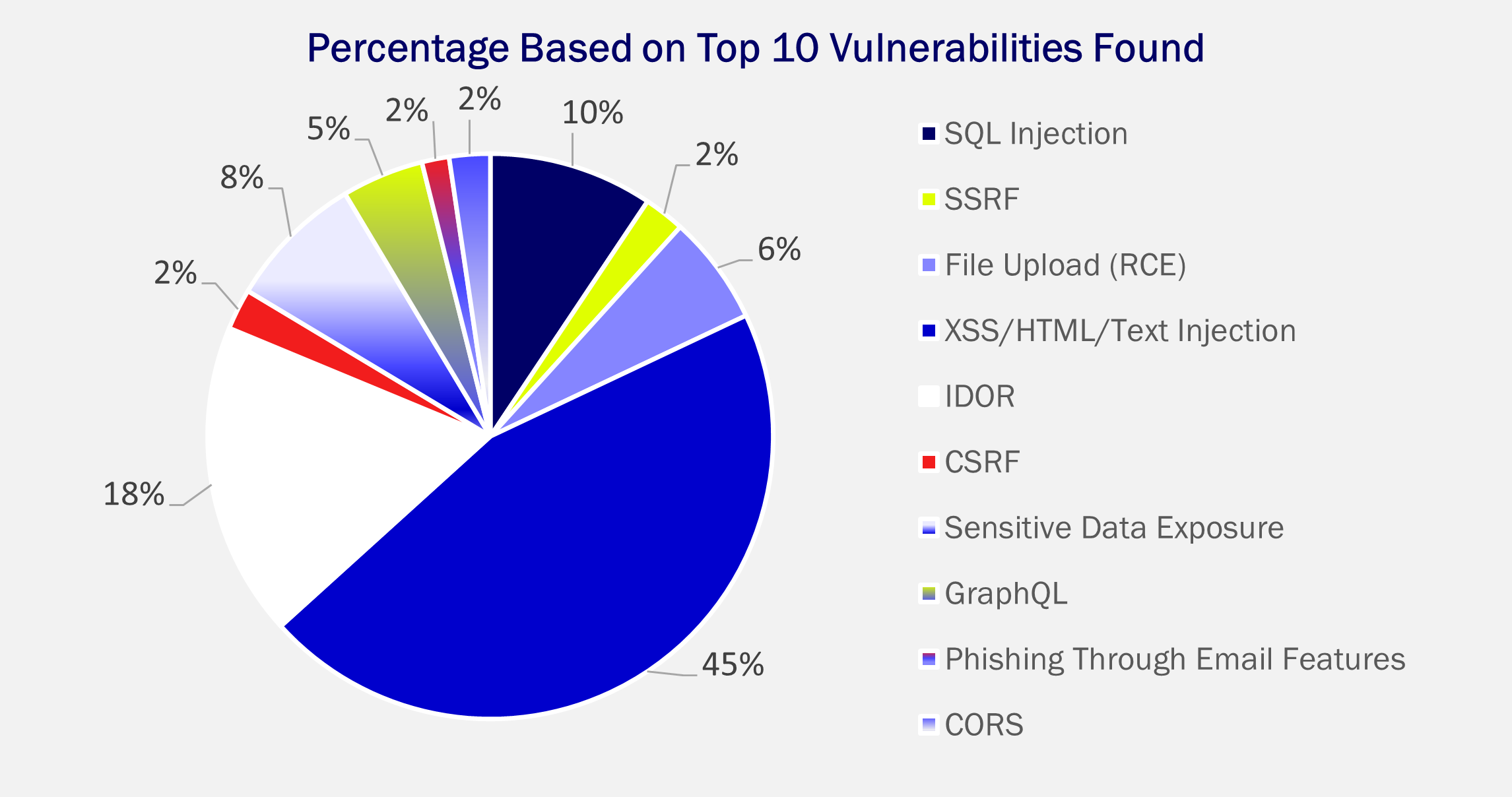
SQL injection
- Learn how to break into SQL statements through GET/POST parameters and execute queries on the back-end database. Once you learn how to break it, we will then teach you how to patch the server and prevent these sorts of attacks from occurring.
- Watch the webinar here
SSRF
- Understand the importance of whitelisting specific URLs being accessed by a GET/POST parameter. We will demonstrate how a threat actor can access internal ports and scan a network through an SSRF vulnerability. After, we will dive into the code and learn about how to remediate this vulnerability.
IDOR
- Learn the details of role-based access control, and how hackers can abuse your application by taking advantage of insecure endpoints/parameters.
Cross-Site Scripting & HTML Injections
- Understand how hackers can use Cross-Site Scripting for more than just an alert box – resulting in CSRF attacks or running a client-side keylogger.
File Upload Exploitation (Speak RCE)
- Learn how to find and exploit a file upload vulnerability with the potential for remote code execution. We will demonstrate how to abuse file extension restrictions through POST requests and upload various files containing reverse shells, web shells, and basic HTML. We will then explain how to mitigate these attacks.
Sensitive Data Exposure
- Understand how the data exposed by a web application can result in its exploitation – and how to prevent hackers from gaining access to your server through detailed error messages.
Phishing through Email Features
- Learn how to chain numerous vulnerabilities to achieve phishing through email sending features on a web application. We will be going through a few techniques to test and find this kind of vulnerability. After, we will analyze the server-side code to determine where the vulnerability occurs, and how to prevent it.
GraphQL Weaknesses
- Hacking GraphQL API’s can be a pain. In this webinar, we will go over how to access a GraphQL endpoint and enumerate all mutations and queries within the GraphQL API. After, we will dive into how to exploit and patch misconfigurations within GraphQL.
CSRF
- Understand the modern state of Cross-Site Request Forgery. Once demonstrated, we will delve into the cause of this vulnerability and discuss the importance of proper patching.
CORS Misconfigurations
- Learn how a simple CORS misconfiguration can result in a threat actor gaining access to sensitive information on the users of your platform.
Join our Hackin’ Saas Webinars!
At Echelon, we consistently discover these 10 vulnerabilities within our application security tests.
If you are interested in exploiting or patching these sorts of findings, we will be hosting a webinar on the second Tuesday of every other month.
Join our October webinar here!
Come learn the ins and outs of what it takes to keep your web application secure!


